Intelligence to Address Extremism: Look for What Matters Most
We are currently seeing a rise in extremism and hate-related criminal activity that has not been seen in decades. The U.S. Government Accountability Office found that incidents of domestic terrorism increased 357 percent between 2013 and 2021 in the United States and that racially or ethnically motivated violent extremists committed the most violent attacks during that period. Hate crimes reported by law enforcement agencies to the FBI rose from more than 8,000 in 2020 to nearly 11,000 in 2021.
In Europe, hate speech and hate crime are thriving on social media, driven by a perception of increased migration, economic and social crises, the proliferation of conspiracy theories, and the stressors of the COVID-19 pandemic, according to a European Parliament report.
While the global number of war deaths has been on the decline for decades and the number of deaths attributed to terrorism continues to decrease, extremist groups are thriving and the number of terrorism- and extremism-related incidents is increasing, noted the United Nations. Heightened political tensions and rhetoric, multiple wars, and the use of social media have led to a level of societal conflict that leaves many of us wondering what we do next.
For the security professional, this isn’t just an academic exercise or discussion to be avoided at family gatherings during the holidays: it poses a significant challenge to protecting the enterprise and its employees from what could be some very aggressive actions. Fortunately, there are tools already at hand to help you better understand your adversary and mitigate those risks.
The Intelligence Cycle
Anybody who’s familiar with the basics of intelligence will recognize “the wheel,” as it is often called. The intelligence cycle comprises six steps: targeting, collection, storage, analysis, reporting, and retargeting. These are the steps you can use to gain a better understanding of the extremists that may be focusing on your organization. By applying this cycle when addressing the risk of extremism, you can get a more accurate picture of the risk your organization and its stakeholders face.
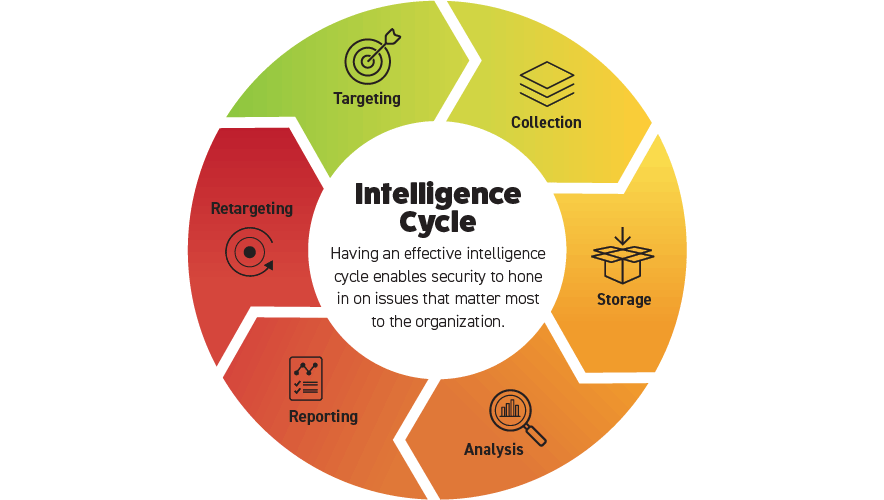
Targeting
The first step, targeting, is the most critical step and depends on your perspective and unique needs. Determine what you want to know and by when. Information that arrives too late is really of no value. Additionally, the level of the information needed will crucially affect where you search.
For example, at the strategic level you may be asked by your executives to provide a broad picture of the risk extremism poses and how you can address it. This will change your targeting significantly, because you will be looking at larger issues with a focus on a wider view, keeping executives’ needs in mind. For those working in organizations with a retail- or customer-facing operation, you may wish to take a more tactical view of the threat at the street level.
The key is to understand what is needed and by whom, and that requires you to have a conversation with the stakeholders. Often you can use this as an opportunity to identify potential challenges that had not manifested before.
