Rising Global Tensions and Financial Incentives Make Industrial Environments a Ripe Target for Threat Actors
Rising global tensions and increased financial opportunities are incentivizing threat actors to target industrial environments, according to an annual Operational Technology (OT) cybersecurity report published by Dragos this week.
“Cyber adversaries with a range of capabilities have used the Ukraine-Russia and Israel-Hamas wars to conduct targeted operations against critical infrastructure, and less sophisticated hacktivists have used the same conflicts to cause panic and negatively impact public perception of the resilience of critical services,” according to the Dragos 2023 Year in Review report. “Geopolitical tensions worldwide, including in Asia and Africa, have also driven intelligence gathering and capability staging activity.”
One of the threat groups that Dragos—and the U.S. intelligence community—is tracking closely is Voltzite, commonly known as Volt Typhoon. Dragos has tracked this group, which has targeted several critical infrastructure entities in Guam, the United States, and other countries since 2021.
“Voltzite has shown continued interest in the electric and telecommunications sectors in the United States, evidenced by the long-term reconnaissance of multiple electric entities,” Dragos explained.
Rob Lee, CEO and co-founder of Dragos, said in a briefing with reporters that Voltzite/Volt Typhoon is a “very well-resourced state actor” that is considered an “A-level team. It’s sophisticated, it can target infrastructure, and achieve its objectives.” The U.S. government has attributed the group as a Chinese-government based group.
The U.S. government released a joint advisory earlier this month on Volt Typhoon’s tactics, including its living-off-the-land techniques to maintain persistent access to systems.
“The advisory also confirmed that Volt Typhoon had maintained access and footholds within some victim IT environments for several years, indicating a long-term, strategic approach to positioning themselves within critical infrastructure for potential disruptive effects in the event of geopolitical or military conflicts,” says Michael Welch, managing director and sector lead, utilities, industrial, and critical infrastructure, MorganFranklin Consulting. “This long-term access, coupled with the strategic shift towards developing offensive capabilities, underscores the seriousness of the threat posed by Volt Typhoon to U.S. critical infrastructure and the necessity for heightened vigilance and enhanced cybersecurity measures across affected sectors.”
Lee says that what’s concerning to his team is not that Voltzite has deployed capabilities to target infrastructure, but rather the targets the group has chosen to hit—strategic sites that would hurt or cripple U.S. infrastructure.
For instance, Dragos recently worked with a mid-level electric customer that was compromised by Voltzite for well over 300 days. It was “very clear that the adversary, contained in the IT networks, was explicitly trying to get into the OT networks,” Lee adds.
Dragos worked with the client to confirm that the threat actors were stealing OT-specific data that would be useful in future disruptive attacks. The Dragos team was then able to work with the client to get the adversary out of its network, and then scale that same approach across its customer base. Dragos also provided information on the incident and the response to the U.S. government.
“It’s really powerful to have one entity get punched in the face but all of us learn about it as quickly as possible so nobody gets hit twice,” Lee says.
This incident validated the U.S. government focus on Volt Typhoon and that it is targeting key electric sites, Lee adds. “The cherry on top is showing where defense can win,” Lee says.
The Rise in Ransomware
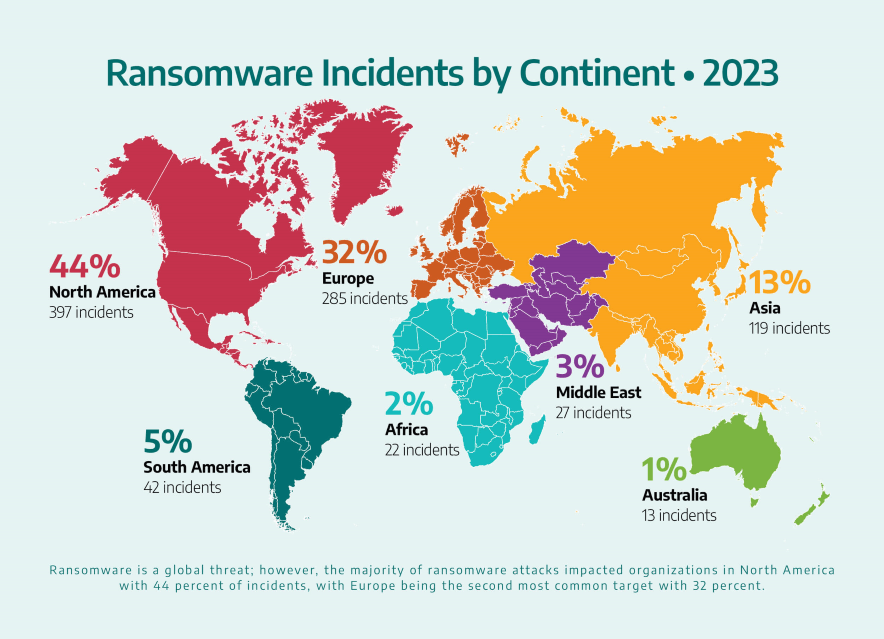
Dragos tracked a 49.5 percent increase in ransomware attacks, 905 reported incidents, against industrial organizations in 2023.
