

October 2022
Your Cyber Response Plan Needs These 6 Components
Cybersecurity incidents are no longer a matter of if, but when. Building a good strategy and architecture to deter intrusions is incredibly important in reducing the frequency and severity of incidents, but there is no scenario where any organization is totally immune. That means that every organization must have a plan for what they will do in both their enterprise (IT) and operational technology (OT) environments in case an incident occurs.
‘Pen-Tested’ by a Hacker: What to Believe
Some criminals are posing as penetration testers, offering corporate security reports in exchange for ransom payments. Here’s how to spot the difference between who’s legitimate and who’s a con, and measures to take to protect your networks.

The Physical Ramifications of Cyber Response
Sixty-seven percent of surveyed incident responders reported experiencing stress or anxiety in their daily lives, while others said they experienced insomnia, burnout, and impacts on their social life and relationships.
Why Mergers and Acquisitions Don’t Need to be a Security Professional’s Nightmare
There are key security considerations for preventing cyber threats before, during, and after M&As. Here’s how organizations can gain visibility into assets to mitigate risks while making a deal.

The Evolving Tactics of BEC Attacks
Business Email Compromise schemes continue to flourish, suggesting it’s not a security problem but a business process problem.

Be Cyber Aware: ASIS Resources to Aid Your Organization
For National Cybersecurity Awareness Month, the ASIS Information Technology Security Community and the Security Applied Sciences Community partnered to provide resources and webinars to help make individuals more aware of the changing threat landscape.

Key Learnings from Log4Shell
The Log4Shell vulnerability is “endemic.” But there are steps companies can take to secure the open-source software supply chain and shore up the security of the Internet.
Software-as-a-Service Applications Create a Growing Attack Surface
With several incidents in 2022 leveraging prominent Software-as-a-Service applications, experts warn that this is a trend that is likely to continue to pose a risk. Here are some simple steps to help mitigate the risk of these kinds of attacks at your organization.

Speco Technologies’ NRN Series are NOW UL 2900 Listed!
Speco Technologies is proud to announce that our NRN Series of network video recorders with advanced analytics have passed rigorous testing and now carry Level 1 UL 2900-2-3 cybersecurity certification.

Availability First Achieves More Positive Outcomes. It’s a Mindset!
If we want to change the narrative around cybersecurity to achieve more positive outcomes, then we must change the way we lead.

Employees: The First Line of Defense Against Cyberattacks
Approximately 20 percent of burned-out employees said the security policies for the companies they work for “aren’t worth the hassle.” This is not the attitude you want from the people who should comprise your first line of defense in cybersecurity.

Three Key Considerations for Building Threat Assessments
With today’s business climate and the types of threats constantly evolving, having real-time insight into threats can tangibly move the needle in improving a company’s overall reputation and outlook.