During a conversation a colleague had with a key regional leader in his company, he began to realize that they were getting a great deal of pushback at the retail level regarding the company's policies and efforts on diversity, equity, and inclusion. Specifically, they were getting aggressive feedback at the retail level about the organization’s support for LGBTQ customers during the most recent Pride Month.
When that negative feedback was initially reported, it appeared to be a client/customer on employee threat (classified as a Type II threat by the U.S. Occupational Safety and Health Administration). However, through the conversation with the regional leader, the risk quickly revealed itself as an extremist challenge to the company, abruptly changing the focus and goals of intelligence targeting efforts. This discovery caused the company to develop better goals.
When setting goals, remember the acronym SMART: specific, measurable, attainable, relevant, and time bound. Just as you would use this approach to develop measurable key performance indicators for your security operation, it also can be applied to developing your target list.
Specific. What is the exact information that you are trying to find? Has your organization been the subject of discussions by hate groups in social media? Is there a pattern to the action? Have there been protests in front of your organization? Who are the groups conducting the protests? All these elements go into determining the precise information you need.
Measurable. As with any goal, your targeting should be something that you can quantify or explain. If you can't explain it quantitatively or qualitatively, it probably should not be an area of focus.
Your own internal incident reporting system can be very helpful here. Go back through previous reports. Are there incident reports that were filed under “workplace violence” but may in fact be indications of extremist targeting? Work with your human resources team to determine if they are hearing concerns from employees. Very often this information is transmitted through channels other than security or intelligence. This internal review can determine how you can accurately measure your risk in this area. Measurability allows you to place the risk in context, which is key to stakeholder comprehension.
Attainable. The nature of the information you can attain affects your ability to manage your stakeholders’ and leadership’s expectations. It is not uncommon to get requests for information that cannot be lawfully obtained, and in some cases, you may have a great deal of pressure placed on you to find this information.
In many countries, particularly in Europe, the laws governing privacy and far more restrictive; even completing a simple criminal history check can be a serious violation of a national law. Within the United States, restrictions can vary significantly from state to state, and getting this wrong can have major consequences for the organization, regardless of your good intentions.
We are all aware of major organizations that have engaged their security team in actions that were seen as unethical or unlawful. These often become visible in the public media, and the reputational harm will more than likely exceed the value of the information gained.
As you’ve probably done when discussing risk mitigation with stakeholders, you want to address what you can achieve and how fast you can achieve it. That honest conversation will require courage, but in the long run it is in the interests of leaders and their organizations. Additionally, attainable information is frequently available without violating legal or ethical standards.
As the professional who knows your business, you are the one to help guide leadership through the decision-making process to make sure what they do is done properly and lawfully. Consider engaging your legal team when addressing this issue as well. The legal department can bring the creditability of their profession when looking at what is attainable.
Relevant. Is this information essential to or helpful in developing a better picture of the risk your organization faces? Are you asking questions that meet the identified statements of the stakeholders? It’s important to keep information relevant if you want the reporting to be accepted. There is a great deal of information out there about hate groups and extremism. Weed through this material and look for specific information that can help shed light on what is important to decision makers.
Time bound. Providing information that is five minutes too late is as bad as not providing it at all. The key to success here is to get a specific date from your stakeholders for when they need this information. Often, when you ask this question, you’ll hear "Just get it to me as soon as you can.” That ambiguity is an almost certain recipe for frustration and disappointment.
When talking to your stakeholders, keep in mind the amount of time required to assemble and analyze this information. That needs to be built into the discussion so that you can provide them with an accurate recommended date. Executives often can be quite demanding about timely information and may set a timeline that is not realistic based on your analysis of the situation. Make the leadership aware that a short timeline will significantly affect the quality of the report.
Collection
Collecting the information will depend on the type of intelligence you are trying to locate. Regarding extremist groups, you most likely have access to this information already.