Most of these reported attacks occurred in North America (397 incidents, 44 percent), followed by Europe (285 incidents, 32 percent); Asia (119 incidents, 13 percent); South America (42 incidents, 5 percent); the Middle East (27 incidents, 3 percent); Africa (22 incidents, 2 percent); and Australia (13 incidents, 1 percent).
Attackers were especially attracted to manufacturing entities, targeting 638 of them in 33 unique subsectors, followed by ransomware attacks on ICS (115), transportation (65), oil and gas (30), electric (20), mining (13), water and renewables (10), and government and defense (2).
“Ransomware operators’ primary methods to gain initial access to victims’ networks have remained steady in 2023, including collaborating with initial access brokers, phishing, and exploiting publicly accessible network assets such, such VPNs and RDP servers,” according to the report. “Dragos also observed ransomware campaigns exploiting public-facing services such as Citrix using the Citrix Bleed vulnerabilities.”
Ransomware attackers can exploit victims partly because targeted organizations may have steps in place to keep assets from being directly connected to a public-facing network, but these assets are only behind a single defense layer—such as a firewall.
“The effectiveness of these security controls varies greatly, and organizations should not assume that a single layer is sufficient protection,” the report explains.
Lee says that ransomware actors do not typically target the OT environment but have learned that when they do, they are impacting revenue generating sectors for these businesses, who will often pay a ransom faster.
Lee also adds that about a quarter of all ransomware Dragos sees is LockBit malware. This means the UK and U.S. takedown of LockBit websites earlier this week could have a major impact on ransomware assaults on industrial organizations.
“Dragos points out that LockBit operations accounted for 25 percent of the total ransomware incidents against industrial organizations in 2023, which speaks to the importance of the recent law enforcement operation shutting them down,” says Brian Harrell, former assistant secretary for infrastructure protection at the U.S. Department of Homeland Security. “Anytime we can take an adversary off the board, that’s a win.”
Another Win for Security Teams
A positive note in Dragos’ report touched on a 2023 collaboration between industry, the OT security community, and the U.S. government to address a serious vulnerability before it could have a widespread impact.
Last year, the U.S. government notified Rockwell Automation—which provides industrial automation and digital transformation technologies used in industrial systems across the country—of two vulnerabilities impacting a subset of its ControlLogix communication modules (CVE-2023-3595 and CVE-2023-3596).
Rockwell then coordinated with the government to create a defensive working group that included Dragos to create detections for these vulnerabilities and search for evidence of exploitation. Dragos analysts were able to build these signatures to alert them to potential exploitation and then deploy them to Dragos’ existing products. The analysts then shared the results with the rest of the working group so the rest of the OT community could take similar steps, addressing the vulnerability before the adversary was able to launch their attacks, Lee says.
“This is the perfect case study of one of those left of boom moments,” Lee adds.
Other New Groups to Watch
Along with Voltzite, Dragos also highlighted two other new threat groups that are conducting long-term reconnaissance and intellectual property theft:
- GANANITE: Targeted government entities in Central Asian nations and the Commonwealth of Independent states, as well as attacking key personnel for industrial control system (ICS) operations in European oil and gas, rail in Turkey and Azerbaijan, and others.
- LAURIONITE: First identified after exploiting Oracle E-Business Suite iSupplier web services, the most-use enterprise solution for integrated business processes, including in United States Steel and textile manufacturing.
