Getting Visitor Management Right in Access Control
At its most basic level, an access control system is supposed to efficiently allow access to those with permission to be there, while denying access to those without permission. The complexity of this foundational aspect of physical security increases significantly when developing a system to accommodate various types of visitors.
That’s why when ASIS undertook a detailed research project examining access control systems in late 2023 a major consideration was how organizations approached visitor management. The final report, The Essentials of Access Control: Insights, Benchmarks, and Best Practices, sponsored by iLobby, examined visitor management along with several other aspects of access control. This article expands on the visitor management section of the report, providing additional analysis and context.
One note—for purposes of the research, ASIS defined an access control system as both the technology deployed to restrict access and the policies and procedures that supported the effort.
The Complexity of Dealing with Visitors
The fact that visitor management is a pain point for security professionals was highlighted in the study by an open-ended question asking participants what they would change about their current access control system. Omitting the words “access,” “control,” and “improve,” the word “visitor” was the third most-used word in the responses. Many hated the paper-and-pencil process they used to manage visitors and wished for a more sophisticated solution. Others wanted more restrictive policies. Some wanted a quicker, less resource-intensive alternative to their current approach.
It's no surprise that visitor management causes so much consternation. The ubiquitous term “visitor” covers a lot of ground and includes such varied scenarios as a prospective client coming to a facility for an hourlong meeting, an HVAC contractor coming to diagnose a problem that might take three hours or three days to fix, accounting auditors who need facility access for a month, a family member visiting an employee, a short-term temporary worker, an inspector, and the list could go on and on. Each individual visitor has varying levels and durations of access need.
Frazier R. Thompson, IV, CPP, is the deputy chief security officer with International Paper, the largest paper-producing company in the world. The 125-year-old company has 39,000 employees at 250 facilities in 10 countries.
“You can imagine the challenge of standardizing all that,” he says. “How we’ve been doing it is slowly but surely conducting those internal physical security assessments. Visiting the sites to understand how their operations work, how they’re currently doing visitor access management. A lot of our sites are doing what you would anticipate—paper logs—most of them are still doing that… What we’re doing is trying to move to and implement a more electronic standard to make it more efficient.”
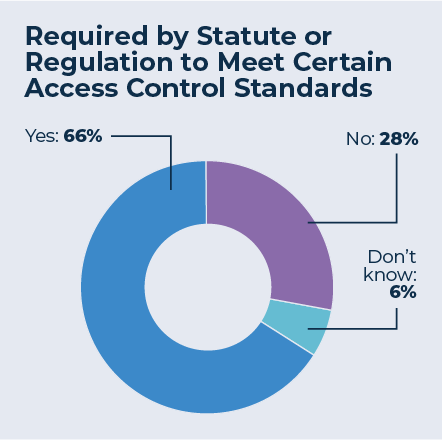
Getting visitor management right is not just a security issue; it is a business imperative for most places. Two-thirds of those surveyed said they were required by statute or regulation to meet certain access control standards, and most of those access control standards include accounting for visitors.
“One of the biggest issues for us is to make sure that everybody that comes on one of our sites is, not only are they secure, but they are safe as well,” Thompson adds.
Benchmarking Visitor Management Policies
Despite the complexity that visitor management presents for organizations, some best practices are elegant in their simplicity.
Don McInnes, PSP, a longtime security professional and consultant, describes one simple idea. “You change the horizontal or vertical alignment of [identification badges],” he explains. “So, if your employees have horizontal cards, you give your visitors cards with a vertical alignment. It’s easily distinguishable, you don’t have to train the employees to look closely at the card. Large sporting events might use such a policy for event staff or vendors or contractors or caterers so that anybody can, at a glance, see that it is this year’s badge because it’s horizontal, and then the next year they flip it. Something as simple as that can be an effective part of visitor management.”
