Follow the Money: How Digital Currency is Changing Crime
In investigations (and in journalism), those with experience will tell students to “follow the money.” And when looking into criminal actors or organizations, the money trail can often illustrate illicit methods, such as bribes, transportation of goods, services, and more.
However, the form of money leveraged in illicit activities has changed in recent years. Currency was traditionally established as either an item backed by a physical commodity, like gold or silver, or by the government issuing the item (also known as fiat money), like most modern paper currencies.
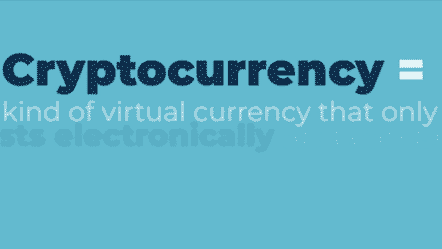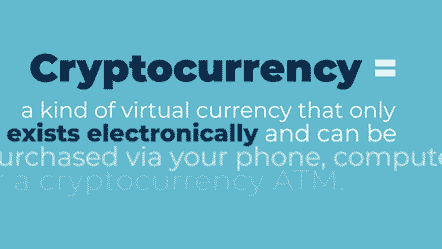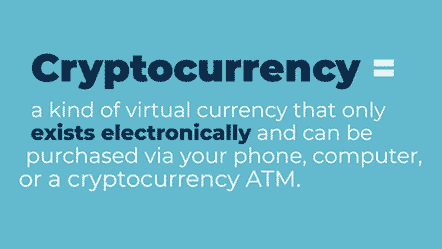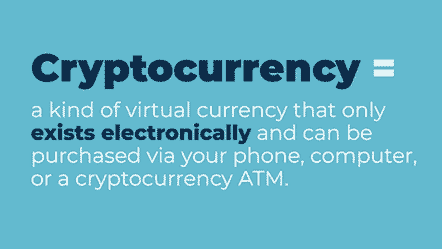
One modern form of currency is a digital asset, or cryptocurrency. Cryptocurrencies are usually not issued by a central public or private authority; instead, these digital currencies were independently created to pay for services or goods. Myriad ones exist, such as Bitcoin, XRP, Ethereum (ETH), and Dogecoin, and many depend on blockchain technology.
Cryptocurrency users found a preferred advantage in digital assets: they were no longer relying on a centralized financial institution to support transactions. So, if a financial crisis occurs, some have argued that the funds invested in digital assets will retain their value.
Criminals seeking to keep their profits out of regulated institutions have also found advantages to digital currency.
“U.S. law enforcement agencies have detected an increase in the use of virtual assets to pay for online drugs or to launder the proceeds of drug trafficking, fraud, and cybercrime, including ransomware attacks,” according to the 2022 National Money Laundering Risk Assessment by the U.S. Department of the Treasury.
“It’s an alternative way to pay for traditional acts of crime,” says Celina Realuyo, lecturer at The George Washington University and expert in counterterrorism and threat finance issues in the Americas.
Cryptocurrency Crimes
Digital currency plays a role in many crime trends and illicit activities today, and its use cases just keep growing.
Illicit marketplaces. Although it was not the first such site, The Silk Road was relatively popular and supported by more than 100,000 buyers before being taken down in 2013 by the FBI.
The Silk Road was an online black market website that allowed anonymous users to buy and sell products and services using digital currency. Since its shutdown, other Dark Web markets have emerged—some of them rebranding as later versions of The Silk Road. Law enforcement agencies worldwide have tried to target these marketplaces, as they often connect disparate crime rings and schemes.
Recently, a coordinated effort between Europol, Australia, and the United States seized an illegal Dark Web marketplace called Monopoly Market. As part of the seizure, dubbed Operation SpecTor and publicly disclosed on 2 May 2023, law enforcement agencies arrested 288 suspects involved in buying or selling drugs and confiscated more than €50.8 million ($53.4 million) in cash and virtual currencies, 850 kg of drugs, and 117 firearms.
Many illegal domains are supported by cryptocurrencies, according to the International Monetary Fund (IMF).
“Recreational and pharmaceutical drugs are the most popular products, followed by stolen and counterfeit documents such as identities, credit cards, and bank credentials. Some sites offer hacking and technological crime services, including malware, distributed denial of service attacks, and hacking for hire,” the IMF said in a 2019 article.
One reason cryptocurrencies are relied upon by these websites’ users is because they provide at least some screening of the user’s identities, partially hiding them from law enforcement.
U.S. law enforcement agencies have detected an increase in the use of virtual assets to pay for online drugs or to launder the proceeds of drug trafficking, fraud, and cybercrime, including ransomware attacks.
Ransomware. After an attacker has infiltrated an organization with ransomware, the victim is often instructed to pay a ransom in the form of a digital asset, allowing the attacker to redirect the funds into other accounts in their control. This allows attackers to move payments, which can then be used to purchase goods, services, and even better ransomware. Using digital assets for payments enables the attacker to obfuscate the origin of the funds more easily.
When a U.S. organization is attacked with ransomware, it can request support from the U.S. Secret Service, the agency responsible for protecting the financial integrity of the nation. According to Matt O’Neill, deputy special agent in charge of cyber for the Secret Service, the agency can provide guidance and help coordinate investigative or response efforts with the FBI and the National Cyber Investigative Joint Taskforce.
The Secret Service, however, strongly discourages paying a ransom in instances where extortion is involved (such as when the data has been stolen instead of encrypted) because there is no guarantee that the attacker will not release potentially private or damaging data.
Scams. There are other forms of attacks on private organizations and individuals, one of the largest being crypto investment scams. These scams involve fraudsters luring victims either through blanket spam or targeted messages in emails or texts.
