Leaderless Resistance: Understanding and Countering an Amorphous Threat
Extremist movements rise and fall, but the key, high-impact threats remain consistent. In my assessment, the most severe terrorist threat to targets in the United States today stems from professional terrorist cadres, such as the group of 19 attackers responsible for the 9/11 attacks.
However, due to security improvements made in the wake of the 9/11 attacks, extremist groups have had difficulty getting trained operatives into the United States or training and organizing them domestically. As a result, the most likely terrorist threat today comes from lone assailants and small cells operating under the principles of leaderless resistance.
The same dynamic applies outside the United States, such as in Europe, Australia, and New Zealand. The 16 October 2023 armed assault in Brussels by a Tunisian extremist is a recent illustration of this threat.
Extremist ideologues did not freely choose to adopt leaderless resistance. They have been forced to adopt this operational model in response to effective government counterterrorism programs. In recent years, when extremists have attempted to form groups to conduct terrorist activity—such as Atomwaffen, The Base, and the group of extremists plotting to kidnap Michigan Governor Gretchen Whitmer—they have been quickly infiltrated and efficiently dismantled.
This relentless counterterrorism pressure has constrained the abilities of extremists of all ideologies, including jihadists, white supremacists/nationalists, anarchists, and single-issue extremists. As a result, they have all adopted the leaderless resistance model of terrorism.
White supremacists were among the first to adopt leaderless resistance, when many ideologues began promoting it the late 1980s following the Fort Smith Sedition trial. Environmental and animal rights extremists were also adopters of leaderless resistance, as was seen by the operations of the Earth Liberation Front (ELF) and the Animal Liberation Front (ALF). Jihadists were a little later coming to leaderless resistance, but after years of frustration trying to get operatives into the United States to conduct attacks, al Qaeda in the Arabian Peninsula (AQAP) began to promote leaderless resistance in 2009 in its magazine Sada al-Malahim.
Now, nearly every successful terrorist attack in the United States since 9/11 has been conducted by a lone attacker or small cell operating under the rubric of leaderless resistance. Such incidents characteristically involve simple attacks directed against soft targets using readily available weapons such as firearms, crude bombs, edged weapons, and vehicles.
What Is Leaderless Resistance?
First, leaderless resistance is an admission of weakness: it is the recognition by extremist ideologues that counterterrorist forces are so effective at targeting known individuals and extremists operating in hierarchical groups that they cannot operate in that manner. In response, they choose to adopt a shapeless form of extremism intended to produce ambiguity—a problem for all governments struggle.
Perhaps the most accurate description of leaderless resistance was penned by Klansman Louis Beam in 1983 and republished in a Ku Klux Klan newsletter in 1992. In Beam’s conceptualization of leaderless resistance, the violent extremist movement should be divided into two tiers.
The first tier is the legal and aboveground “organs of information” that would “distribute information using newspapers, leaflets, computers, etc.,” Beam wrote. The ideologues who comprised the organs of information were encouraged to use First Amendment protections for free speech to shield their operations and were advised to not conduct any illegal acts. Instead, their role was to articulate grievances, provide direction for those conducting attacks, identify enemies of the movement, and issue propaganda for recruitment purposes.
A wide array of extremist idealogues today use social media to attract new adherents, identify targets, and foment violence. Some ideologues operating in the West carefully tread the boundaries of free speech, while others openly spew vitriol from conflict zones abroad.
The second tier of the extremist movement is composed of individual operators and small phantom cells conducting attacks and other illegal activities. These extremists remain low-key and anonymous, with no connections or communications with the aboveground extremist ideologues.
In today’s parlance, we often refer to this violent, operational tier of the extremist movement as self-initiated or grassroots terrorists. The press often refers to them as lone wolves, although I think that term glamorizes the threat they pose.
This strict separation between the segments of the ideological movement is meant to prevent government agencies from being able to prosecute the ideologues for the crimes they commit. It is also intended to make it more difficult for the government to identify individual actors and infiltrate or compromise the small cells planning and conducting attacks.