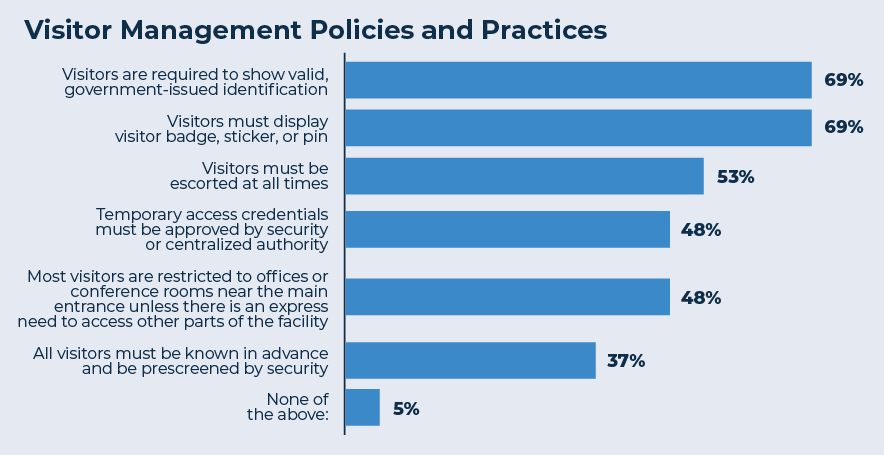
The survey research provided a list of common visitor policies and practices, asking participants if their organizations used them. Almost all of them were in place in almost half of organizations. The most restrictive item on the list, “all visitors must be known in advance and be prescreened by security,” was least prevalent, cited by 37 percent of participants as in place in their organization. The two policies that were most prevalent, both by just more than two-thirds of participants, were visitors needing to show valid identification and visitors needing to wear and visibly display a visitor badge while on site.
McInnis’s example and the policies presented in the ASIS research are broadly applicable to many different sectors. Many, if not most, organizations will also tailor policies and practices based on the characteristics of the site. For example, with safety as a primary concern, Thompson says all of International Paper’s “manufacturing sites required high-vis vests, and at some of our sites they’ve gone a step further and have different color vests for visitors so our employees can watch that person closely, make sure they’re being escorted, and make sure they remain safe.”
Ross Johnson, CPP, is the president of Bridgehead Consulting, and he has extensive experience working with critical infrastructure organizations to improve their physical security practices. In the utility space, he says, safety is by far the paramount concern.
“The problem with visitors is they don’t know anything,” he says. “They don’t know how dangerous a high-voltage substation is. They don’t know there are places you can walk where the electricity will reach out and kill you if you get too close. The goal of access control in that environment is to keep visitors alive.”
Policies include safety briefings prior to accessing dangerous areas; ensuring they are escorted at all times and remain under constant supervision; and, similar to Thompson’s experience in paper plants, having visitors wear different colored hats so that employees can see who on-site is not experienced in the environment and can help try to keep them safe.
Benchmarking Visitor Management and Technology Practices
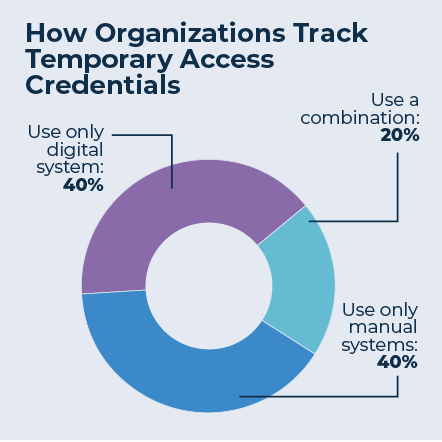
The bugaboo of visitor management is using a manual system to track visitors (or visitor credentials). Whether it’s an actual pen-and-paper system or a spreadsheet tracker—which is really just a pen-and-paper system masquerading as a digital system—40 percent of organizations use the method exclusively and, like Thompson at International Paper, another 20 percent use manual systems at some of their sites and fully digital solutions at others.
"I would love to have a visitor management system," says Parnell Lea, director of security and life safety at Brookfield Properties, which manages high-rise office buildings and is based out of Calgary, Alberta. "The problem is our buildings are open with numerous clients in each building. We would not use it for people visiting our clients, that would not be a workable situation. But a visitor management system would sure make working with contractors easier. We have our workaround systems, a paper process. We've had discussions with a couple of vendors, because we'd sure like to eliminate the manual recording, but so far, we haven't found a solution that meets our needs that would be worth it."
