

August 2023
Protecting Privacy and Corporate Data on Employee-Owned Mobile Devices
Our mobile phones today contain many things we hold dear: our photos, our financials, our contacts, and more. We use our devices for everyday life, which can include our daily work activities. With a powerful handheld computer in many of our pockets, organizations must manage corporate data while protecting the privacy of employees across the enterprise.
Knowing where to start when protecting these devices is vital for ensuring data security while maintaining employee privacy. As an increasing number of employees use mobile devices for work, it is important for leadership to be aware that modern mobile devices come with mechanisms that separate personal and corporate data.
Device Security 101: Best Practices for Phones
Threat actors are increasingly targeting mobile devices to gain access to sensitive information. The U.S. National Security Agency recommends following these best practices to maintain the security of your device.
The Time is Up for TikTok: How to Effectively Enforce an App Ban
Banning TikTok is not as easy as adding the social media app to a block list. Instead, organizations will need to create strong operational governance combined with mobile device management, network security solutions, and strong visibility solutions to ban the app.
Research Shows Growing Role of Mobile Access Control to Improve Sustainability, Facilitate Hybrid Work
Trusted ecosystems of cloud-connected mobile devices fuel future-proofed solutions for optimizing building operations and securely accessing services through mobile phones and other devices.
Assessing the Need for Heightened Mobile Device Security Awareness
The proliferation of mobile devices has amplified cyber risk to new heights, where most people today are walking around with a high-impact vulnerability in their pocket and don’t even realize it.
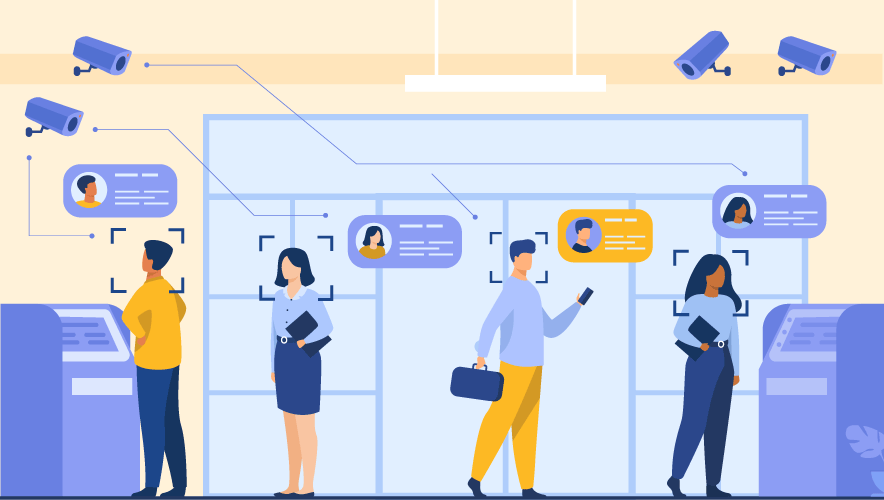
Mobile Access and Secured Entry Solutions: The New Lobby Ecosystem
Secured entry solutions integrated with mobile access offer front line protection against risks that can harm organizations from the outside in.
Infographic: What is SIM Swapping?
Fraudsters are increasingly using a technique that targets mobile devices to gain control of their targets’ financial and social media accounts. Here’s how it works and how you can prevent it.
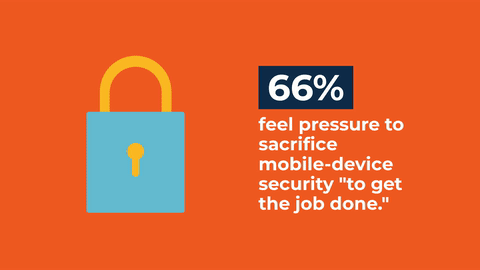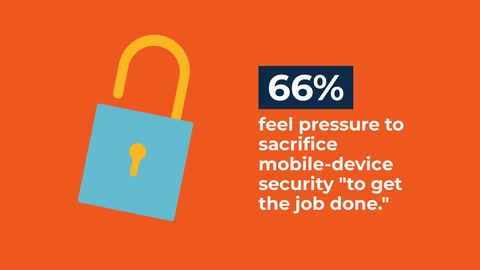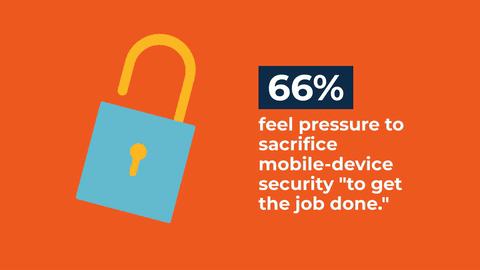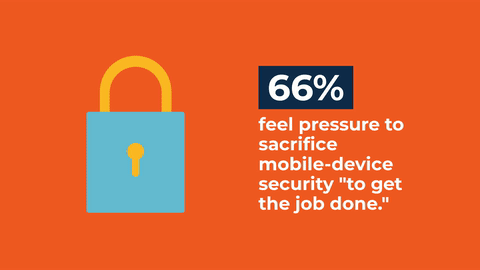
Making Sense of Mobile Threats
Mobile devices are critical to moving corporate operations forward. They’re also becoming a more lucrative target for malicious actors looking for access to your network.
Edge Computing Unlocks Innovations in Access Control
Solutions that combine hardware and software in one device present businesses with an additional opportunity to enhance their operations and cybersecurity while decreasing their total cost of ownership.

Modernizing a San Francisco Landmark with a Streamlined Security Dashboard
Nearly 100 years after its opening, the Bently Reserve building in San Francisco rolls out an integrated access control and video management system to improve security incident response.
