
Featured Articles
Our 11 Favorite Stories from 2022
The Security Management editors write and collaborate on hundreds of stories each year. Here are 11 pieces they enjoyed most in 2022.
Hatejacked: How to Monitor for Co-Opted Messaging
As corporate messengers seek to use their messaging to distinguish their brand, it is also imperative that organizations are mindful of—and take active precautions against—the misuse of the brand by potential adversaries, extremists, and opportunists seeking to co-opt elements of their messaging.

Our 9 Favorite Illustrations of 2022
The Security Management design team has the momentous challenge of visually bringing our complex stories to life. Here are 9 designs that were their favorite to collaborate on in 2022.

How to Identify Forced Labor in Your Supply Chain
The European Union (EU) and the United States, among other jurisdictions, have tough laws in place to deter exploitative practices, but forced labor persists. A sound risk management strategy is a strong first step employers can take to help prevent exploitative practices.

Our 12 Most-Read Stories of 2022
The Security Management editorial team and contributing authors wrote hundreds of articles in 2022. Here are the 12 that readers kept returning to throughout the year.
How to Train Healthcare Teams to Detect and Support Human Trafficking Victims
Healthcare organizations and their employees often fail to identify when a patient is a victim of human trafficking. Perhaps worse is when someone spots a red flag but doesn’t know how to respond.

Infographic: Trauma-Informed Approach
The core principles of trauma-informed approach can be applied to healthcare organizations’ programs in identifying, approaching, and supporting victims of human trafficking.

Phoenix Children’s Hospital Applies a Multi-Disciplined Approach to Pediatric Protection
The security team for the Phoenix Children’s Hospital in Phoenix, Arizona, applies education and communication to protect its staff and patients.

Modern-Day Slavery: Fact Versus Fiction
There are several myths surrounding human trafficking. Here are some of the facts and the stats.

Serious Fun: Using Social Media to Entertainingly Educate
How do you get millions of people to pay attention to safety information? Mastering memes can help, according to the strategist behind the U.S. Consumer Product Safety Commission’s Twitter account.

Fast Facts: 6 Factors to Assess Before Leaving Twitter
Know these six factors before deleting your social media account
Legal Report: Google Settles to End Privacy Investigation
Google agreed to a $391.5 million settlement with 40 U.S. states over violations of location tracking of users.
Nine Security Social Media Accounts that are Making a Mark
When it comes to security awareness, a little humor goes a long way. Security Management collected a list of some of our favorite security social media accounts and movements that are hitting the mark and inspiring new energy in the industry.

Where Did You Read That? U.S. Adults Turn to Social Media for News
Half of U.S. adults now get their news from social media sites. But depending on their political views, they are seeking out different sites to share and engage with content—potentially contributing to increased political polarization.
Healthcare NGO Partners for Risk Management Assistance
Orbis International, a global, non-governmental organization (NGO) that treats avoidable blindness, teamed up with ADT Commercial to gain advice on how to scale and manage systems to address safety and security concerns.

How to Plan Out Your Workplace Investigation Interviews
Before you launch a workplace investigation, take the time to plan out how you will conduct your interviews. They will lay the groundwork for everything that will follow.

Unravelling the Complexities of Healthcare Access Control
Two healthcare facility experts offer insights into how to manage the complexities of hospital access control systems.

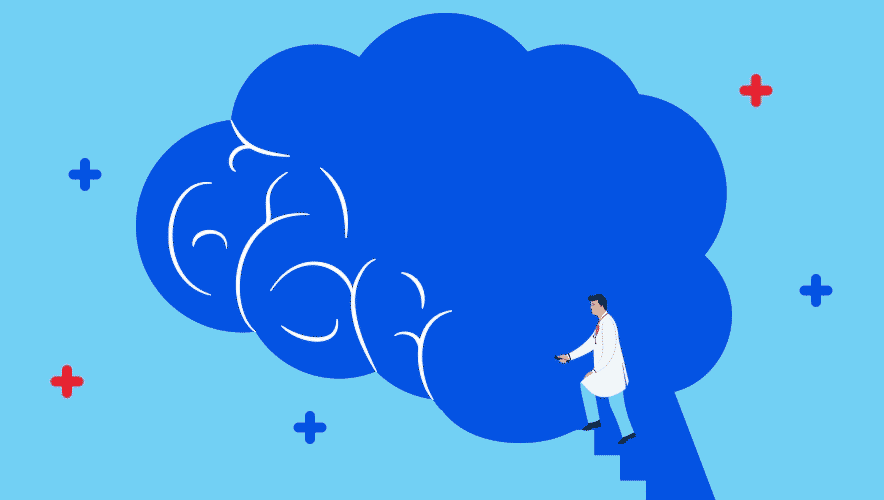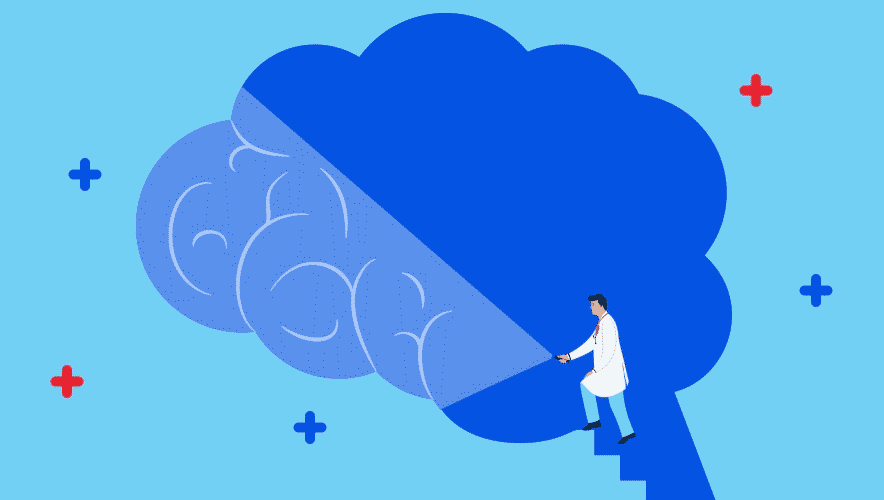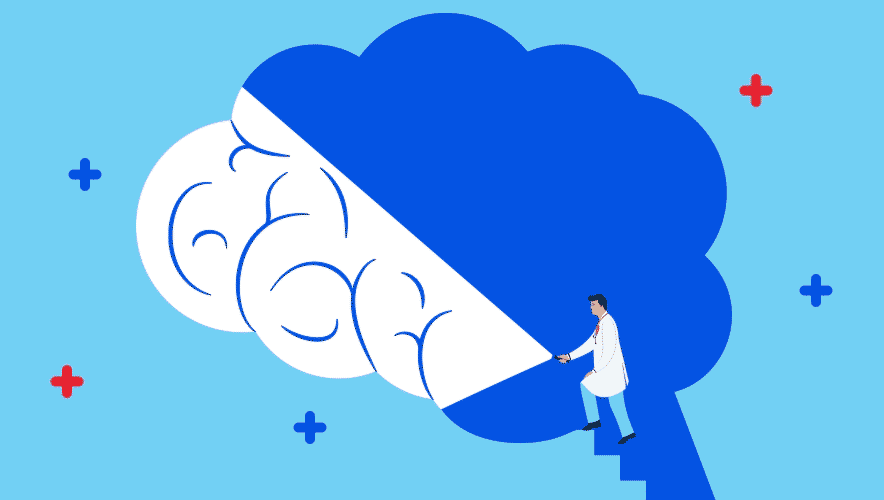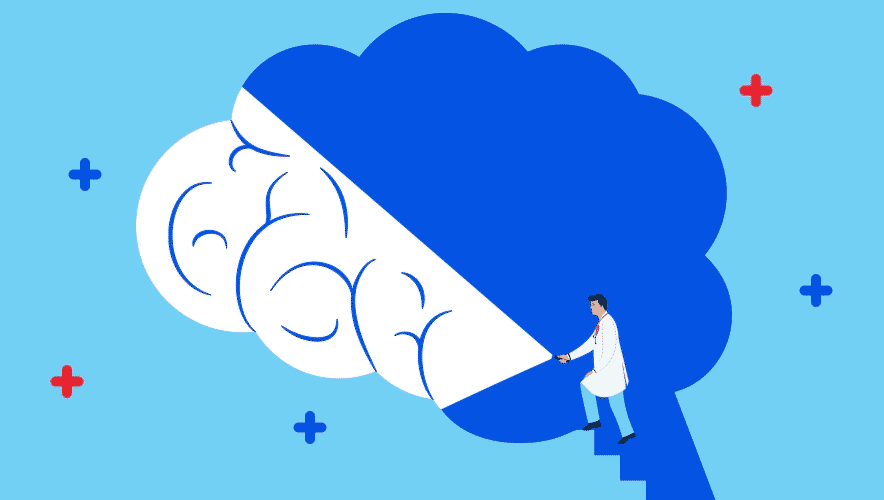
The Security Professional’s Guide to the Brain
How you think determines how you act. Knowing more about the nervous system can help security professionals de-escalate situations, craft stronger education initiatives, and improve decision making.
How a Virginia City Built an Effective Volunteer Security Reserve Program
Security organizations are being forced to compete in a shrinking labor market for personnel who must take on greater responsibilities in a dynamic risk environment. One city’s security team turned to an underutilized resource to fill in the gaps: floor wardens.