Of those who use manual systems or no system at all to manage visitors, 41 percent said adding a visitor management system was an explicit part of an upgrade plan. Thirty percent said the systems were cost prohibitive, and more than half said either they didn’t have enough visitor traffic to warrant such a system or that their risk assessments had not identified a visitor management system as a priority.
When asked how he advises prospective clients to approach decision makers to make the case for visitor management systems, iLobby Facility and Visitor Management’s Chief Revenue Officer Jeff Gladwish notes that it was better to make the case before an incident occurs as part of a risk management process. (Disclosure: iLobby sponsored the research, though ASIS retained full control over the project.)
Another point to make is the Fort Knox Inequity Syndrome. “One of our clients said, ‘We’ve invested in this really good access control system for our employees,’” Gladwish explains. “‘It’s like Fort Knox. We know who’s there, we know who’s coming in, we know who’s going out. And these are people we already know and already, for the most part, trust—our employees. And the riskier group—the visitors—the people who don’t come every day, who we don’t know, or don’t know as well, in some cases we let them into our facilities with looser security.’”
Thompson points out that his locations with a robust visitor management system are lightyears in front of the others in terms of efficiency and compliance with visitor management protocols. It’s important to “frontload anything you can during that preregistration process using an electronic system,” he says. “You can frontload those [nondisclosure agreements (NDAs)], you can frontload any training necessary. Before that visitor even shows up, they sign the NDA, agree to abide by your safety protocols, watch any training you have, they’re aware of any [personal protective equipment]. It just speeds up that registration process, so when they do arrive on site, they have a much better customer experience to get in and do their job and get out.”
Visitor Management-Related Factors that Make Access Control More Effective
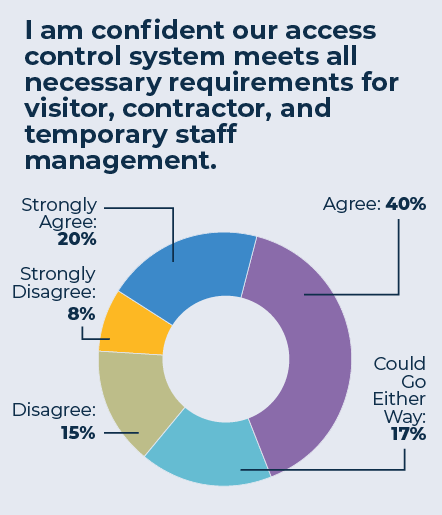
The research showed that overall, access control systems are highly effective. Even at large, multisite organizations, security professionals reported very few incidents. To measure effectiveness, then, the research turned to questions that asked security professionals to rate their confidence in the effectiveness of their systems on a five-point scale. Even in this rating, access control systems performed well. For example, when asked to rate the statement, “I am confident our access control system meets all necessary requirements for visitor, contractor, and temporary staff management,” the breakout was fairly positive, with 60 percent either agreeing or strongly agreeing.
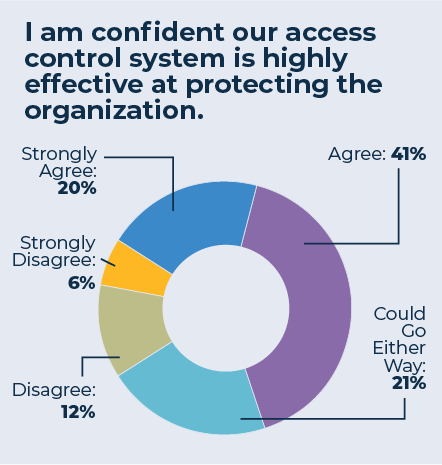
Similarly, survey participants rated the statement, “I am confident our access control system is highly effective at protecting the organization.” The distribution of results was similar, with 61 percent agreeing or strongly agreeing.