A rapidly growing type of crypto scam is called “pig butchering,” when scammers use elaborate storylines to build up a potential victim’s confidence and trust in the fraudster, potentially increasing the funds that the victim will send or believe he or she is investing. The term comes from scammers referring to the victims as pigs, who are “fattened up” in the sense that they are duped into believing the fraudster.
Once the victim trusts the scammer, he or she will make an investment in a cryptocurrency platform that has a veneer of legitimacy. But in reality, the victim is sending the fraudster virtual funds that will never be reinvested or returned.
“Butchering” occurs when the “victim assets are stolen and ultimately cause victims financial and emotional ruin,” according to the Secret Service. And it’s easy to imagine that this kind of scam can take a significant toll—the average reported loss is $2,600, according to the U.S. Federal Trade Commission.
Altogether, crypto scams, ransomware, and social engineering frauds resulted in more than $3 billion stolen in 2022 from U.S. consumers via blockchain-based entities, according to Michael Jabbara, vice president and global head of fraud services for Visa. Speaking at the RSA Conference 2023, Jabbara noted that crypto phishing scams—reaching out via text or email—can appear legitimate if you don’t know what red flags to look out for.
Virtual kidnappings. Like ransomware attacks, in a virtual kidnapping—where someone pretends to have kidnapped a family member and then demands a ransom over the phone or through a computer—the attacker asks that ransoms be paid in a digital currency. The funds are then reinvested in tools for future virtual kidnappings. These tools could include artificial intelligence-enabled solutions that can be used to perfectly mimic a person’s voice by relying on videos posted to social media platforms like Instagram or TikTok, according to Realuyo.
For organizations that have been targeted by a crypto fraudster—whether through an investment scam, ransomware attack, or other attack where digital assets were involved—O’Neill notes that preparations prior to these attacks are key.
Organizations should reach out to a cyber fraud taskforce, and U.S.-based groups ought to preemptively get to know a local Secret Service or FBI liaison, making that person part of an incident response plan.
“These trends and tactics change so much, that you have to have a plan in place when something bad happens,” O’Neill says.
Financing Alternatives
While digital assets themselves are not truly anonymous, cryptocurrencies do offer a way for entities to bypass U.S. sanctions that would otherwise hamper financial movements or operations. Because this kind of currency exists and operates outside of traditional banking systems, “a lot of our adversaries are using it as an alternative to the dollar,” Realuyo says.
Avoiding sanctions. Sanction enforcement depends upon the cooperation of traditional banking or financial institutions, but those entities are increasingly looking towards virtual funds. In its annual report on cryptocurrency crime, Chainalysis found that 43 percent of illicit use of cryptocurrency in 2022 came from activity linked to sanctioned entities.
Part of this jump was due to sanctions issued by the U.S. Department of the Treasury's Office of Foreign Assets Control (OFAC) in response to Russia’s war in Ukraine, including the April 2022 sanction of Russia-based virtual currency exchange Garantex.
“…While most of that activity is likely Russian users using a Russian exchange, most compliance professionals treat this as illicit activity,” according to The 2023 Crypto Crime Report.
43 percent
of illicit cryptocurrency use in 2022 was linked to sanctioned entities.
Overall, “sanctions-related transaction volume rose 152,844 percent from 2021 to 2022,” according to the Chainalysis report.
Another reason for the steep rise is that in 2021, OFAC began labeling some crypto services or groups with crypto-linked entities as bad actors instead of just individuals. These groups include Garantex, the Lazarus Group, and Hydra Marketplace. OFAC sanctioned Garantex and Hydra because of accusations of money laundering and offering services to criminals, including ransomware attackers.
Terrorism financing. Beyond sidestepping sanctions, criminal organizations like terrorist organizations and drug cartels are finding advantages in aspects of digital currencies, notably the ability to transfer and launder funds.
While the most common method to transfer funds remains through traditional banking systems and money wiring services, online payment platforms have increased in popularity because they lack the strict regulations of traditional banks that are subject to anti-money laundering rules.
“More layers are used to cover the transactions, which are taking place globally. For instance, cryptocurrencies are paid to an account in one country where they are withdrawn, the amount is divided and sent via hawala to other countries and further transferred via money transfer services,” according to Europol’s European Union Terrorism Situation and Trend Report 2023.
The Hawala system is a value transfer system where funds are sent from one location to another through service providers, known as hawaladars, according to the IMF. It is illegal in many EU member states.
“Terrorist organizations increasingly use digital currencies and virtual assets service providers (VASPs), as these provide a higher level of anonymity for donors and recipients,” Europol noted. “As regards to jihadism, IS and al-Qaeda and their affiliates appear to have stepped up the use of VAs (virtual assets), especially cryptocurrencies, for fundraising and the movement of funds in recent years, possibly as a result of an increased knowledge of VAs among members of jihadist terrorist groups. Right-wing extremists also resort to funding platforms operating with cryptocurrencies.”
Realuyo notes that digital assets’ ability to at least partially screen users from regulated financial systems also makes them attractive to terrorist organizations.
Money laundering. Drug cartels and organized criminal groups can launder their illicit funds by using digital asset service providers, allowing them to cash out in jurisdictions that lack effective international standards, according to the U.S. Secret Service.
Some organizations might have an in-house money launderer to reshuffle digital funds, but third-party launderers are available for hire in case the crime group has a digital skills gap.
And these money launderers who clean digital funds on a massive scale are the ones that can result in bigger impacts if law enforcement can disrupt their activities, dismantle their networks, and arrest them. O’Neill calls them the “centers of gravity.”
“There are a finite number of individuals around the world that can launder millions and millions of dollars,” O’Neill notes. “…When you take them off the playing field, that’s where you’re securely disrupting and dismantling organized crime.”
Sara Mosqueda is associate editor for Security Management. You can connect with her on LinkedIn.