The 5 Scariest Hacker Groups of 2022
In cyberspace, no one can hear you scream—unless you follow these dynamic cyber defense strategies.

How Political Affiliation Bias Heightens Workplace Tensions
Almost a quarter of the 504 workers surveyed by SHRM in late August (24 percent) say they have personally experienced differential treatment, either positive or negative, because of their political views, compared with 12 percent of U.S workers in 2019.
Treating Trauma
Today, there’s more awareness than ever of the trauma that first responders and security practitioners experience while on the job. But we’re only beginning to understand how to treat it and remove the stigma associated with seeking care.

How to Minimize Harm in Active Shooter Responses
Identifying the best strategy to survive an active shooter incident amid chaos can be tough, with indecision possibly incapacitating stakeholders and putting employees’ lives in imminent danger.

The Need for a Multidimensional Active Shooter Response
The complexity and high-risk scale of active shooter situations warrant a multidimensional response that can be applied across locations universally.

How to Put Multidimensional Active Shooter Response into Practice
Many organizations still don’t have an active shooter response plan in place, and even fewer have trained their employees on what to do. This is a huge mistake.
How Alternative Credentials Can Help You Find Employees
If organizations expand their candidate search methods beyond the traditional bachelor’s or associate degrees, they will find a throng of candidates with the skills they need, earned through unconventional means. This will be a boon not only for those individuals, but also for the companies they serve.
3 Benefits of Alternative Credentials
“Skill-based hiring reduces barriers to entry that disproportionately affect minority workers,” says Kate Markin Coleman, co-author of Growing Fairly: How to Build Opportunity and Equity in Workforce Development.

Staffing Security While Restocking the Talent Pool
Just as a business might call on a temp agency, security teams are tapping into off-duty police officers to fill the bench until the security workforce rebounds.

How Educational Institutions Can Help Fill the Cybersecurity Workforce Gap
Educational institutions can help fill the deficit in national cybersecurity capacity. One way this can be accomplished is by bridging the gap between STEM and non-STEM disciplines through the creation of educational programs that provide essential technical cybersecurity-related knowledge, skills, and abilities.
Amid Remote Work, Romance and Risk Persist
Even during a period of remote and hybrid work, office romance is on the rise. So, it’s essential to have a policy and best practices in place.
6 Ways Environmental, Social, and Governance Principles Influence Security
What started as investor terminology to measure environmental and worker relations transparency has drifted into something quite different: environmental, social, and governance (ESG) is now synonymous with creating the most sustainable, socially conscious, and progressive brand possible.

Consider Special Discretion for LGBTQ Workplace Romance Disclosures
Legally, companies can’t have different rules for LGBTQ employees than they do for employees who do not identify as LGBTQ.
Infographic: Workplace Dating Data
Even though many employees are working remotely, workplace romances are on the rise—6 percent more workers reported being involved in a workplace romance in 2022 compared to 2019, according to a January 2022 survey of 550 U.S. employees.

Establishing a Good First Impression for Healthcare Security
Whether a person likes and trusts a healthcare institution or not can have consequences for their care and their behavior.
Video: Top Targeted Items for Retail Crime
Inflation is high, and it’s driving retail theft higher. Organized retail crime groups are perusing grocery store shelves to steal easily resold items, which could have heavy ramifications for stores’ bottom lines.

In Danger: Managing Risks to Cultural Properties in Latin America
Seven Latin American countries have World Heritage Sites that are on the in danger list. These are some basic security steps that could help protect them.

Protests and Paintings: How Museums Can Prepare for Demonstrations
Protests at cultural properties are nothing new. But a recent trend of environmental protestors gluing themselves to artwork is. Here are some best practices to prepare your institution to respond.

Behind the Façade: Negligent Security and Premises Liability
Jurors expect landlords and property management companies to exercise a reasonable standard of care in protecting tenants from violent crime. The law demands it.

Ready, Stress, Go! Why Active Shooter Training Fails
The purpose of training is to inspire a sense of confidence and competence where knowledge and skill are otherwise wanting. Training that leaves participants terrorized, anxious, and bruised fails the foundational ideal that makes it meaningful.

Hunting for Profits, Criminal Groups Turn to the Environment
In the European Union alone, the profits of some criminal networks involved in environmental crimes—from trafficking protected wild animals to waste and pollution crimes—reach millions of euros every year.

Video: How Organized Crime and Terrorism Leverages Wildlife Trafficking
Illegal wildlife trafficking is the fourth most profitable illicit activity in the world, behind only narcotics, human trafficking, and counterfeiting.

Meet Gen Z: The Stressed, Indebted, and Idealistic Future of Work
College debt, inflation, racial and gender inequity, political upheaval, the lingering effects of the COVID-19 pandemic, and recession fears plague Generation Z, so it’s no wonder that many of them say they’re facing mental health issues.

How the U.S. Army Is Changing Its Recruitment Strategy for Gen Z
Nearly three-quarters of Generation Z people recently surveyed claimed to be familiar with the Army—the highest amount of any generation. But it turned out they weren’t well-informed.

Four Smart Cybersecurity Investments for CISOs to Bridge the Talent Shortage
The most effective security leaders maximize their investments in talent, technologies, and services to address the cybersecurity talent shortage.

Active Threat Attacks by Lone Actors: A New Category of Risk to Anticipate for Effective Prevention
A recent wave of violent attackers crosses traditional active assailant categories, vastly complicating traditional threat assessment practices.

Why Zero Trust Must Extend into Deep Infrastructure
Serious, persistent threats are already looming in your infrastructure. The lowest-hanging fruit—and the most vulnerable point of attack—is where you may least expect it: the hardware and firmware that lies in the deep layers of your physical infrastructure.

How to Get Real Results with Virtual Training
Virtual reality isn’t typically used to hone soft skills such as improving leadership or communication, though more companies are considering it. Instead, it’s a conduit to developing physical skills like repairing a piece of equipment or learning the most effective way to stack boxes in a warehouse.

Building Your Personal Brand Through ASIS Certification and Networking
"Trust is the key to being a successful CSO. I must continuously cultivate my brand to demonstrate that I am a trustworthy person who has the experience and expertise to guide my company through a maze of security risks," writes Scott Wolford, CPP. "This is achieved by building a system that consistently communicates my values, skills, and personality."

Influencers and Abusers: Keeping Online Celebrities Safe
To learn more about how security practitioners can respond to online threats and protect influencers—from social media to basketball stars—Security Management interviewed a risk expert.
Infographic: The Latest Cyber Target: Manufacturing
Manufacturers face an increase in cybersecurity threats which can threaten sensitive data and disrupt production.

Remote Viewing to Support Lone Workers and Facilities
When colocation data center provider Flexential looked for a way to support their lone workers, it went back to what was familiar and what would support a complex regulatory environment.
Collateral Damage: Cartel Activity Spills Over into Tourist Resorts
Although Mexico’s famous tourism hub Cancún has been in the spotlight lately for violent incidents, its crime rates are still significantly lower than many U.S. cities.

Crime Prevention Travel Tips in Mexico
Cancun remains one of the safest locations for tourists and travelers in Mexico, but recent incidents reinforce the message that violence can happen anywhere, and cartel activity can spill over and threaten bystanders.