The easiest place to start is open sources. Use organizations that already spend a great deal of time studying this material. Leverage data from the FBI and various non-profit organizations focused on hate group and extremist activities, such as the Southern Poverty Law Center’s Hatewatch, the Simon Wiesenthal Center Digital Terrorism and Hate Project, and the Anti-Defamation League H.E.A.T Map. Information from these programs can be combined with that of your contacts in law enforcement and professional colleagues, who can be excellent sources.
Storage
You need to have a system for storing the information so that it can be properly digested in the analysis process. Consider what processes you already have that you could copy or repurpose. Often your investigative processes include the creation of a case file. If you use the same process that you use for an investigation, you could assemble the information in a simple and easy-to-use format that your stakeholders and team are already familiar with.
Analysis
Certainly, the most time-consuming element of any intelligence cycle is the analysis portion. But you may have people and processes in your organization that can make this step much easier. Start with your investigative team. Good investigators are often very good intelligence analysts. They know how to ask questions and challenge assumptions, both highly prized skills for analyzing data.
A complicated investigation may require committing more resources to analyzing extremist activity as it relates to your organization. It’s not uncommon to have a lead investigator and four or five additional investigators working a case. Why can’t we apply the same process when analyzing extremist group activities? Security departments do not have a lot of analytical resources, but often they have people who can focus on one specific element of the analysis.
For example, have a manager analyze all of the hate group activity data available in your area from the FBI and produce a subsection report on it. Assign a separate manager to go through all the incident reports looking for unreported indications of hate group activity that were overlooked. If you have access to intelligence vendors, you can solicit information from them, and they will produce a report for you. All these methods can help you produce a product that is both accurate and useful to the decision maker.
Reporting
Reports need to be written specifically with the audience in mind to avoid confusion. Who will be reading your report? That is the most important question you need to ask and should be the first one addressed. Understanding the amount of time, effort, and interest they have in the subject matter will help you tailor the report accordingly.
One effective method is to use a reporting style with which your audience is already familiar. Many of us have provided enterprise security risk management (ESRM) reports for our stakeholders. If that is the case, you can leverage this. Effectively, an extremist activity report is a risk report. Breaking it down into a risk and recommended response format can result in a reporting system that makes it easier for the stakeholders to understand what you are telling them and what they can do about it.
For example, suppose you are asked about the risk that ecoterrorists can pose to a key timber processing plant that generates a high-margin product used in packaging and shipping. Using the ESRM asset owner and stakeholder process, you identified the key concerns and refined your targeting. In this case, infiltration attacks through routine hiring and third-party vendors represent a major concern for the leadership. Now the report can be written using the identified risk and mitigation options format, and you will provide the decision makers with a better picture of what could happen and how it can be mitigated.
Retargeting
Retargeting is probably the most overlooked step in the intelligence cycle, but it is highly important when looking at extremism and hate groups. These groups are flexible, their strategies evolve, and the risks they pose are dynamic. During your reporting, you may find an area that requires additional focus.
If your report is effective, stakeholders will have a better understanding of the information they need—which typically results in follow-up questions that require retargeting. This combination can work to your advantage, enabling you to take existing data and concentrate on specific concerns.
In conclusion, security professionals can bring order and understanding to the chaotic situations produced by extremist and hate groups. Using these tools, what you have at hand, and what you already know can result in an improved understanding of the risk for your leadership. It is this knowledge that allows them to make informed decisions and you to accomplish your goal of being a trusted advisor and solution provider.
The process is not complicated. When implemented properly, it produces results that help you accomplish your primary mission—protecting your people and company from harm and alarm.
Ralph “RC” Miles, CPP, is the global director of safety and security for the AIDS Healthcare Foundation. He has more than 25 years of private sector experience in the design, development, and implementation of comprehensive security, investigations, and intelligence strategies in a variety of business climates and organizational cultures. Prior to his civilian career, Miles spent nine years as an officer in the U.S. Army in various assignments around the world. He serves on the board of directors of the CSO Center.