What’s Important About Access Control Systems? Consultants Weigh In
For the first time in an ASIS research project, security consultants were given the option to participate as if they were employed directly in security by organizations or take a separate survey to gauge consultant opinions and attitudes on the topic—in this case, access control systems. More than 70 elected to answer the alternate set of questions.
The research project was sponsored by iLobby, and some of the consultant question findings made it into the final report on the survey, The Essentials of Access Control: Insights, Benchmarks, and Best Practices. However, this article is the only comprehensive look at the consultant results.
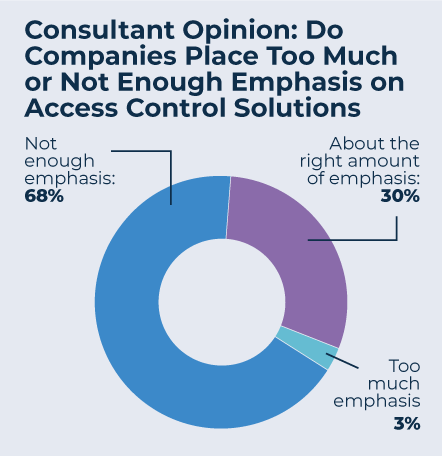
Access control is a ubiquitous part of every physical security portfolio. Every security manager, director, supervisor, guard, and executive—everyone involved in physical security—touches or is influenced by the access control system in some way, often on a daily basis. Still, when asked if companies paid enough attention to access control solutions, two-thirds (68 percent) of the consultants said they did not.
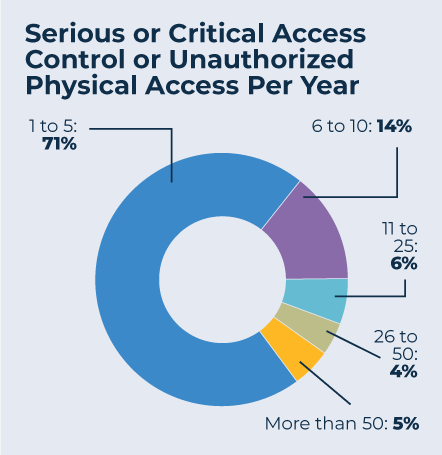
The good news is that access control systems by-and-large are very effective. In the main survey, security professionals were asked how many critical or serious access control or unauthorized physical access incidents they faced each year. More than 70 percent said they only faced one to five such incidents. Most of those who reported more than 10 incidents per year were from large, multinational organizations.
Despite the overall effectiveness of access control systems, security professionals reported a fairly high prevalence of minor issues. For example, more than half said they had experienced tailgating or piggybacking incidents (61 percent) or propped doors (50 percent) within the previous month. Other incidents, including card sharing (38 percent), visitor attempts to circumvent procedures (32 percent), and deliberate staff attempts to circumvent procedures (32 percent) were also significant issues. It is likely these are the kinds of incidents that consultants had in mind when they said companies did not emphasize access control enough. Major incidents are more likely to occur when these minor infractions are prevalent.
According to Don McInnis, PSP, a security consultant who helped ASIS develop the research project, “The problem is, they basically install it in forget it, and they never come back and revisit things. …People can get real used to propping a door open or holding a door open, negating the whole purpose for the access control.”
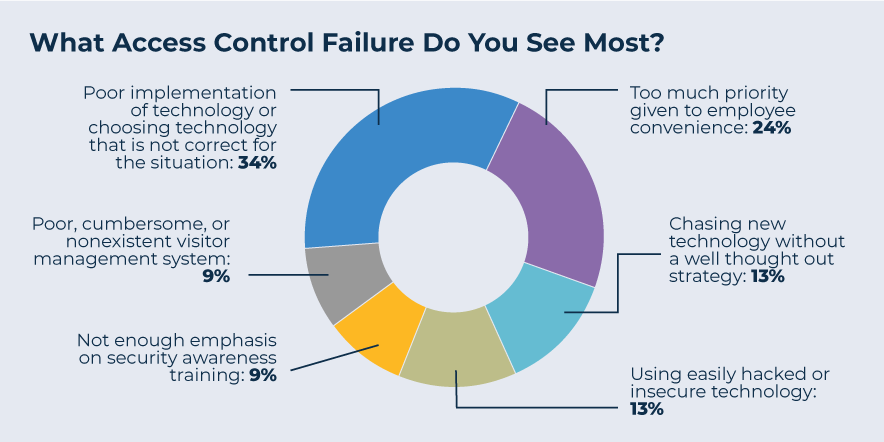
The survey also asked consultants what access control failures they saw most often. Poor implementation of technology topped the list, followed by giving too much priority to employee convenience. A lack of security awareness training or inadequate visitor management systems were much lower on the list.
Finally, consultants were decidedly lukewarm when assessing how well practitioners used access control data. Just under a third said they “do the bare minimum” or “do a very poor job.” Also a little less than a third said they do a good or excellent job, with the rest saying they do an adequate job.
The survey also asked consultants to rate how important certain technical innovations and certain policies and procedures are to effective access control.
The most highly rated technical innovations were “access control system integration with surveillance system,” “linking access controls to critical systems such as IT access,” and “using multifactor authentication for access control.”