Timeline: Increased Violence in Mexican Tourism Districts
Cancun remains one of the safest locations for tourists and travelers in Mexico, but recent incidents reinforce the message that violence can happen anywhere, and cartel activity can spill over and threaten bystanders.
How to Build a Best-in-Class Security Culture
Building a sustained security culture starts with the security leader’s ability to emotionally connect, engage, and partner with people at all levels of the organization, from the C-suite to the third-shift frontline associate.
Could It Happen Here? Assessing Cyber Defenses After an Outside Breach
A hacker breached a video surveillance provider, gaining access to its systems to view live footage of client sites. The incident prompted security companies to reassess their own authentication and segmentation practices to prevent a similar hack.

4 Stages to Plot Your Personal Branding Pathway
Executive branding expert Lida Citroën shares insight on how to craft your brand with authenticity and credibility for future success.

7 Tips to Verify Your Social Media Connections
Social media messaging platforms are even more effective than email in landing a spearphishing campaign, says Peter Warmka, founder of the Counterintelligence Institute.
How to Develop an Effective Succession Plan in Uncertain Times
Many organizations don’t think about succession planning until someone retires or dies. But in an increasingly volatile job market, that's an untenable strategy.

Infographic: Why Organizations Don't Have Succession Plans
In a 2021 survey, 36 percent of HR professionals said they had no succession planning program in place.

6 Common Blunders in Succession Planning
The biggest mistake in succession planning is the failure to plan at all, but for those implementing succession planning processes, there are a few other pitfalls to watch for.

Infographic: Security Decision-Making and the Value of Information
Security professionals’ relationship with information is complicated, especially where risk management decisions are concerned.

Exploit: The Forgotten Fifth Option of Risk Management
Security professionals often view risk only in negative terms, and they are taught there are four commonly accepted options for treating risk: accept it, avoid it, manage it, or share it. However, there is a fifth option that is often overlooked but can be very positive to those who understand it: exploit it.

5 Steps to Personal Branding Success
Ready to take control of your professional reputation? It requires intention, dedication, and diligence to keep your message on track, and it’s a skill that CSOs need to be particularly adept at.
Infographic: Risks in the Great Resignation
Port operators and shipping companies are getting back to full capacity after widespread resignations, but is the new workforce skilled enough and sufficiently trustworthy to keep shipments flowing safely?
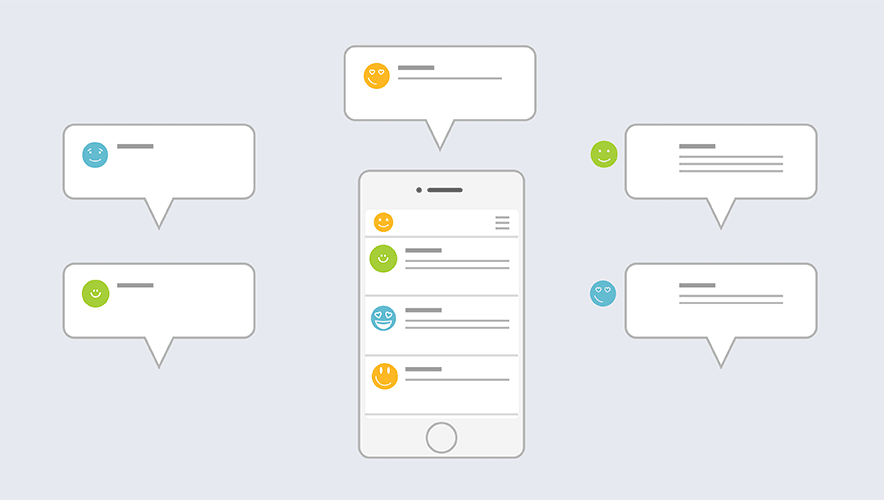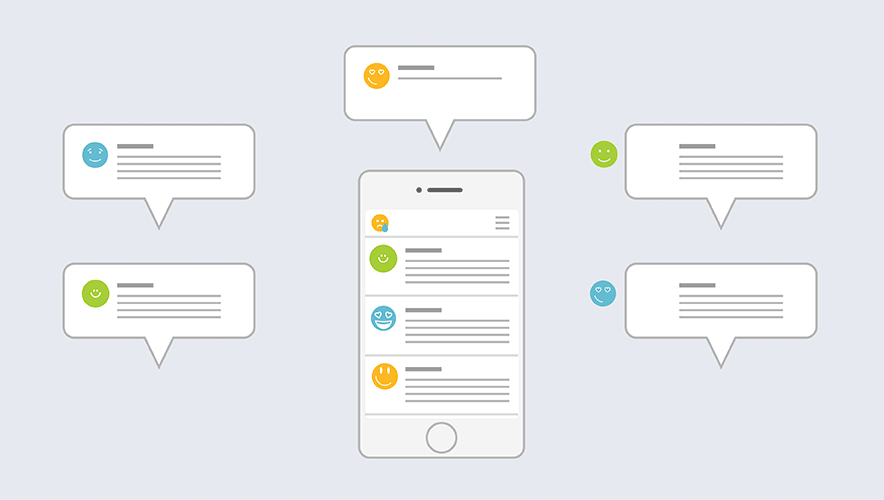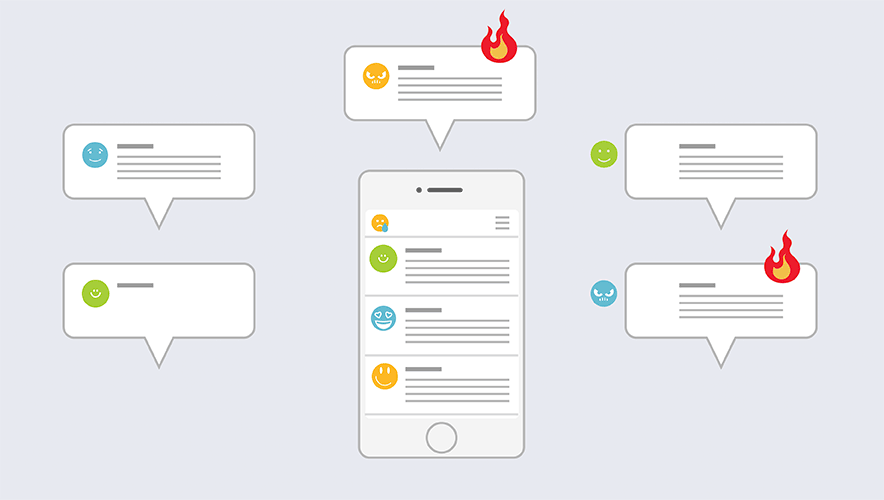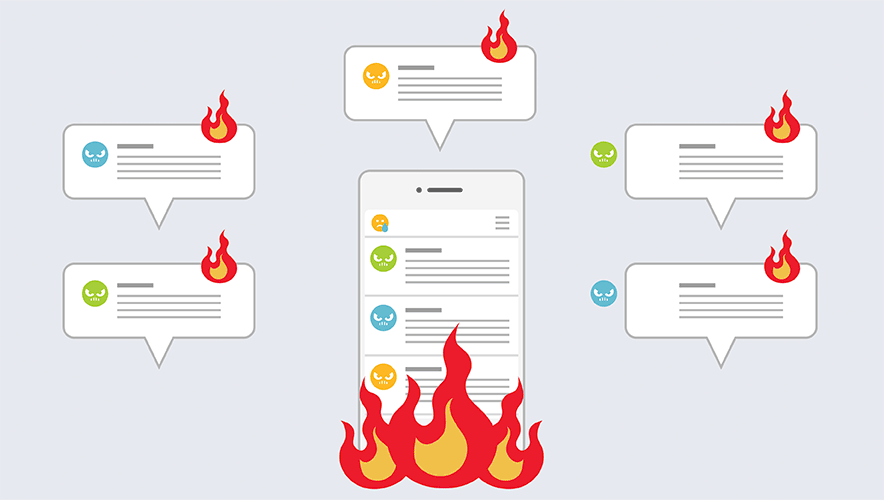
When Personal Branding Becomes Personal Risk
As security professionals launch and cultivate their personal brands on public-facing channels such as social media, they can draw attention to themselves. While increasing security’s profile is not necessarily a bad thing, understanding the risks and challenges is essential.

Infographic: The Essential Elements of CPTED
These tips will help you implement natural and low-impact security measures using landscaping, signage, and workplace culture.