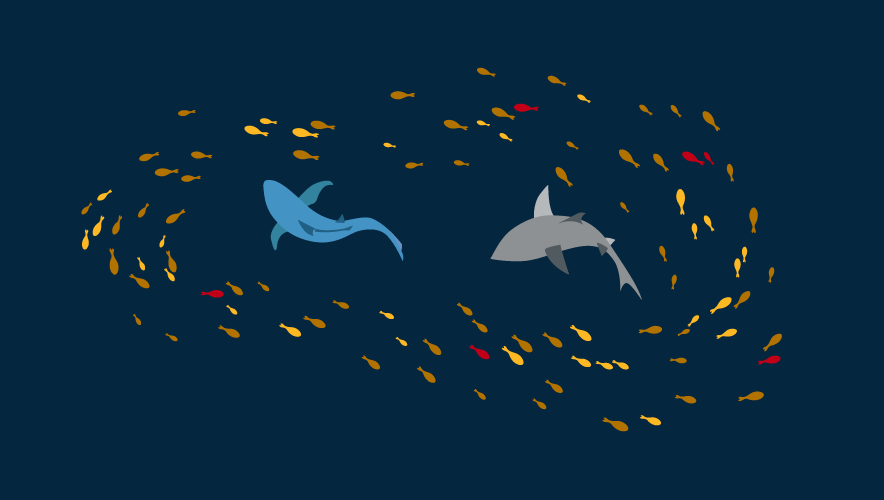
To illustrate leaderless resistance, I often use the analogy of a shark and baitfish. Like government counterterrorism forces, a shark is a highly efficient hunter: its sophisticated sensors can lock on to and devour any target it can identify. A single fish—be it a minnow or a tuna—is helpless against a shark.
The idea behind leaderless resistance is for extremists to fade into the midst of society like a single fish in the center of a huge school of baitfish. The movement and activity of the thousands of individual fish within the school serve to overwhelm the sensory capacity of the shark, making it difficult for the predator to lock on to any single target.
Harder Than It Looks
By design, when executed with rigorous discipline, leaderless resistance provides a high degree of operational security and can be highly effective at masking extremist operations. If those planning an attack are careful, it can be very difficult to detect them with traditional counterterrorism tools such as using informants or tracking travel, communications, and funds. Disciplined lone extremists like Joseph Paul Franklin, Eric Rudolph, and Ted Kaczynski, and small cells like “The Family” were able to conduct terrorist attacks for years in this way before being caught.
However, while leaderless resistance does provide very good operational security in theory, it is not easy to practice. By definition, it forces a lone attacker or small cell to finance, plan, and execute an attack without outside guidance and assistance. Many attackers have struggled from a lack of both resources and terrorist tradecraft.
“Terrorist tradecraft” is the set of skills a person needs to conduct an attack. These tradecraft skills include the ability to travel without detection, communicate clandestinely, ensure operational security, and covertly transfer money. Once the operatives are established in the location where the attack will be executed, they then need to conduct their attack cycle without being detected. This entails conducting multiple rounds of surveillance on the target—a point in the attack cycle where many plots are thwarted. Acquiring weapons for an attack can also be a considerable challenge for militants operating in a hostile security environment, along with manufacturing effective bombs.
To compensate for this lack of tradecraft, extremist movements have created detailed manuals to assist lone attackers and small cells in their efforts. Examples include the ELF timed incendiary devices manual, the ALF arson guide, and al Qaeda’s Inspire magazine. Many successful attackers have used these guides, including the Boston Marathon bombers, who carefully followed the pressure cooker bomb instructions provided in Inspire.
Many plots have been thwarted when would-be attackers asked outsiders for help acquiring weapons or manufacturing bombs and inadvertently stumbled into government sting operations. Examples in the United States include thwarted bombing plots against a Pittsburgh church in 2019, an Oklahoma City building in 2017, and the Wichita airport in 2013.
In general, however, tradecraft remains the bane of would-be terrorists operating under the leaderless resistance model, giving security teams an opportunity to mitigate these threats.
Focusing on the How
If extremists who are planning an attack self-identify through posts on social media or have contact with an extremist ideologue under surveillance, they become easy prey for government counterterrorism forces. When they do not self-identify, it is more difficult to identify them from the population they hide within. One way to identify extremists from others is by focusing on the activities associated with the attack cycle.
