The Carrot and the Stick: How Audits Sustain Success
“This may just be the last tool we have to get the resources needed to secure our systems.” Those were the words of an IT department head at a company where I once worked as he desperately described the degraded state of our infrastructure. “We’ve tried just about every angle to fund our most basic needs and we’ve failed, so we hope these audits will show senior leadership just how badly we need help,” he continued. I felt his pain. Our department had fought similar battles and lost many of them. It seemed that no matter how many times we identified deficiencies and offered solutions, the money was rarely available to get the job done.
This is a common scenario in corporate security. When times are lean, budgets are often cut or, at best, remain flat. When times are good, resources may be available at the start of the fiscal year, but as the year progresses, funding for security is often diverted to other projects. This often results in once-working systems degrading year over year until they finally fail, usually at the worst times, resulting in significant vulnerabilities and risk.
Establishing a security audit program may not only help to assess the state of your program but might just be your “Hail Mary” pass attempt for salvaging it. However, some very important steps need to precede this initiative if you hope to launch and conduct a successful security audit program.
This is the fifth and final article in a series about security governance. The first article, “Setting the Bar for Strong Governance in Security Management,” makes the case for establishing a governance program within your organization’s security department. The second article, “For Effective Governance, State with Why,” implores you to ask yourself why you need a security program in the first place and then provides an outline for your program standards as to how you can communicate your why to the rest of the organization. The third article, “The How of Security Governance: Procedures Provide Support,” makes the case for tactical-level guidance on completing the most common tasks at your sites, and the fourth article, “On the Point of a Double-Edged Sword: Technical Standards Protect and Defend,” provides a framework for creating technical standards.
Brand Your Program
Department standards, operational procedures, and technical standards represent the most basic building blocks of your security program. While standards are important, they’re nothing more than good ideas unless you are prepared to enforce them, hence the reason for a formal review, a way to judge the effectiveness of your program for your organization’s stakeholders. This is often known as an audit, but can also be known as an operational review or compliance check.
The term you choose will likely depend upon your organization’s culture. For example, you may find that using the term operational review is more attractive in an unregulated industry that has few internal controls and little history of conducting audits, whereas the term audit may be more common in a more regulated industry. Brand the process with a term that is most likely to be adopted and garner support. At my current company, we use the term audit, but at my former company, we used the term security management operational review. Use terminology common within your organization.
Socialize, Socialize, Socialize
Regardless of which term you use, it’s critical to socialize your standards thoroughly in advance of your audit program. At my current company, we provided a full year after the launch of our final standards product—our technical standards—to ensure that our clients were familiar with the products upon which they would be judged. Promote them at every opportunity.
As soon as a standard product was completed, we uploaded it onto our global security website and email notifications went out to the field informing them as such. As part of our roadshow to sites, we always spend time with our site security leaders ensuring they know how to access the website—and to create a little urgency—we remind them of their upcoming security audits. When we receive queries about policy or procedure, we always refer our clients back to our standards. A link to our website appears in my email signature and can be found easily using our company’s internal website.
We tend to fear being judged, so it’s also important to reassure your teams that your audits are not only tools that can be used to help appeal for additional resources, but to also maintain existing assets and encourage continuous improvement.
Be sensitive to the fact that audits can feel invasive and take away from one’s daily priorities. If you’re now working at the strategic level at your organization, chances are good that you progressed through the tactical and operational levels where, in the past, you prepared for weeks for “the experts from out of town” to parachute in to conduct their audits, pontificate about your deficiencies, and then blow back out of town, leaving a wake of stress and anxiety at your site. You’re now on the other side. Go slow, walk softly, and don’t create anything you cannot support. Your audit may be yet one more task that’s being requested on top of an already long list of management responsibilities, so reassure your teams that the process will be thoroughly supported by your corporate security team. You’re there to help them, and the audit is a tool you have created to ensure continuous improvement.
In most cases, audits are to be used as carrots to reward success, not sticks to penalize for non-compliance.
Establish Your Process
With your standards complete, available, and promoted, you can now think about creating the framework for your audit program. I found it useful to first interview colleagues at my current organization to understand their processes and borrow as much as possible from them, including terminology, timelines, reporting structures, and methods for following up. If your teams in the field are already conducting reviews with groups like internal audit; environment, health, and safety (EHS); or regulatory agencies, using similar processes and terminology will be easier for them to understand. For example, if EHS employs a self-audit phase and calls it a Level 1 Audit, do the same for your security audit.
Next, consider the criteria for your audit. Referring to your standards, select major categories and develop your points—the items to be assessed. Each audit point must be supported by your standards. It should be thorough enough to be meaningful yet cause the least amount of stress for those involved.
At my current organization, we have 13 sections that cover 147 audit points. This may sound like a lot, but it’s not. We purposefully created it so a senior guard could complete it within four hours, and many sites have reported that it can be done in less time. Feedback from the field has confirmed this, and nearly everyone involved has been pleasantly surprised by how pragmatic and simple our checklist is to use.
