How to Scale Investigations Using Open-Source Intelligence
Modern investigations into today’s most sophisticated criminal activity involve a variety of tactics, including the analysis of both physical and digital evidence.
With so much more organized crime being coordinated online, open-source intelligence (OSINT) has become a critical element of the investigative process. And with so much publicly available information online to work through, it’s important to help a broader range of professionals understand where OSINT fits into the investigative workflow, and how to properly scale short-term and long-term investigations.
Whether you are a member of law enforcement, or part of a security team within a private organization, online artifacts must not be overlooked. Having a method to the madness is key as investigators look to integrate OSINT more thoughtfully into their investigative workflows. To do so, they need to know when, where, and how to add the collection of online and publicly available information into their process to translate it into valuable intelligence.
Back to the Basics: Investigative Fundamentals & Definitions
There are some ground rules for any effective investigation that serve as the foundation for gathering information that will ultimately be transformed into intelligence.
These fundamentals include:
- Understand OSINF vs. OSINT. Open-source information collected online is “OSINF.” It’s not until human analysis and context is applied that it becomes open-source intelligence, “OSINT.” This distinction is important because data tells the story, but humans cannot be removed from the workflow.
- Follow the scientific process. Keep it simple and map your questions and theories. Write them down in a notebook and see if artifacts support them. This helps me as an investigator in two areas: longer-term memory and keeping me honest when my ego may magnify an artifact or demand the story fits the artifacts into place versus what needs to happen.
- Document the W’s. Being intentional about answering what, when, where, and why will help you remember it all comes back to the who. And as you start discovering data, the answers will emerge.
- Map friends and associates. The more you know, the luckier you will become. In other words, the more information you have, the more likely you are to be successful. Map out each entity's friends, associates, known businesses, and locations.
- Document and keep everything. Document each connection and relationship using a link analysis tool, pen, and paper. It’s paramount you preserve your findings and thoughts, as data may become relevant in the future. I can’t begin to emphasize how valuable this step is. Once you have determined the dates and events that make up an investigation, use a spreadsheet or handwritten journal to build a timeline and see what—if any—artifacts correlate. As you continue building your timeline, patterns will eventually emerge.
A Sample Investigative Workflow to Support Scaling OSINT
There are seemingly 100 different ways to reach a single conclusion or find a piece of information. But the best and most successful investigative workflows, which span the physical acquisition of artifacts and electronic data, can typically be illustrated through four key stages. This ideal workflow for integrating OSINF and OSINT collection includes: acquisition and collection, indexing, analysis and data exploitation, and reporting and “finding the gold.”
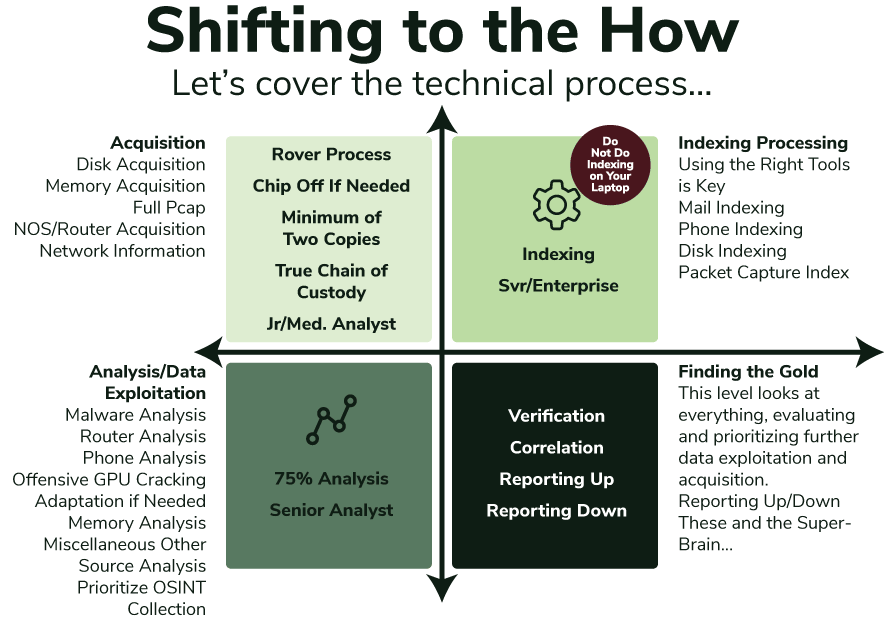
1. Acquisition and Collection
Data needs to be acquired first. In this step, investigators need to group all acquisition requests to the analyst in charge of acquiring data. The importance of decoupling acquisition tasks to a particular group or subject matter expert allows for scaling of the requirements, like analysis or data exploitation, and reporting phases. Examples of elements that fit under the acquisition phase include hard disk, memory, packet capture, social media and publicly available or OSINF, and other physical hardware like phones, database acquisition, etc.
2. Indexing
Once data has been acquired and normalized, it must be indexed for advanced queries, relational data modeling, or simple queries for lookup. Different technologies exist to allow additional data types to be indexed. In short, the indexing phase is all about making data searchable.
3. Analysis and Exploitation
Within the analysis and exploitation phase, valuable information is gleaned. I start by analyzing the data we have gathered, looking for correlations that support the questions and theories we posed earlier in the process. This vigorous interrogation of data will enable us to report on the data or allow us to increase the collection of a particular data source recursively for continued insights gleaned in this phase.
4. Reporting and Gold Digging
The reporting phase can potentially redirect the acquisition and analysis phases, while also sharing valuable information regarding investigative requirements with stakeholders or business owners. As critical information is discovered and documented, new artifacts can be added for acquisition or correlated within the analysis and exploitation phase. Most of the time, OSINT/OSINF collection falls into this section of the investigation, as well as the data acquisition phase.
There is tension within these processes, usually because the analyst or team must perform two different workflows and thought patterns during this process. The first is a sequential gathering, indexing (allowing information to be searched) or tagging workflow. The second is a visual-spatial correlation from analysis, exploitation, and reporting. Decoupling each investigative arc segment allows skilled analysts to incorporate distinct skill sets into each process. Some will be better with sequential, methodical, and repetitive tasks, which require precision. In contrast, others will shine in putting all the puzzle pieces together.
The More You Know, The Luckier You Become
Scaling an investigation has everything to do with decoupling each process. As you add more people to your team, you can delegate the different tasks of this more-extensive process to enable a long-term investigation at a larger scale. This is critical, as it will help you identify investigative bottlenecks while also maximizing each individual analyst's performance.
With OSINT collection, much of the learning curve revolves around collection and identifying the correlations of seemingly disparate data types in a visual-spatial model. OSINT may not solve all the issues within an investigation, but it will provide valuable clues that you won’t find anywhere else. The unspoken value of one small artifact can break a case open or change a perspective. My experiences in collecting all sorts of data in investigations while adding in OSINT collection have taught me that the more I know, the luckier I become in my investigations.
Daniel Clemens is the founder and CEO of ShadowDragon, a leader in ethical open-source intelligence (OSINT), unique datasets, and investigative training. Clemens has dedicated his career to solving complex crimes that leverage technology and the internet. His decades of experience include aiding in extensive research and offensive action against emerging threats, creating scalable curriculum for long term investigations, and offering insights to uncover clues for anti-human trafficking organizations globally.
© ShadowDragon