War in Ukraine Heightens Refugee Trafficking Awareness and Prevention
Most refugees are women, children, and elderly people. Without means of subsistence in a situation of political, economic, social instability, these refugees often become a target for traffickers.

Managing Security Operations in Regions Outside the Rule of Law
For organizations seeking to manage risk and security operations in tenuous circumstances—including in countries or regions where there is conflict or where the rule of law has been undermined—a little guidance is more than welcome.

How a People-First Hybrid Strategy is Essential for Retention During the Great Resignation
What approach can companies take to keep their staff from joining the millions of Great Resignees? To put it simply: implement a people-first mind-set within your hybrid business model.

6 Tips for Employers on Conducting Background Checks
Background checks are a critical tool for employers to help avoid liability for negligent hiring—but navigating myriad U.S. federal, state, and local laws that govern such investigations can be a difficult task.

How to Build and Maintain a Personal Brand
“Branding doesn't mean boasting, but it means being really clear about who you are, who you want to serve, and how you want people to experience you,” says Lida Citroën, a personal branding expert and a 2022 CSO Center Leadership Series speaker.

Inside the Investigation: The NTSB’s Culture of Transparency and Integrity
The U.S. National Transportation Safety Board conducts thousands of investigations each year to understand why crashes happen. The process it uses to collect evidence, analyze material, and share recommendations with stakeholders provides best practices for private investigators on the job.

Wearable Solution Helps Security Factory Buffer Against COVID-19
ASSA ABLOY Opening Solutions America implemented a Bluzone fob system to prevent its factories and distribution facilities from shutting down while protecting staff from infection.

Leaders Conduct Risk Assessments: Security and Safety at Festivals and Outdoor Events
Major outdoor festivals and concerts require a comprehensive, holistic, and layered approach to security and safety that includes the inclusion of internal and external stakeholders. This process should start with a threat, vulnerability, and risk assessment.

Human Trafficking in Casinos: The Ghost Crime Operating in Plain Sight
Human trafficking, frequently referred to as a ghost crime, occurs in plain sight within casino and resort properties, but it remains largely unseen because the indicators of this crime are invisible to most.

Lessons from the War in Ukraine: Commercial Drones Used for Combat
Security professionals across the globe should be taking note of the creative uses of recreational drones in Ukraine because nefarious actors certainly are.

Public Access Bleeding Control and the Standard of Care: A Rising Tide Lifts All Boats
Is there a general duty to provide first aid? As is often the case, the answer is “it depends.”

In the Great Resignation, Engage to Retain
With near record-high job openings, engage your employees to ensure you don’t lose them to a costly turnover tsunami.

Building the Foundation of Effective Communication: Trust
To get out of a crisis, any crisis, we need to focus on building unity through purposeful communication, ethical reciprocity, and authentic trust-building efforts with our stakeholders.

Protection of Assets: Developing Effective Crisis Communications Plans
Crisis communications is focused on not only communicating messages regarding a disruptive event but also on broader issues that support the organizational resilience, survival of the organization’s business model, and future strategic business plans.
Greet, Pray, Love
Houses of worship must turn to different types of training to protect their flocks. One synagogue shifted to a non-confrontational crisis response exercise.

Infographic: The Payout Problem
Ransomware thrives as organizations remain vulnerable and continue to pay criminals.

Career Advice: Mind Your Skill Gaps
As young professionals build up their experience within security, it can be easy to miss some essential areas that CSOs look for in their successors. Here, two members of the ASIS CSO Center share career advice and professional development tips.

Career Advice: What Young Professionals Bring to the Table
Early-career security professionals bring unique and valuable perspective to organizations, but their soft skills often outweigh their subject matter expertise. Two ASIS Young Professional leaders share advice on how to rebalance.

Meet the Latest Players in Industrial Control System Cyber Intrusions
New threat actors emerge on the scene to target industrial control systems and operational technology networks around the world, often with little insight into their activities until an incident occurs.

The Milestones in the Marathon
Being a security leader can feel like an unending race, but establishing personal and professional finish lines to mark accomplishments and demonstrate progress can reinvigorate both managers and their departments.
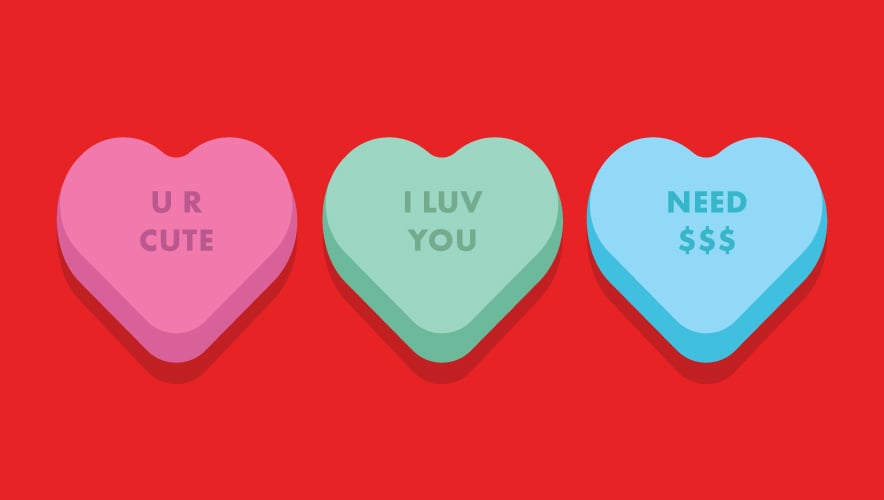
Targeting All Lonely Hearts
Romance scams are easier than ever through social media and online dating, and the schemes can be very profitable for fraudsters.

Unraveling the OSINT Oxymoron
There is almost infinite data freely available, and yet, it is so often ignored because of its sheer size and complexity. So, how can security professionals sift through the information to detect fraud?