This is not a comprehensive list, but categories may include:
- Facility details. This is an opportunity to collect the basic details of the site such as site name, address, type, workforce size, floor size, facility leaders, names of those completing and reviewing the audit, organization (if not part of your organization), and date completed. You may also want to capture data like total number of cameras, card readers, etc. Include a section where an updated image of the facility can be uploaded.
- Action plan. This is a comprehensive list of deficiencies, images to support findings, plans for improvement, and anticipated completion dates.
- Score sheet. Leverage an auto-tabulating scorecard arranged by category noting max available points, raw scores, and percentage scores.
- Administrative. Does the site have someone responsible for security? Are they familiar with your security resources? Can they demonstrate this? Do they have post orders in place? Are they reviewed regularly?
- Guard services. Does the site have a dedicated guard service? Is management responsive? Are guards using a standardized incident reporting platform? Is patrol round information collected and monitored? Are response procedures clearly defined and documented? Have emergency response procedures been tested?
- Access control. Does the facility have an automated access control system? Is the access control system functioning properly? Are doors kept closed and locked? Is the system tied to a corporate operations center? Are visitors requested to sign in and wear badges?
- Video management systems. Does the facility use video surveillance to aid the security force? Is the system functioning as designed? Is there adequate light for viewing? Are there cameras monitoring critical spaces like lobbies, IT server rooms, main entrances, and parking lots?
- Intrusion detection systems. Does the facility have an intrusion detection system? Is it functioning as designed? Is the system monitored by a central station or an operations center?
- Lighting. Does lighting properly illuminate all facility roads? Is there adequate exterior and interior lighting to provide a safe environment for operations? Do exits have emergency lights and lighted exit signs?
- Clear zones, grounds, and signs. Does the facility have clear zones on the inside and outside of perimeter fencing? Are there any scaling hazards? Are private property and/or no firearms signs posted at regular intervals?
- Vehicle control. Are vehicles searched when entering the perimeter zone? Are vehicles searched? Is a vehicle log maintained? Are loads spot checked for paperwork and load integrity? Are there pre-alerts for collections or deliveries?
- Emergency response and crisis management. Does the facility have emergency response procedures? Do procedures include workplace violence, bomb threats, medical emergencies, etc.? Do drills take place on a regular basis?
- Training. Are there security awareness, emergency and crisis management, first aid, and security procedures training programs in place? Is mandatory training documented?
Though commercial audit platform subscriptions exist, we created ours using Google Sheets (the same can be done using Excel) and, using embedded formulas, our check sheets are self-tabulating. Scoring is basic—two points for compliant, one point for partially compliant, and zero points for non-compliant. Columns also exist for not applicable, max score possible, score, facility comments, and reviewer comments. Each section then lists total points possible, total score, and percentage correct. Each section score then auto-populates in the score sheet section, and non-compliant deficiencies auto-populate in the action plan section.
What do you want to set as a passing score? We set the bar at 70 percent—a minimum score of 70 percent is required in each section and overall. Once completed, scores are auto-loaded onto an audit dashboard which we created using Google Data Studio (now known as Looker Studio). Data can then be tracked by site, area, region, and category, and progress can be monitored on a real-time basis.
The scope and frequency of your audits will be determined by your industry type, department resources, existing processes, culture, and risk. We employ a four-level system which is somewhat aligned with existing internal processes:
- Level 1. For low- and medium-risk sites, this is an annual self-audit process in which site leaders complete our checklist. The corporate security team then reviews findings with them, answers questions, and adjusts scoring if necessary. For high- and critical-risk sites, this occurs every six months.
- Level 2. This one counts for the record. Conducted by the corporate security team at the site, this is a confirmation of a Level 1 audit, and it occurs with a site visit. Findings are reviewed thoroughly, and discussions focus on providing pragmatic solutions for improvement. These are great opportunities to conduct training and demonstrate support. These occur every other year for low- and medium-risk sites, annually for high- and critical-risk sites.
- Level 3. Special audits following near-miss and loss events. These focus only on areas that may have contributed to an incident and may be conducted by site, corporate, or outside auditors.
- Level 4. Conducted by outside organizations, these audits may be driven by regulatory requirements and/or a desire for specialist involvement (e.g., government agencies or professional industrial auditors).
A reasonable roll-out plan may be to spend the first year creating your standards, the second year socializing them, the third year conducting Level 1 audits, and the fourth year conducting Level 2 audits. Ensuing years can then rotate back and forth between Level 1 and Level 2 audits. This is the approach we’re taking at my current company, where adoption and administration has been positive.