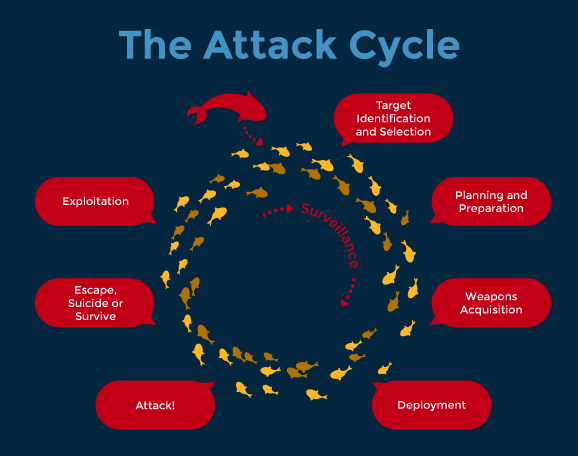
Those intending to conduct a terrorist attack are bound to the attack cycle. They must select a target, plan the attack, acquire the weapons to be used, conduct surveillance, and then deploy to the attack site to conduct the attack. Once the attack is conducted, whether the attacker(s) dies, survives, or escapes, they or the movement they are connected to will seek to exploit the attack.
Operating under the leaderless resistance operational model, lone assailants and small cells are even more exposed by the constraints and vulnerabilities created by the attack cycle. They must conduct each step of the attack cycle by themselves. Potential assailants must expose themselves to detection at more points throughout the cycle than would a hierarchical terrorist group with many members or cells.
Now, the attack cycle will obviously vary at least slightly based on the specific circumstances and the type of attack involved. A simple pipe bomb attack, for example, will require less surveillance than an assassination or kidnapping, and a suicide attacker needs no escape plan. Despite these variations, certain steps must be taken to conduct an attack, which means there are windows when extremists planning an attack become unavoidably vulnerable to detection.
Terrorists are extremely vulnerable during the preoperational surveillance conducted during the target identification and planning stages of the cycle. Most extremists possess poor surveillance tradecraft. They tend to behave suspiciously, look out of place, and lurk—what we refer to as exhibiting bad demeanor. Because of this, surveillance can be highly effective in detecting and identifying extremists progressing through their attack cycle. The main reason extremists can succeed with attacks despite their poor surveillance tradecraft is that, in general, they are not watching for surveillance.
Efforts to detect hostile surveillance can range from individuals practicing proper situational awareness to formal countersurveillance teams. In general, it does not take much sophistication to spot the clumsy surveillance conducted by grassroots extremists. Surveillance is as much an art as it is a science, and it takes a significant amount of training to create a good surveillance operative.
Those operating under the rubric of leaderless resistance simply don’t receive this type of training. Thus, they tend to lurk with no apparent reason to be where they are or for doing what they are doing and thus look out of place. They also tend to be nervous while conducting surveillance, which causes them to generally stick out from the people around them. Many times, simply looking at people conducting surveillance is enough to make them react in an unnatural way and to reveal themselves as hostile actors.
Security teams should both train employees on how to identify hostile surveillance and implement a program to report and investigate suspected incidents of surveillance.
Identifying attack cycle behaviors permits security teams to adopt additional measures to mitigate or avoid potential threats. In some instances, this increase in security posture is enough to cause a would-be attacker to decide to divert to an easier target, because they don’t have the skill required to attack a well-defended target.
Bringing a person evidencing attack cycle behaviors to the attention of law enforcement may be enough to put them on notice that they are being carefully scrutinized. An interview by a law enforcement officer might also be enough to prevent the person from continuing through with the attack cycle.
However, many attack cycle behaviors do not cross the line into criminality. For example, an individual has broken no laws by standing on a sidewalk watching a motorcade depart from a corporate headquarters. Conducting Internet searches for the home address of a celebrity or corporate leader is not illegal. That said, when protective intelligence teams focus on detecting attack cycle elements such as preoperational surveillance—the “how” of an attack—they can begin to focus on identifying and assessing “who” may pose a specific threat. In this way, spotting the “how” enables security teams to bring a shapeless threat into sharp focus.
Scott Stewart is the vice president of intelligence at TorchStone Global. He is a seasoned protective intelligence practitioner with 38 years of analytical, investigative, and security experience. Stewart spent 10 years as a special agent with the U.S. Department of State’s Diplomatic Security Service, where he was involved in a large number of high-profile terrorism and protective intelligence investigations. He also led Stratfor’s analysis of terrorism and security topics from 2004 to 2020 and served as the protective intelligence coordinator for Dell from 1998 to 2004.