How to Succeed When Shifting from Individual Contributor to New Manager
If you’re a new manager and are feeling overwhelmed, here’s some good news: There are immediate steps you can take to acclimate yourself to a leadership role.
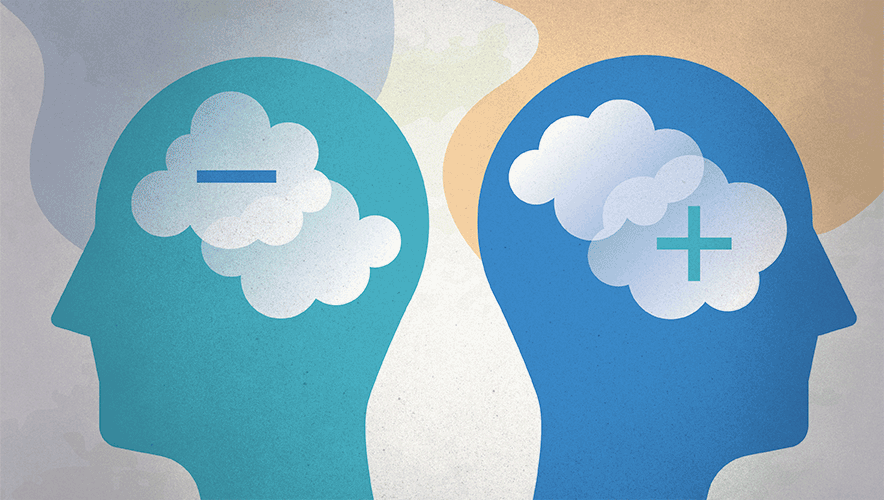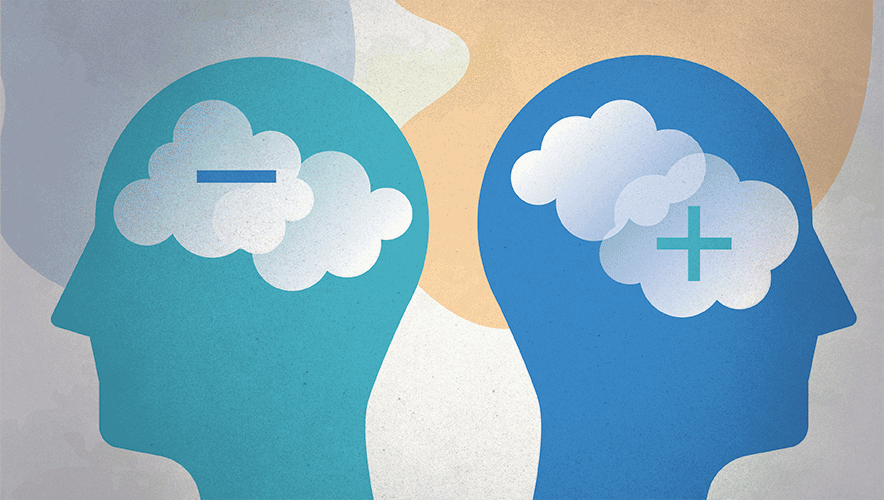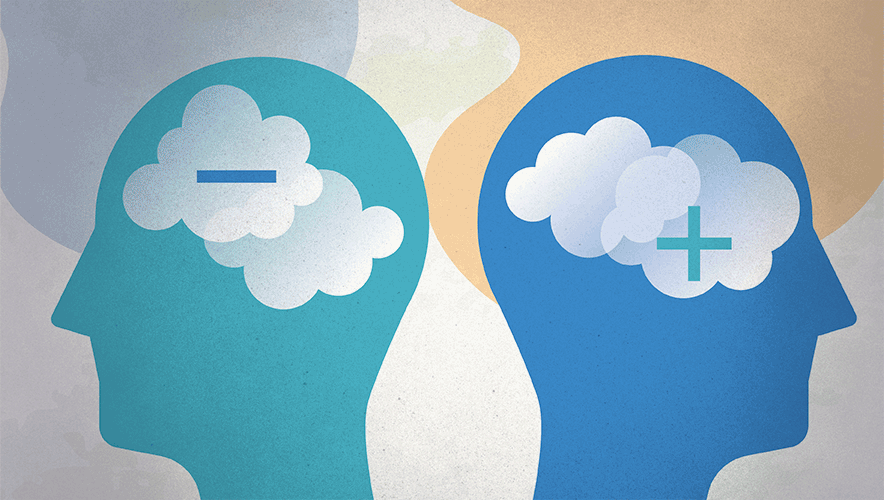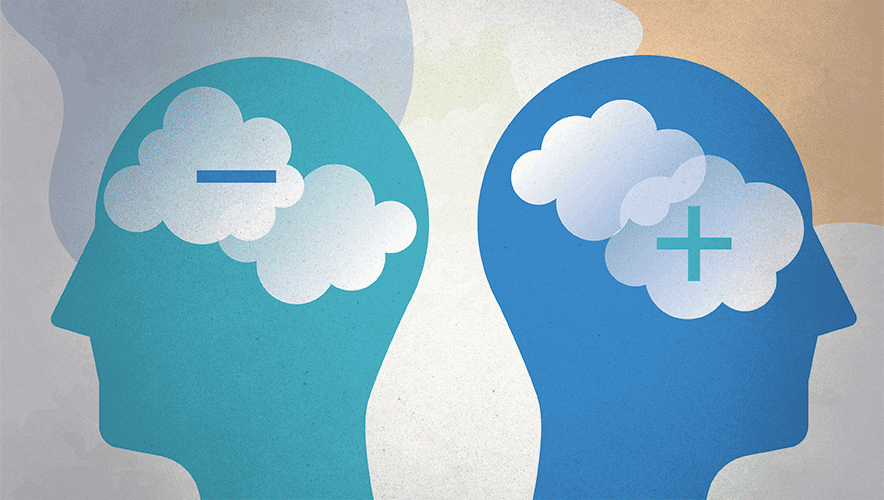
Three Security Disconnects that Fall Through the Cracks
In strengthening one’s organization to withstand the challenges of tomorrow, it is critical to focus on the three most common disconnects taking place today, primarily around standardization, personnel, and system maintenance.

Five Tools to Drive Cyber Success
Understanding how policies, procedures, and tools impact your security posture is critical. A new report helps shed light on what’s working, what’s not, and how security leaders can adopt best practices with C-suite engagement.

New CISA Directive Reiterates Need for Cyber Modernization
U.S. agencies will lean on their private sector mission partners to continue to assess and resolve risks as they arise—and the government contracting community must take similar steps.

Addressing Mail-Borne Threats at Remote and Traditional Offices
In the last three years, the U.S. Postal Inspection Service and the U.S. Bureau of Alcohol, Tobacco, Firearms, and Explosives responded to an average of more than 10 dangerous mail or package incidents per day.
Leveraging the GSOC During COVID-19
At industrial gas company Air Products, the global security operations center continues to play a critical role and add value for the organization and its stakeholders during the COVID-19 pandemic.

The Bull and Millionaire Mike: A Look at Darknet and Securities Fraud
Criminals have long leveraged information and communications technology to commit crimes. They are now using these tactics to engage in insider trading on the Dark Web.

A Society of Belonging: An Interview with Malcolm Smith, CPP
Incoming ASIS President Malcolm Smith, CPP, takes the helm with inclusion and community as his top priorities.

In Case of Crisis, Build Community
In the face of natural disasters increasing in both frequency and ferocity, when the lights go out businesses should look to a nearby network of neighbors to get back up and running faster.

Robbed in a Flash: Assessing Risk for Mass Smash and Grab Incidents
Flash robberies have been reported since the early 1990s, but recent high-profile thefts in the United States demonstrate that the method is alive and well. What brought them back, and how can retailers prepare to respond?

Q&A: How Retail Security Professionals Can Mitigate Brazen Burglary Risks
Highly publicized flash robs are only a small portion of organized retail crime (ORC) thefts, though overall, loss and damage from ORC is on the rise.

Assessing the Use of Edged Weapons in Terrorist Attacks
Firearms and improvised explosive devices take time to acquire and finesse to operate. These factors may be encouraging attackers to turn to more easily obtainable weapons, like knives, to inflict harm.

Overcoming Five Preventive Intelligence Hurdles
A modern enterprise's products and services increasingly exist online or in software code. Corporate assets are increasingly digital assets. This shift calls for the implementation of preventive intelligence, an approach that spans the online and physical worlds.

Best Practices for Dealing with Aging Power Infrastructure
Despite federal commitment to upgrade U.S. electrical grid, businesses and homeowners must still protect equipment from power surges.

Restructuring School Security Planning and Awareness
Before the COVID-19 pandemic, schools were typically very regimented about the main entrance security of their buildings. Security assessments conducted during the pandemic, by contrast, illustrated a very relaxed main entrance security posture.

Cloud in the Crosshairs
Organizations are increasingly embracing opportunities to leverage the cloud, which can create security risks if vulnerabilities are left unaddressed.

Turning Bad Apples Good: Using Soft Skills for Threat Assessment
In cases where an individual’s values clash with the organization’s, negative emotions—sadness, frustration, anger—can result in inappropriate behaviors and choices.

The Tao of Taleb: Learning from COVID-19
As COVID-19 approaches its two-year anniversary, security and risk management professionals would be wise to reflect on past failures in hopes of making our society antifragile to future global calamities.

Research Review: Quality of Work Life for Bank Guards
Researchers conducted a case study in 43 bank branches in the Brazilian city of Campos dos Goytacazes to determine the most important aspects of what security guards considered in evaluating their quality of work life (QWL).

Research Review: Measuring Security Culture
The researchers’ goal was to evaluate the various tools available to determine whether they are effective in accurately measuring the security culture within an organization.

Trust Has Never Been More Important
In addition to dealing a blow to a company’s culture, a lack of trust can sabotage productivity, engagement, and retention.

Onboarding Beyond Zoom
Millions of people are transitioning to new, changed, or evolving roles in the post-pandemic upheaval. As onboarding shifts virtual, CSOs have an opportunity to leverage a new normal of online meetings to get up to speed and begin adding value faster and more effectively.

Cyber 101 for Physical Security Practitioners
When it comes to cybersecurity, there are many terms and concepts that are beneficial for physical security professionals and IT professionals alike to understand. Here are a few to help you get started.

Assigning Roles for Campus Security Awareness
The high student population, prevailing freedom, lack of guardians, and homogenous nature of the college campus setting create an environment with many opportunities for crime to occur. A modified security model is therefore needed.

Challenges in Higher Education Security: Open Environments
The initial step in developing a balanced security program is engagement with users at all levels. This includes understanding the privacy concerns of residents, safety issues surrounding various modes of transport, and layered security controls of a multipurpose building.