“Dragos observed all three threat groups conducting diverse operations against various organizations, including cybersecurity research firms, government and military defense entities, rail, manufacturing, automotive, and utilities,” according to the report. “GANANITE and LAURIONITE have exhibited an opportunistic approach to their initial access operations; however, VOLTZITE’s operations strongly indicate espionage and reconnaissance objectives in the Asia-Pacific region and the United States—particularly the electric sector.”
Harrell says Dragos rightly pointed out the mounting tensions with China and how that dynamic is contributing to increased cyber-espionage attacks against critical infrastructure in the United States—and around the globe.
“While I think industry has done a good job of eliminating low hanging cyber-fruit for adversaries, third parties remain a significant concern,” Harrell adds. “This is exactly why we must embrace secure-by-design for OT and ensure security always has a prominent seat at the C-suite table.”
About those Vulnerability Advisories
Alongside new threat groups and attack methods, Dragos also tracked a rise in common hardware and software vulnerabilities and exposures (CVEs) advisories in 2023—jumping from 465 in 2022 to 531 in 2023.
These advisories use a Common Vulnerability Scoring System (CVSS) to specify what vulnerabilities should be mitigated and how urgently they should be completed. Vulnerabilities with a CVSS of 9.0 or higher are considered critical and recommended to be mitigated immediately. But the report highlights issues with this approach.
For instance, researchers do not have a say on the copy of the advisory that is issued to the public, that CVSS does not account for OT network architecture, and they often do not have practical steps to mitigate the issue besides patching—which is often difficult or impossible for organizations.
Roya Gordon, executive industry consultant for OT cybersecurity at Hexagon’s Asset Lifecycle Intelligence Division, agrees that solely using a CVSS score to remediate vulnerabilities may not be the best approach.
“It’s important to understand where the vulnerability resides in the OT environment—based on data sensitivity, connectivity, criticality, etc.—in order to truly prioritize remediation,” Gordon adds. “For example, if a vulnerability with a CVSS score of 9 is in an islanded system, the risk may be less than the designated CVSS score. Having the context that a system is disconnected from the OT network or does not have access to sensitive data helps security teams better manage and prioritize vulnerability remediation.”
Dragos also tracked that 31 percent of the 2023 advisories had incorrect CVSS data. Lee says that this is an area where U.S. Computer Emergency Readiness Team (CERT) and the U.S. Cybersecurity and Infrastructure Security Agency (CISA) should play a role to acknowledge when vendors are doing a good job and when they’re not performing well.
This doesn’t mean picking “winners and losers,” Lee adds, but acknowledging openly that “this is what bad looks like; this is what good looks like…. If we can’t do that, then asset owners and operators can’t make informed choices.”
Next Steps for Security Practitioners
While the threat landscape may feel overwhelming, there are steps that security practitioners can take to reduce the risk of malicious activity—including that of Volt Typhoon’s—from impacting their systems and minimizing disruptions.
Lee says Dragos recommends using the Carnegie CERT Methodology of “Now, Next, Never” prioritization.
“This methodology prioritizes the vulnerabilities that defenders should mitigate immediately and places them in the Now category,” according to the report. “Vulnerabilities in the Next category can be mitigated through firewall rules and good network hygiene. This second group could be patched on the next maintenance cycle but should be monitored for abnormal network activity or exploitation. Lastly, vulnerabilities that do not increase the inherent risk of the device fall into the Never category.”
Welch says that in their work with clients, they continually stress the importance of security by design.
Welch suggests starting with identifying and understanding what assets you have and the functions they’re capable of, as well as which have critical functions and what the consequences might be from an adverse impact. Then, determine if there are ways to engineer the assets to reduce the attack surface or potential damage.
Similar to Dragos’s suggestion, Welch also recommends segmenting your network, layering your defenses, and engaging in continuous monitoring; understanding your upstream and downstream dependencies; and understanding what function suppliers play within your ecosystem and how remote access is provisioned and secured.
Finally, Welch adds that owners and operators have incident response and recovery plans in place, conduct tabletops on them, and collaborate and share information with your peers.
“In 2024, critical infrastructure owners and operators need to continue to pay close attention to ransomware, but also how artificial intelligence and machine learning can be used in cyberattacks, vulnerabilities in supply chains, remote access, and how the OT/IoT ecosystem continues to grow, Welch adds. “As cyberattacks continue to advance, we need to continue to enhance our strategies around identity, access, network segmentation and overall resilience.”