Cyber Insurance Hard Market Turns Brittle
Insurers are in danger of failing to turn an underwriting profit on what had three years prior been an exceedingly profitable product.
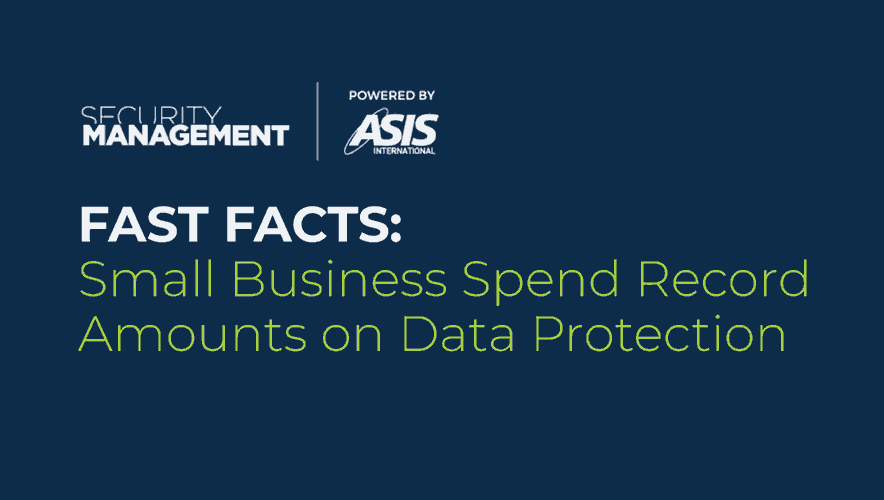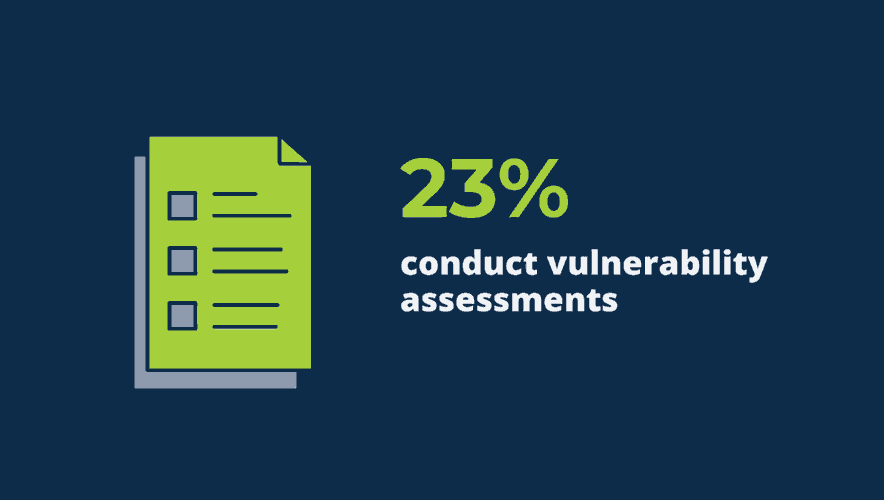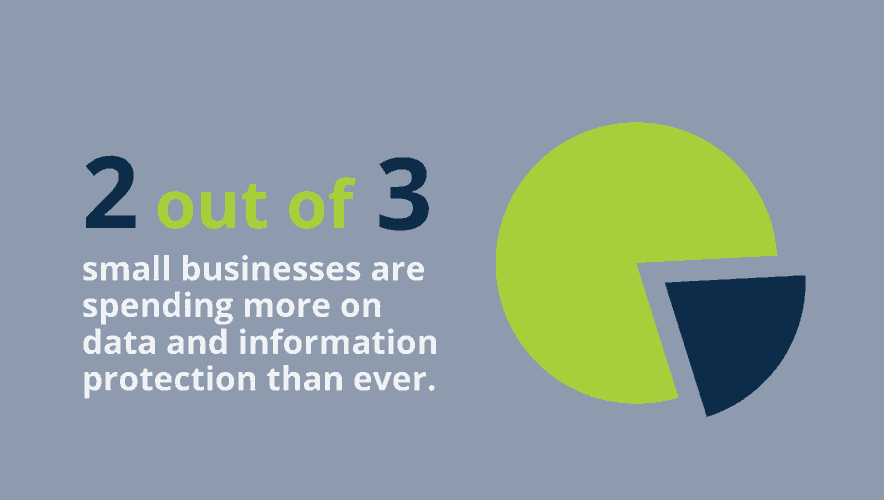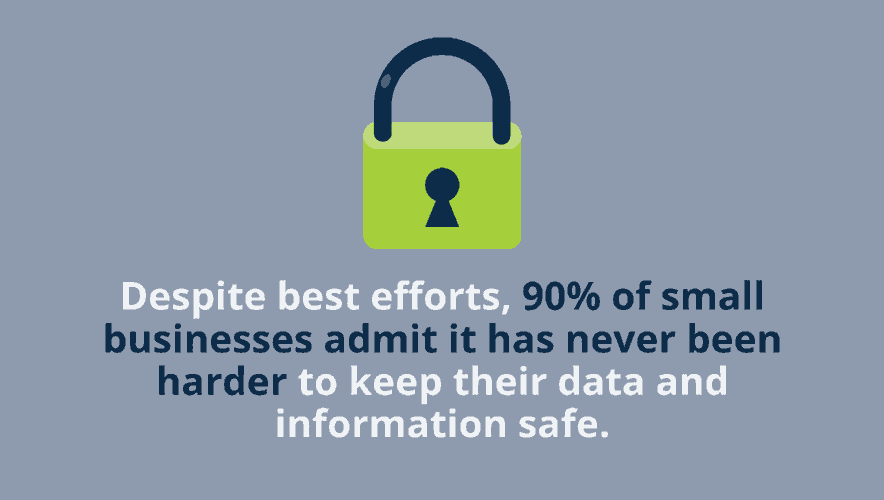
Fast Facts: Small Business Spend Record Amounts on Data Protection
Small business are spending record amounts to protect their data, in both physical and digital form, according to an annual survey. Our Fast Facts video breaks down what measures they're putting into play.

How to Harden Security Infrastructure Against Attacks
Studies and industry security alerts have shown that most organizations do not sufficiently harden and protect physical security systems. Here’s some guidance to get started on enhancing the security of your organization’s security system assets.

Going Nuclear: Watchdog Identifies Major Cyber Risks
A recent U.S. government watchdog audit found that the administration responsible for maintaining the U.S. nuclear stockpile has not fully implemented six key practices for a cybersecurity management program.