Executive Risks Intensified Throughout Pandemic, Study Finds
More than half of respondents to a recent survey agreed their CEO has received physical threats both as a result of either expressing (58 percent) or not expressing (40 percent) a position on racial and/or political issues.
Balancing Needs and Wants Against Situational Realities in Campus Security
As the threat landscape has changed, security leaders have had to adapt. It is infinitely important that the leaders responsible for the safety and security on university and healthcare campuses comprehend and strike a balance between needs versus wants as they build their programs to respond to changes.

Challenges in Higher Education Security: Finance and Funding
Incorporating financial needs into strategic plans can give organizations a more complete and proactive picture of the proposed system and its future, paving a clearer path to avoid administrative and technical challenges.

The Background Check Dilemma in a Shrinking Labor Pool
In the competition for labor, employers may be prone to hire the first living, breathing person who applies. As tempting as it may sound, this hiring practice is fraught with danger.

Challenges in Higher Education Security: Technology and Systems
Technology challenges at universities are often ones of scale and sustainability, which can limit the organization’s ability to meet current security needs or maintain compatibility with contemporary edge devices.

Global Management: How Security is Changing in Jamaica
How are certification and professional development changing perceptions of security practitioners in Jamaica?

Challenges in Higher Education Security: Portfolio Administration
Multifaceted requirements at universities make creating a project portfolio for management large and expensive to build, complex to manage, and challenging to maintain. Portfolios can therefore risk exposure to legacy systems, inefficient processes, and high costs of ownership.

Reimagining Security in a Post-2020 World
Integration into the workforce environment, rather than mere patrol of it, is more necessary than ever for an accurate assessment, prevention, and disruption of threats.

Managing Risk as Demand for Private Security Grows
As pandemic restrictions ease and calls continue to defund the police, security guard firms should understand their risks before taking on high-profile clients.

Don't Play So Close to Me
Casinos and gaming facilities are increasingly relying on touchless methods to ensure guests can safely play, allowing them to scale their pandemic mitigation measures.
Employee Activism as a Risk Management Opportunity
The combination of increased activism and elevated divisiveness presents a heightened threat for conflict entering the workplace, particularly for corporations whose employees are returning to the office after working remotely.

Job Candidates Hunting for Workplace Safety, Flexibility, and Diversity
Job seekers are holding potential employers to higher standards in workplace health and safety efforts, diversity initiatives, and flexible work arrangements in the wake of the coronavirus pandemic and social unrest of 2020, according to a recent survey.

Balancing Tolerance of Diverse Views and Workplace Violence Prevention: When Extreme Views Lead to Extreme Acts
Left unchecked, extreme beliefs can not only threaten cohesion and productivity, they can compromise safety and raise the risk of disruptive behaviors, even violence.

Extremism in Plain Sight: Recognizing and Responding to Symbols and Threats
We live in a world filled with visual images, and their meanings often changed based on context--benign in one case but inflammatory in another. So what does this mean for monitoring signs of extremism in the workplace?

Engaging Employees on Their Mental Health
The mental wellbeing of the workforce needs to be a major consideration as organizations move forward after the last year-and-a-half of turmoil.
Global Management: How Security is Changing in Western Europe
With more than 40 countries in close proximity, managing security and teams in Europe is a test of cultural intelligence and flexibility.

The Growing Mental Health Crisis
Months of turmoil and upheaval take a toll; the mental wellbeing of the workforce has never been a more important topic.

The Changed Nature of Civil Unrest: Lessons from 2020 in Philadelphia
Security professionals need to ask themselves two key questions: Can we protect our property when the police are overwhelmed and does our company have the resources to win the communications battle?

The Insider Threat and Extremist Rhetoric
While the growth of polarizing and extremist rhetoric may be most commonly attributed to an advancing Internet, the traditional approaches to mitigating insider threat risks may also be effective in reducing the incendiary quality of extremist rhetoric before it results in harm or destruction.

Six Steps for Incident Prevention Amid Growing Physical Threats
Psychologically, executives will want to believe that things will go back to normal, but COVID-19 has changed that for the foreseeable future.

Returning to Work the ESRM Way
With vaccinations on the rise, organizations are seriously contemplating whether and how to return to physical workspaces. By leveraging ESRM principles, security leaders can help steer the conversation.

Leveraging Public Data to Mitigate Threats
Worrisome indicators often precede insider threats. More and more, these indicators are reflected in publicly available spaces.

Learning the Red Flag Indicators of Human Trafficking in Multitenant Spaces
Private security personnel are ideally situated to observe people who are vulnerable to trafficking or are currently being trafficked.

Combating Complacency: Lessons Learned from the 1994 AMIA Bombing in Argentina
World events from 9/11 to today demonstrate that violence and extremism are a prevalent threat, with the risk of right-wing terrorism rising globally. But 25 years after a major terrorist attack in Argentina, complacency is setting in.

How to Avoid Pandemic-Related Litigation Risks
Worries over workplace safety in the COVID-19 era, as well as concerns about the impacts of business closings, plant shutdowns and mandatory stay-at-home orders, spawned more than 2,000 lawsuits from January 2020 through March 2021.

Protection of Assets: Online Information Sources for Investigations
The Internet can be a powerful force multiplier for investigators. When used prudently and strategically, online information sources are undoubtedly a critical component of a thorough investigation.

Enabling Agile Decisions in a Rapidly Evolving Risk Environment
Many security leaders have discovered that, due to the pace of change and increasing demands for real-time risk analysis, organizational capabilities that were effective five years ago are no longer sufficient in today’s environment.

Updating Business Continuity Basics After COVID-19
Core services do not mean all services. In a private enterprise scenario, your core functions must be identified so that your continuity plan ensures at least their partial operation within the shortest amount of time possible.

Protection of Assets: Leveraging Investigative Results
The organization needs to have mechanisms in place to leverage any and all investigative findings for process improvement.

A Cut Above the Rest: Using Puns to Promote Security Awareness
TSA’s Instagram account has nearly 1 million followers. Here’s how it uses its feed to share important security updates, one great catch and K9 at a time.

A Portrait of Fire Prevention
When it comes to protecting priceless pieces of cultural heritage, following industry best practices with planning, automation, and early response measure proves essential.

Fostering the Geniuses in Your Backyard Through DE&I Efforts
“If we don’t start growing the number of people we’re fostering, our industry will go extinct,” says Rob Duhart, Jr., global head of federated security at Google.

Time to Pivot: Applying ESRM After COVID-19
The COVID-19 pandemic may have provided an ideal push for organizations to implement an ESRM approach to resilience and crisis management, which can multiply security’s value to the business.

How Toxic Masculinity Ruins Workplace Culture
When leaders fail to see how toxic masculinity affects their teams’ dynamics, the whole organization is at risk.

Ancient Art, Illicit Revenue
Organized crime groups, terrorists, and state actors have all dabbled in antiquities trafficking to fund their operations. But the scale of the market remains elusive due to the diversity and secrecy of the art world.

Risk Assessment Approaches for the Reopening of Cultural and Heritage Venues
Most museums and heritage sites were forced to close during 2020 in response to COVID-19-related lockdowns. Here’s what should be top-of-mind as they reopen.

Protest Preparedness: Analyzing Crowd Dynamics, Threat Actors, and Intelligence
While most protests are peaceful, some trigger violence, riots, looting, and clashes with law enforcement, and where one protest escalates, other movements are likely to watch, learn, and adopt similar tactics or countermeasures.
Controlled Unclassified Information: What Happened to Marking Everything FOUO?
Requirements for information protection are changing. The U.S. government is taking a new approach in marking and handling Controlled Unclassified Information, which can lead to best practices in the private sector by modeling proper protection methods for sensitive information.

The Case for Access Control for Cannabis Businesses—Even When It’s Not Required
Investing in expensive technology when it is not required can be a hard sell. So before you invest, carefully weigh the benefits and considerations of access control technology.

Know Before You Hire: Three Employment Screening Trends in 2021
The COVID-19 pandemic will continue to impede aspects of employment screening in 2021, leading employers to use alternative procedures such as conditional hiring and remote drug testing.

Four Steps for Getting Started with CMMC Compliance
These new requirements act as the U.S. Department of Defense’s response to strengthen its focus on cybersecurity and resilience against outside forces and emerging security risks.

The FBI Art Crime Team: Repatriation, One Antiquity at a Time
Along with investigating fine art thefts, the FBI Art Crime Team also works with partners around the globe to track down and return antiquities to their rightful homes.