Comparing how respondents answered the highly effective question with other questions in the survey, however, gave ASIS a picture of the characteristics that improve the confidence security professionals have in their access control systems.
For visitor management, 41 percent of respondents said they had integrated a visitor management solution with their access control technology. Seventy percent of those with the integration either agreed or strongly agreed that their access control system was highly effective overall. Among those without such an integration, the percentage who agreed fell to 54 percent.
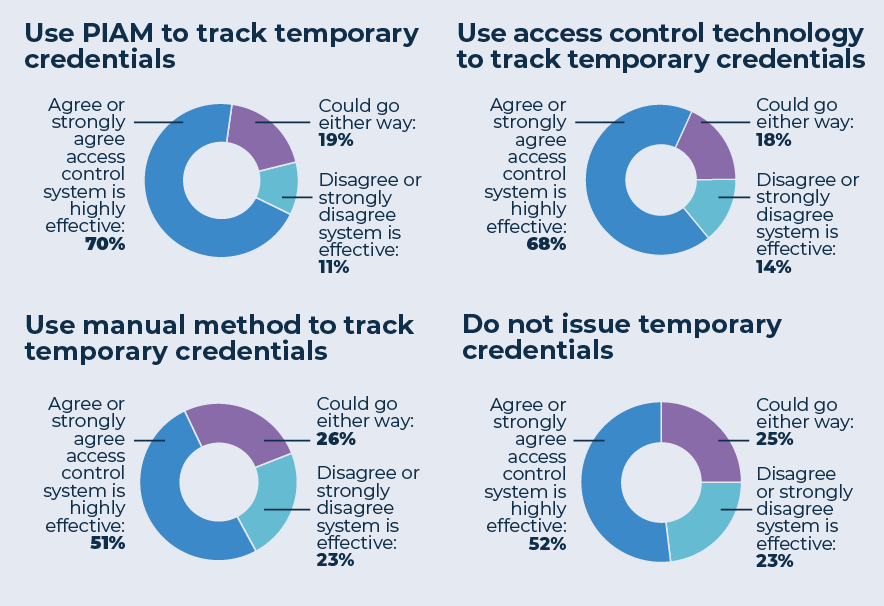
Similarly, looking at the different ways organizations used to track temporary credentials showed that security professionals with more sophisticated means, rather than a system that employs pen-and-paper record keeping, were more confident in their system.
Another question asked if the organization could track in-and-out access for people in their facilities: 48 percent said they had that capacity for all people in a facility, 14 percent had it for staff only, and 39 percent did not have in-and-out tracking capacity at all. It turns out that this was one of the stronger correlations on the effectiveness measure. Of respondents who could track everybody, 73 percent agreed or strongly agreed their access control systems were highly effective, versus only 45 percent of those who had no in-and-out tracking capability.
While technology solutions added to security professional confidence, every practitioner, consultant, and vendor who worked on the project emphasized that the human aspect is the most important element to access control systems—and that includes for the visitor management components.
“If the process is inefficient, it only increases the likelihood that people will find a way around it,” Gladwish says. “The access control system might meet the minimum standard necessary, but it needs to be efficient and cost-effective, too.”
It’s no surprise, then, that the top access control policy or procedure practiced by participants in the study was emphasizing access control policies as part of employee orientation (75 percent).
“A system’s only going to be successful if your employees understand the safety and security reasons behind your system and buy into it,” McInnis says. “If you’ve got resistance, there will be people who pay no attention to your policies and procedures and your system will fail. Training on the system, on security awareness, is critical.”
Methodology of the Research
ASIS empaneled a small group of members, with a representative from the sponsor iLobby, to develop a survey instrument to study access control systems. The survey was deployed in September 2023, primarily to ASIS members, but it was also promoted publicly via social channels.
A total of 1,022 participants answered at least some questions, and 735 participants completed the survey by answering the last question possible. All responses were included in tabulations. For most questions and analysis, the margin of error is ±4 percent at the 95 percent confidence interval. See the report for more information on the methodology and demographics of the survey.
Scott Briscoe is the content development director for ASIS International. He served as the project lead for the research and was the primary author of the resulting report.