The process for passing an audit may be best illustrated using the following flowchart:
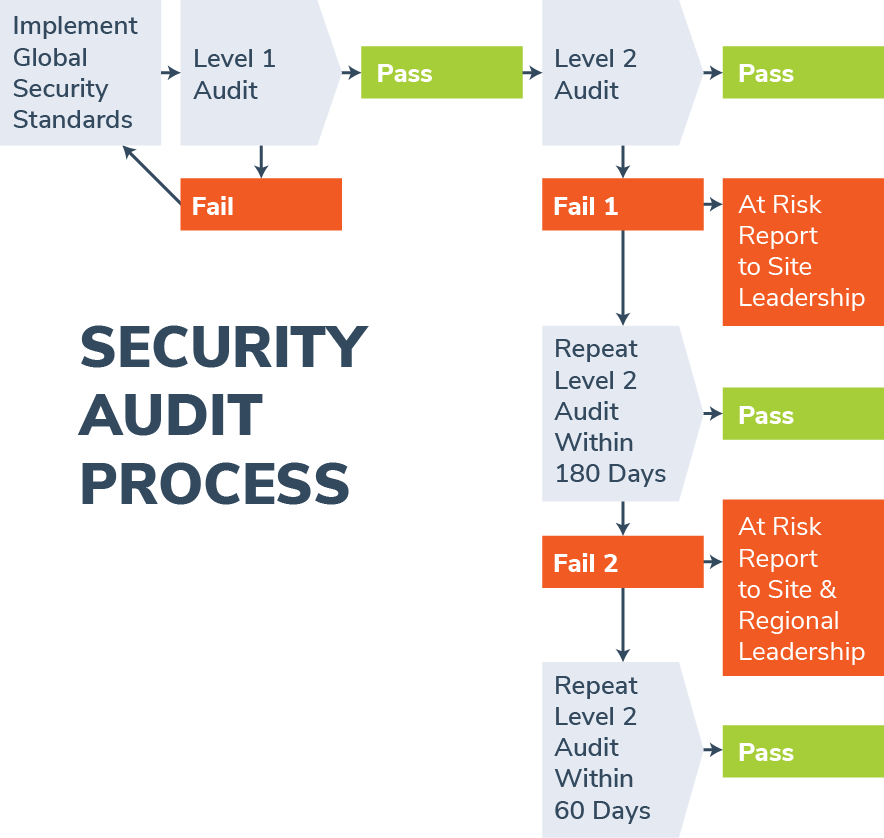
If 70 percent compliance is not obtained during a Level 2 audit, an “At Risk Report” is drafted which outlines deficiencies. For the first failure, the report remains at the site level, but if there is a second failure, it escalates to site and regional leadership. Hopefully, there won’t be a third failure, but if there is, a third escalation to corporate leadership may be in order to make a point.
Maturity Modeling
A maturity model is a tool that organizations use to measure how well they are doing and how capable they are of continuous improvement. Measurements are based upon standards, so choosing your standards will be critical. Because so few standards exist within the security industry, you will likely be benchmarking against yourself—your standards—so your scores will demonstrate your current state, where you want to go, and what you need to get there.
We use four designations to define our current state of maturity, and they are based upon the results of Level 2 audits:
- At Risk (<70 percent overall). A site has not achieved a fundamental level of security to adequately safeguard its people, property, information, and/or processes. When this occurs, findings are reported to regional leadership and must be addressed immediately.
- Foundational (70-79 percent overall). The site has achieved a fundamental level of security. Several areas for improvement exist and some domains may be close to At Risk designations, so constant monitoring and improvement should be implemented.
- Performing (80-89 percent overall). The site is implementing and maintaining the department standards adequately and consistently. Some domains may be foundational, so sites should be encouraged to maintain and improve.
- Excelling (90-100 percent overall). This represents a best-in-class program. Team members and leadership are to be commended and the program is promoted and cited as an exemplar.
Consider creating and presenting meaningful, unique awards to your sites that demonstrate and recognize consistent improvement. Create something they will be proud to display and promote, further promoting a culture of security within your organization. The type and style of award will be driven by your organization’s culture. Have fun with them and try to avoid yet another boring certificate in a cheap frame or engraved acrylic trophy. For example, we’ve considered creating professional wrestling championship belts and other whimsical items.
All concepts, processes, and the terminology should be outlined within your security department standards, and your standards should be updated regularly. We review ours as needed but at least annually. Finally, consider your other partners which can help audit parts of your program. Regular internal audits usually include major categories for security, and if you have contracted guard services, they should be conducting regular audits of their guards. These are your backstops and will be mutually reinforcing if aligned with your standards.
With your standards created, a method for enforcing them, and a process for continuous improvement, you will have a fundamental governance program for your department. Additional products will support these fundamentals as your program matures. As a manager, you will spend less time in the trenches dealing with issues on an ad-hoc basis at the tactical and operational levels and more time actually leading strategically, offering creative solutions for your team and your customers.
Erik Antons, CPP, PSP, is the chief security officer of Whirlpool Corporation, where he leads the physical security risk and crisis management programs for the $20 billion enterprise of more than 61,000 employees across 170 countries. Previously, he was vice president and CSO of Hyatt Hotels Corporation and the manager of international security and executive services with Sempra Energy. Antons began his security management career as a special agent with the Diplomatic Security Service with the U.S. Department of State, where he safeguarded the people, property, and information of Americans overseas, often in critical-threat environments.
The comments and views expressed in this article are the author’s alone and may not reflect those of his employer.