Protecting Privacy and Corporate Data on Employee-Owned Mobile Devices
Our mobile phones today contain many things we hold dear: our photos, our financials, our contacts, and more. We use our devices for everyday life, which can include our daily work activities. With a powerful handheld computer in many of our pockets, organizations must manage corporate data while protecting the privacy of employees across the enterprise.
Knowing where to start when protecting these devices is vital for ensuring data security while maintaining employee privacy. As an increasing number of employees use mobile devices for work, it is important for leadership to be aware that modern mobile devices come with mechanisms that separate personal and corporate data.
Enterprise Mobility: The Security and Privacy Challenges
Imagine an employee is working from a local coffee shop. Without a secure device, a malicious actor can gain unauthorized access to private or proprietary information, with potential damage to the employee or even the entire organization. Considering that nearly 50 percent of data breaches are caused by inappropriate IT resource use by employees, it’s imperative that organizations employ effective security management platforms across the enterprise.
At the National Institute of Standards and Technology (NIST) National Cybersecurity Center of Excellence (NCCoE), we are aware that mobile device security risks require unique solutions that are different from traditional computing platforms. While some organizations provide staff with corporate-owned mobile devices, many also allow their employees to use personal mobile devices to perform work-related activities. This increasingly common practice, known as bring your own device (BYOD), provides employees with the flexibility to easily access organizational resources remotely. At the same time, this convenience also comes with added risk.
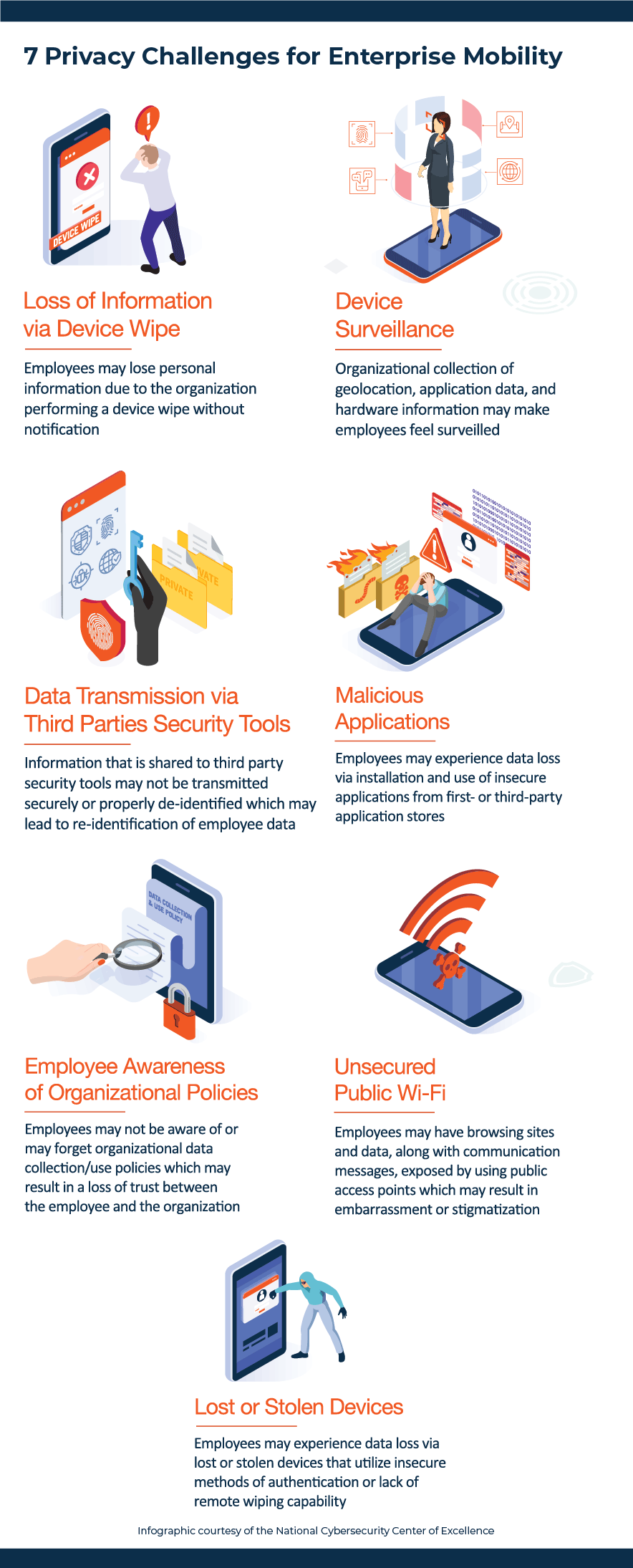
Privacy challenges can arise when personal and work data are stored on the same device. Organizations can mitigate privacy risks to employees and related risks to the organization (e.g., reputational damage or data leaks) by mitigating problematic data actions (PDAs) in its BYOD systems.