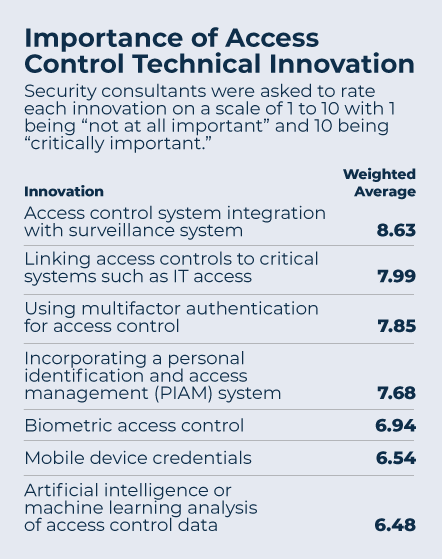
These results mesh pretty well with findings from the security professional part of the research. Video surveillance devices were in place at main entrances for 85 percent of organizations and at secondary entrances for 84 percent. In addition, 54 percent of respondents said their video surveillance and access control systems were integrated, significantly more than the second-most integrated system, visitor management, at 42 percent. However, far fewer organizations have linked IT access and physical access, only 22 percent. Only 14 percent use mobile devices as access credentials.
The survey asked consultants the importance of three different policies or approaches to access control. All scored very well, but “incorporating access control into the overall security risk management plan” scored the highest.
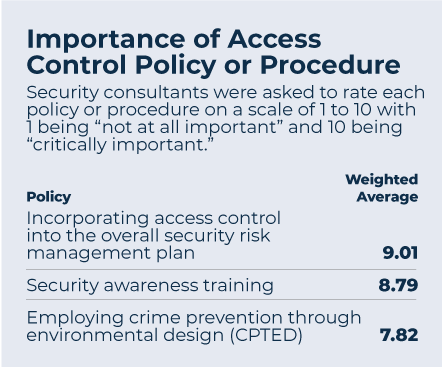
Just as with the technical innovations, the policy results from the consultants mesh well with the security professional opinions and approaches noted in the survey. More than 90 percent of security professionals said access control was an explicit part of a risk management or security plan at their organizations. Also, 75 percent report that access control policies are emphasized during employee onboarding, and 61 percent say they are reinforced with staff regularly.
Finally, the survey asked the consultants an open-ended question: What is the one piece of advice you would give to security professionals about access control? Sixty-two consultants answered the question. Several themes emerged among the answers: integrating access control systems with other systems is a business imperative; people are the weakest link of access control systems and there is no substitute for training; and the need to see the access control system as an important part of, but still only part of, a robust, layered security strategy.
Read on for a selection of the pieces of advice from consultants.
- Access control is part of an organizational strategy to protect the company's assets (property, people, information, and operations). As such, it is imperative to leverage your key organizational partners and stakeholders to establish the effort and gain support.
- Maintain the systems you have in place and work with an integrator that can help you get the most from your existing system while helping you prepare for future developments.
- Whatever system is implemented, it must be underpinned by a robust policy and supported with user training and auditing to ensure it is implemented as intended and remains effective.
- Know your clients’ risks and risk tolerance.
- You must partner with IT as it relates to your devices. The blending of physical security and IT security is here and real.
- Emphasize security awareness training; incorporate access management policy/procedure and development/implementation into risk assessment so you understand system’s impact.
- Physical security is best designed in a layered approach where we start at the perimeter and work the plan inward to the most critical zones; we next implement the layered approach with CPTED, good mechanical hardware, then electronic intrusion detection, video surveillance, electronic access controls, and then implement analytic solutions that help provide competency improvements to the overall business.
- You cannot always fix human problems with technology. A unified approach that balances human, procedural, and technological advancements capitalizes on each of those and makes the most of the overall experience.
- Access control is the bedrock of the security framework. Once you fail in access control, you fail in all. Professionals should therefore choose the access control that best suits their application. It is often said that application determines the equipment.
- Choose a solution that gives security operators real-time data insights, such as authenticated users in the building, peak usages of systems, failure rates, etc., and allows security operators to better manage risk and provide more situational awareness.
- It must be implemented with a hierarchy of controls from softest controls to most restrictive. Not one solution for all levels of protection.
- Design simple systems with redundancy that people can use effectively.
- Stop looking at just the cost as the deciding factor. Look for a system that can grow and be expanded to meet the needs down the road not just for today and listen to other security professionals and consultants as subject matter experts. Take the advice they give you and really use it. Learn from them and your past mistakes and do better. An ACS company sales force is not a subject matter expert, they are there to move product. Sell ACS to the C-suite as an investment or capital improvement for the whole company's benefit and have a more realistic replacement budget.
- You have to pick your battles. Watch out for use of inappropriate security measures in the wrong place—either too stringent or too casual can cause problems.
- Perform a strategic analysis of your needs for access control with a focus on building a 15-year plan, and, if the size of your operation is big enough (over 100 readers), definitely plan for PIAM. The key to your enterprise is not the card/credential, it's the identity.
- Regularly auditing electronic access control system permissions to specific areas to ensure only those with a demonstrated need-to-access can enter is a critical component of effective access control. Regularly reviewing audit logs more broadly can provide a wealth of information on who is accessing your sites/areas and how they are doing it.
- Don't do the same old thing you've always done because it's comfortable. There is so much information out there on how to defeat systems that we must always stay aware of our vulnerabilities and how to currently best mitigate them.
Methodology of the Research
ASIS empaneled a small group of members, with a representative from the sponsor iLobby, to develop a survey instrument to study access control systems. The survey was deployed in September 2023, primarily to ASIS members, but it was also promoted publicly via social channels.
A total of 1,022 participants answered at least some questions, and 735 participants completed the survey by answering the last question possible. All responses were included in tabulations. For most questions and analysis, the margin of error is ±4 percent at the 95 percent confidence interval.
See the report for more information on the methodology and demographics of the survey.
A total of 71 consultants elected to answer an alternate set of questions geared specifically at security consultants. The small sample size means that data derived from the questions have a high margin of error and should be considered more as a broad approximation of survey consultant attitudes than statistically rigorous results.
Scott Briscoe is the content development director for ASIS International. He served as the project lead for the research and was the primary author of the resulting report.