Controlling Stress Responses for Better De-Escalation
As security personnel are expected to stay responsive and nimble in the face of the unexpected, knowing how to de-escalate yourself is key.

The Preparedness Puzzle
Resilience is a multifaceted concept, and depending on which way you view it, you may see different challenges and stronger solutions, says Michael Szönyi, Flood Resilience Program Lead at Zurich Insurance Company.

Getting Proactive with Protective Intelligence
Eighty-seven percent of security, legal, and compliance executives agree that investment in technology to advance physical security effectiveness and mitigate violent threats is necessary for the future of their company, according to a recent study from the Ontic Center for Protective Intelligence.

Adjusting Security Awareness for Remote Work Hygiene
As the lines between work and leisure time become increasingly blurred and employees use company-issued devices and resources for personal use—such as social media, online shopping, and even telehealth—the potential for cyberattacks is ever present.

Public–Private Partnership Case Study: OSAC
Nearly three decades ago, the U.S. government grew increasingly concerned of the potential negative impacts of rising globalization and terrorism on U.S. corporations with international operations, giving rise to the creation of the Overseas Security Advisory Council (OSAC).

Looking Ahead: Shifts in Training Needed for Security Guard Use of Force
The differences between training and learning will require a major shift in preparation and standards for armed security officers.

Answering to Abuse
With more employees working remote and from home, companies’ have become increasingly liable once a victim informs them that he or she now works and lives with the abuser.

The Chief Security Strategist in an Age of Uncertainty
The contemporary CSO has to understand the geopolitical dynamics of the 21st century. In an interconnected and a globalized world, a crisis in one part of the world will have profound cascading effects on organizations on the other side of the globe.

Shared Successes: Building Collaborative Professional Networks
Where do I start? It’s a common refrain, whether it’s coming from a young professional just entering the security industry, a former law enforcement officer building her first private sector SOP, or a security industry veteran preparing to combat a new crisis. Fortunately, few of these paths need to be walked alone.

Change is the Only Constant: Lessons Learned from Uber
After five years, six managers, and three promotions, Carla Gray shares her insights and guidance for security managers operating in both global enterprises and agile, rapidly growing startups.

Embracing True Diversity in Times of Crisis
The business case for diversity is stronger than ever. A 2020 report found that companies that foster gender diversity are 25 percent more likely to have above-average profitability than companies that don’t.

Training Security Guards to Identify Sex Trafficking Victims
Child sex trafficking is a multi-billion dollar a year business. Besides the moral obligation to combat domestic minor sex trafficking, businesses are criminally and civilly liable as facilitators for indirectly, but knowingly, profiting from the venture in reckless disregard to use of a minor.

Measuring Employee Engagement During a Crisis
For companies to maintain a motivated, productive workforce, organizations need to find the best methods to gather and interpret employee feedback, including from remote workers, and make changes accordingly, experts say.

Accelerationists Rising: The State of U.S. Hate Crimes
Rising hate crimes in the United States show the increasing threat of accelerationists in white supremacist groups.

Q&A: Essential Takeaways from the 6 January Riot at the U.S. Capitol
As U.S. federal law enforcement agencies warn of a potential wave of armed protests across the United States in the coming week, members of the ASIS International Extremism and Political Instability Community share lessons learned, analysis, and preparedness advice for the days ahead.

Conspiracy and Consequences: When Mass Delusions Come to Work
At its core, QAnon is a militant and anti-establishment ideology focused on destroying the existing corrupt world order and accelerating the arrival of a new Golden Age. When true believers turn violent, workplaces and employees are at risk.

Q-Speak: The Language of QAnon
Knowing the basics about QAnon, as well as the terminology and beliefs of this movement, can help security leaders recognize when someone is being led down the rabbit hole and possibly becoming a risk.

Developing a Layered Defense to Harden Facility Security
Hardening is an offensive security measure; it stops the fight before it starts.

Leading from Afar: Remote Management Lessons from CSOs
As organizations double down on remote work policies, security leaders shift their management, communication, and mentorship styles to foster team wellness and personal resilience.

The Vaccine Is Here, Are You Ready?
Organizations need to begin to plan now for the wider rollout of the COVID-19 vaccine and what policies and procedures they need to have in place.

Travel Safety eLearning: A Reasonable and Practicable Alternative to In-Person Travel Risk Mitigation
As companies begin readying their workforce for a new normal in anticipation of use of widespread COVID vaccine, eLearning can offer a safe, flexible, and perhaps more efficient method of ensuring business travelers are appropriately versed in risk mitigation wherever they go.

Crowd Avoidance: COVID-19 Spurs Interest in Smoother Security Lines
If security screening lines are too crowded, many Americans said in a recent poll that they would abandon plans to attend an event or enter a facility.

Softening the Impact of a Hard Insurance Market
The year 2020 started inauspiciously with a hard security insurance market in the United States. This meant security firms experienced rising premiums and tightening underwriting guidelines, largely due to concerns about claims, costly legal settlements, and risk management in the industry. These issues were only exacerbated by the emergence of COVID-19 and civil unrest.

Surging Gun Sales Could Soon Become a Workplace Concern
The pandemic, the recession, and various protests are driving a record increase in gun purchases in the United States, and some experts are concerned about what that might mean for employees.

Managing Stress, Leading, and Serving Through Crises
Crises are by nature unpredictable and uncertain. Our brains process uncertain and unpredictable events as life-or-death threats. During a crisis, one of the key steps to manage our stress and our emotions and to foster our perspective and analytical reasoning is to de-shame.

Emerging from the Ashes: How Aviation Security Rises After COVID-19
Airports have seen a drastic reduction in international travel due to the coronavirus pandemic. Once traffic resumes, however, security screeners will need to hit the ground running.

Protecting Shops from Looting
Beyond retail shrink caused by shoplifters, internal thieves, or fraudulent returns, retailers are also aware of the risks posed by those taking advantage of chaos from mass protests that have become regular occurrences in 2020.

Leading with Empathy: Fostering Engaged Workforces
Much like the world we live in, the security business has changed, and the lessons gained serve as a powerful reminder that to be effective in our industry, we need to evolve as leaders to get the best out of our people.

Rethinking SOC Functionality and Cost
Considering the global shift toward more service-based providers and platforms for physical security, it can be argued that the overall cost of protection is being reduced.

How to Avoid Eight Diversity Recruiting Mistakes
Employers are re-evaluating workplace diversity at their organizations, starting with being more thoughtful about recruiting from a broader range of talent. However, these efforts are not without pitfalls.

Monitoring Remote Workers
Monitoring tools can track productivity and guard against security threats, but employers should weigh the benefits against the legal risks.

Three Steps to Avoid Security Theater
Not all risk mitigation measures are made equal. When managers deploy countermeasures without first understanding and addressing the company’s own specific risk posture, they are contributing to “security theater”—a concept that refers to security measures that make people feel more secure without doing anything to actually improve their security.

Four Principles for Leadership for Security and Safety in the New Normal
Extreme challenges present opportunities to do things better. Leaders are at a major inflection point, affording the chance to reroute connections and revise how they lead industries, endeavors, and teams—which has implications for safety and security.

Change Drivers: Organizations Face Supercharged Activism
“The push for companies to show what they are doing for the greater good will only intensify through the lens of the pandemic; the public will want to know whether companies put people or profits first during this global crisis,” says Allison Wood, an associate director at Control Risks.

Navigating the Impacts of COVID-19 in Mexico’s Manufacturing Sector
As much of the manufacturing industry in Mexico has continued operations classified as essential throughout the federally mandated quarantine, businesses are facing unique and acute challenges.

COVID-19: The Rise in Domestic Violence
Alongside the COVID-19 pandemic, a less-publicized public health crisis is surging across the globe—domestic violence. This guide for employers can help address employee needs and workplace concerns during remote work and return-to-work settings.

Your Hiring Assessments Could Get You in Trouble
Hiring assessments can be a slippery slope for employers, especially when they rule out protected employees and create disparate impact.

Remote Terminations: Special Considerations During COVID-19
Terminations can be triggers for workplace violence in normal times. With COVID-19, these are not normal times, and an organization that needs to lay off staff should account for the unique stress its staff is already enduring.

Virtualization and Empowerment: Microsoft’s VSOC Revs Up During COVID-19
A long-term push for digital transformation paid off for Microsoft’s security department when COVID-19 disrupted global operations.