An example of a PDA resulting in an adverse effect might be data processing that causes embarrassment through the unexpected revelation of an employee’s personal data or the appropriation of personal data resulting in identity theft. Fortunately, resources are available today to help organizations improve their BYOD security posture while maintaining the privacy of employees.
Recommendations for Enhancing Mobile Device Security and Privacy Capabilities
There are several mobile security solutions today that can help ensure an organization’s work environment is sufficiently protected against data breaches and potential privacy risks. Here are three tools that organizations can use to strengthen the overall security posture of their enterprise environment:
Mobile device management (MDM): Allows organizations to secure mobile devices that are used to access organizational resources and may be included as part of a unified endpoint management (UEM) solution. An employee’s personal or corporate-owned device can be enrolled into an MDM solution to apply enterprise configurations, manage enterprise applications, and enforce compliance with enterprise policies. Enterprise administrators can also use MDM to manage and enforce policies on connected devices. If a device is found out of compliance with a policy, an organization can enforce a compliance action.
iOS and Android devices provide software-based separation between work and personal data. This prevents the enterprise from accessing personal information, such as location, apps, and personal data. When devices are enrolled into the MDM, a work profile is created that will store the enterprise data separate from personal information. MDMs can leverage this built-in separation to ensure they are only managing the enterprise data and do not disrupt the personal data.
Mobile threat defense (MTD): Provides real-time information about a device’s risk level. MTD can provide enhanced security when integrated with an MDM system. These integrations allow the MTD to report any risks back to the management software. In response, the management system can then act based on the identified risk and its potential impact to the enterprise.
Mobile application vetting (MAV): Used by enterprises to scan applications for potentially unwanted behavior. MAV can also be used to ensure that applications meet an organization’s security and privacy requirements. The tool uses a variety of static, dynamic, and behavioral analysis techniques to determine if an application demonstrates any behaviors that pose a security or privacy risk. Once analysis is complete, the tool generates a comprehensive report of the application’s security and privacy characteristics. The MAV report allows organizations to make risk-based decisions about whether to allow the use of an application.
Privacy and cybersecurity are two distinct areas, but when considering the risks of each, they often intersect. An organization can mitigate or prevent employee privacy problems and organizational risk through design decisions when implementing mobile deployment systems, such as BYOD.
Security managers can mitigate potential privacy risks by limiting data collection and isolating business applications from personal data sources (e.g., personal email or text messages). They can also notify employees regarding necessary business processing of personal information.
Lastly, managers can ensure proper data lifecycle management for any collected personal information, including strict data retention policies and proper disposal of personal information.
Considering the prevalence of employees who use their mobile devices for both personal and work activities, it is paramount that organizations prioritize the security of their mobile deployments. The good news is that security managers have access to a range of mobile security solutions that can help bridge the gap between organizational security needs and privacy concerns.
To learn more about maximizing mobile device security and privacy capabilities for BYOD, download the NIST Special Publication 1800-22 guide or contact us at [email protected].
Gema Howell is a computer scientist in the Applied Cybersecurity Division at the National Institute of Standards and Technology (NIST). As a project lead at the National Cybersecurity Center of Excellence (NCCoE), she develops reference architectures for enterprise mobile deployments. Her previous research efforts include investigating methods to securely manage mobile devices for emergency medical and fire services, and law enforcement.
Jessica Lauren Walton is a communications strategist, video producer, and writer in the U.S. defense sector. She has written articles on a range of security and mental health topics and conducted interviews with military leadership, psychologists, filmmakers, CIA officers, journalists, and more. To learn more about her work and forthcoming memoir, visit www.jessicawaltonwriter.com.
© National Institute of Standards and Technology