Ready for Reentry?
As organizations reopen their facilities, they must be aware of threats that may arise from a lack of human presence during shelter-at-home orders, such as the opportunity for Legionnaires’ disease outbreaks.

Implementing Split Operations to Improve Resilience During a Disease Outbreak
Employees are an organization’s most valuable asset. Businesses that implement robust and sustainable strategies to take care of their people during the COVID-19 pandemic will fare better than those that do no not.

How to Protect Company Data When Laying Off Remote Workers
Laying off employees is always painful, but having to do so when they are completely remote adds a new wrinkle: What should employers do to protect the company's data on laptops and other devices when letting remote workers go?

Adaptability Helps University Deal with Pandemic's Uncertainties
Harding University Assistant Director of Public Safety Kevin Davis discusses how security at his school managed the pandemic-related campus closure and what they doing to prepare for what comes next.

Conducting COVID-19 "In-Flight" Incident Reviews
At this time, there is tremendous value in briefly pausing to reflect on the organization’s COVID-19 journey to date and conduct an “in-flight” incident review as a means of optimizing the approach going forward.

A Guide to Employee Temperature Checks
The U.S. Equal Employment Opportunity Commission (EEOC) gave employers the green light to take employees' temperatures to try and ward off the spread of the coronavirus. But will taking temperatures really work?

Q&A: Agility and Planning for Multinational Pandemic Response
For international business services company PricewaterhouseCoopers (PwC), managing business continuity and crisis response to the coronavirus pandemic has tested its international, regional and national capabilities. However, key steps—such as the early creation of a dedicated task force for information sharing—have driven a more streamlined, agile crisis response.

How to Anticipate Pandemic-Influenced Risk Developments
Security directors add value when they find data-based leading indicators that can help an organization prepare in advance for the risk factors unfolding as a result of COVID-19.

How to Reopen Your Mail Centers
In the face of the coronavirus pandemic, many companies shut down their offices and told people to work from home. As they begin to reopen, companies will face several major hurdles in their mail centers.

Hiring Blitz by Big Security Firms Continues, Despite Record Unemployment
With U.S. unemployment now at record levels, Allied Universal and G4S are swimming against the current by hiring tens of thousands of new security professionals.

Q&A: Managing Perceptions, Expectations, and Information Fatigue in a Pandemic
As news proliferates yet public interest wanes, security leaders face myriad challenges to present accurate, timely, and actionable information to key decision makers. Here, two CSOs share their tips for communicating and influencing perception during the pandemic.
Resetting the Business After the COVID-19 Pandemic
Using an ESRM-based approach can help organizations re-emerge after facing major, pandemic-induced disruptions.

Security’s Role When Buildings Are Repurposed as Temporary Medical Facilities
Convention centers have played an important role in regional pandemic response. Here are some lessons learned from those put into use so far.

Leadership in the COVID Crisis: The Importance of Building Personal Resilience
Effective leadership in the current crisis requires prioritizing your mental well-being alongside that of your employees.

Coronavirus and Conflict: The Pandemic’s Potential Global Impact
The coronavirus pandemic could stir further global destabilization even after the virus is contained.

Travel Risk Through the Lens of the COVID-19 Pandemic
This short segment excerpted from a webinar describes the travel risks the pandemic exposed.

Q&A: What Employers Need to Know About Essential Workers and PPE
Security professionals are often considered essential personnel who must report to work during the coronavirus pandemic. Here’s what employers need to know to ensure staff is prepared to be at the job site.

Organizations Make Key Standards Freely Available
ASIS, ANSI, and others open access to certain standards to help organizations in their pandemic response.

Q&A: How Security Teams are Adapting to Closures
Almost one-fifth of the world is under some form of lock down. Here’s how those measures are impacting security teams protecting services and sites.

Q&A: CSO Perspectives on COVID-19 Response
Amid floods of information, sales pitches, shifting risks, and staffing challenges, how are enterprise security leaders keeping up during the COVID-19 pandemic?

COVID-19 in West Africa: A Security Manager’s Perspective
As the pandemic spreads through West Africa, a seasoned manager in Nigeria discusses the implications for security.

ESRM and the COVID-19 Pandemic
The preparation involved in enterprise security risk management (ESRM) enables organizations to act decisively and confidently in times of crisis.

Remote Work Considerations in the COVID-19 Age
More organizations are shifting to allow employees to work remotely. Now is the time for enterprise risk managers to strengthen programs against new vulnerabilities unique to telework.

Japan Declares State of Emergency, No Lockdown for COVID-19 Response
Japan Prime Minister Shinzo Abe declared a monthlong state of emergency yesterday in response to the coronavirus pandemic.

In Crisis Communication, Start with Empathy
Crisis response hinges on two factors: what the organization does and what the organization says. When these halves align, it results in trust and a more positively received and effective response.

How the Coronavirus Pandemic Impacts Security Service Firms
The pandemic has increased demand for security among many, and officers are being challenged with new duties and tasks.

How to Add Pandemic Response to Business Continuity Plans
The decisions you make today to mitigate the threat of the coronavirus pandemic will have significant impact on your operations in the future.

Q&A: How the Bank of Hawaii is Responding to COVID-19
Brian Ishikawa, senior vice president and director of corporate security for the Bank of Hawaii Corporation, shares how the coronavirus has impacted the bank's business continuity.
BCI Study: State of Organizational Business Continuity Plan Implementation
Most organizations have activated incident management teams; fewer had practiced for an emergency situation in the previous 12 months.

Q&A: Security’s Role During Pandemic Response
Scott Stewart from Stratfor explains how security professionals can leverage their creative problem-solving skills and preparedness to diffuse panic and secure operations and assets during the coronavirus pandemic.
Pandemic Impacts HR issues
Whether employees are working at home or on-site, employers should be aware of various workplace and employment issues raised by COVID-19 mitigation efforts.

Report on COVID-19 Response from Asia Pacific
The chief information security officer for Fullerton Health, based in Singapore, discusses his organization's experiences dealing with the pandemic.

Global Demand Puts Pressure on Healthcare Supply Chains
In light of potential shortages and rising value of personal protective equipment (PPE), healthcare security professionals can take additional steps to protect these newly high-value items and shore up supply chain vulnerabilities.

Casino Resort Tactical Response Teams
How are casinos maintaining the softness required for guest services while simultaneously keeping up a tough front against an increasing number of public attacks?

Key Elements of Pandemic Readiness
The world has changed since the 2003 SARS outbreak. Has your pandemic preparedness plan changed with it?

K9 Teams Press “Paws” on Healthcare Violence and Crime
Whether de-escalating potentially violent scenarios, managing crowd control, or simply acting as a visual deterrent, highly trained K9 security teams are playing an important role at U.S. hospitals and medical centers.

The Rise of eCommerce Fraud
The use of stolen customer information to purchase goods is becoming an even larger threat to online retailers.

The Rising Cost to Insure Security
A rash of large insurance claims in the United States has been reshaping the security insurance market, especially regarding security guards and guarding firms.

Managing Risk for World Youth Day
Every three years, millions of youth from around the globe make a pilgrimage to see the Pope. This poses unique security challenges.

Q&A: John Kelly on China, Partnerships, and Border Security
At GSX 2019, Marine Corps General John Kelly (Ret.) sat down with Security Management to talk about how the United States is grappling with issues that the country faces today and will continue to deal with in the future.

Data Privacy, Information Management, and Security: Adjusting to a New Normal
Stakeholders can work hand in hand to protect against insider and external threats and reduce the risk of data loss while simultaneously improving data protection and streamlining processes.

Protecting Soft Targets without Hindering Culture
How do you protect a soft target—a restaurant, a museum, a park, or a city street—without taking away from its beauty, cultural value, or intended use?

Lessons Learned from the Notre Dame Fire
In the aftermath of the Notre Dame fire, security professionals should assess similar risks to their institutions.
Tomando Vuelo
En el condado rural de Grant, Washington, el personal de servicios públicos no sólo protege las subestaciones remotas: también ayuda a responder a los llamados de emergencia de la comunidad.

Newsroom Shooting Highlights Challenges of Securing Open Offices
An open office environment and a barricaded exit made it impossible for Capital Gazette employees to flee an active shooter.

Video: Charleston International Airport Modernizes Security with Pivot3
Along with a recent renovation, Charleston International Airport invested in a new state of the art IT system to support operational efficiencies, including for its security, surveillance, and access control systems.