Availability First Achieves More Positive Outcomes. It’s a Mindset!
Availability may be defined as being “able to be used or obtained; at someone's disposal.” Outcomes may be defined as, “a concise, defined, and observable result or change in business performance, supported by a specific measure.”
What outcomes do you currently have available? What outcomes do you want available? What outcomes do you need available?
Leading with Availability
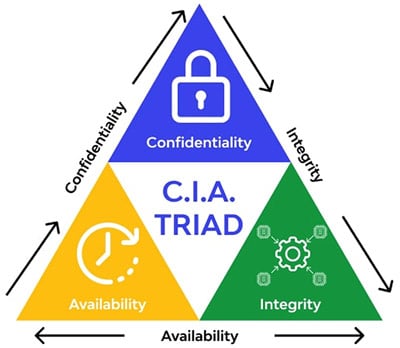 The Confidentiality Integrity Availability (CIA) triad in cybersecurity represents an information security model meant to guide an organization’s security procedures and policies. If we want to change the narrative, to achieve more positive outcomes, then we must change the way we lead.
The Confidentiality Integrity Availability (CIA) triad in cybersecurity represents an information security model meant to guide an organization’s security procedures and policies. If we want to change the narrative, to achieve more positive outcomes, then we must change the way we lead.
In the case of the CIA triad, we must lead the conversation with availability to achieve more positive outcomes. Availability of systems. Availability of data. Availability of organizations, agencies, cities, states, governments, and nation’s critical assets (crown jewels). Why? People’s lives are at stake.
Eight years ago, the IBM Cybersecurity Intelligence Index Report found that 95 percent of cybersecurity incidents recognized “human error” as a contributing factor. The report, published in 2014, explained that “the most commonly recorded form of human errors includes: system misconfiguration, poor patch management, use of default usernames and passwords or easy-to-guess passwords, lost laptops or mobile devices, and disclosure of regulated information via use of an incorrect email address.”
The most prevalent contributing human error? “Double-clicking” on an infected attachment or unsafe URL,” IBM found.
In 2022, things have not changed much. The annual Verizon Data Breach Incident Report found that the human element accounted for 82 percent of analyzed breaches in the past year.
If we unpack the research a little deeper, we find that the ubiquity of cyber events is a systems issue and a human issue when leaders continue to follow the same failed strategies that got us here.
Let’s think about the IBM and DBIR’s findings critically. If one person within your organization double-clicks on a link and takes down your entire system, making it unavailable, then it’s not a human issue—it’s a bad system issue. If one person can access and download your most critical assets, e.g., proprietary information, and make that available to outside competitors, nation states, or the highest bidder, without you knowing, or without you stopping that data leakage, then your system is bad. If one person can log in and gain access to your most critical data, information, systems, crown jewels, critical assets, and make them unavailable, then your system—once again—is a poor one.
The consensus, or common response from leaders when talking about cyber expectations, is that incidents are ubiquitous. It is not a question of if I am going to be hacked, but when I will be hacked. This defeatist mentality, and past failed strategy, is what got us here in the first place. We must flip the script, change our mindset, and move forward.
We need to challenge assumptions, and make a mental paradigm shift to ensure availability first to achieve more positive outcomes, by thinking about cybersecurity with a more proactive, preventative mindset. Let’s plan for failure, while stating: “When our ecosystem is attacked, breached, and/or intruded upon, if our systems are great, by being designed with security in mind, our critical assets will still be available, and we will achieve more positive outcomes—up to and including saving people’s lives.”
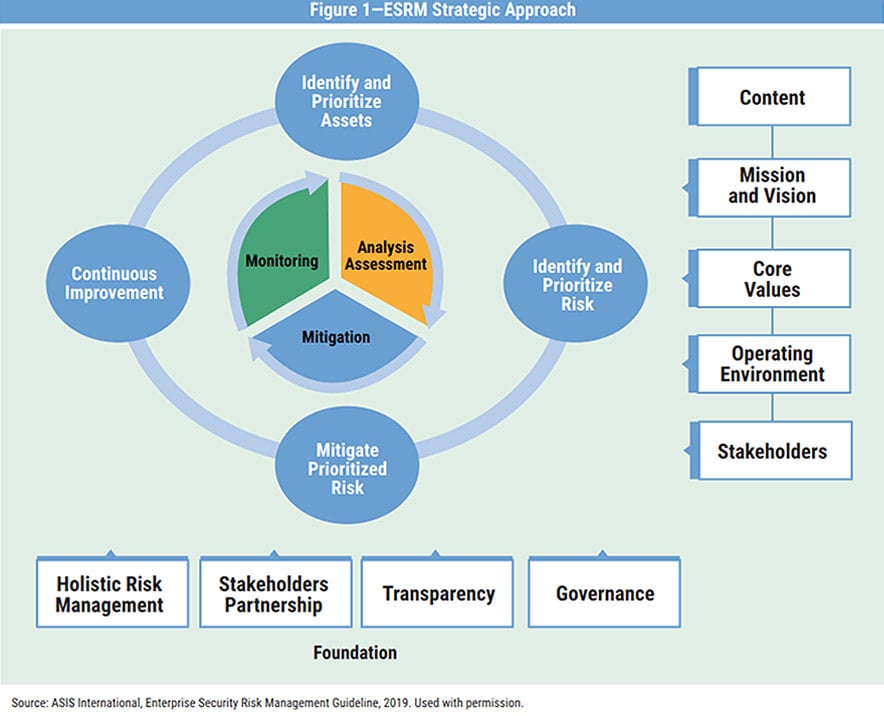
How do we set this in motion? It begins with using the Enterprise Security Risk Management (ESRM) approach:
- Identify and prioritize assets. We identify and define our critical assets, so we know what we are protecting.
- Identify and prioritize risk. We identify risk through discovery of value deficiencies, gaps, and vulnerabilities to prioritize risks and their acceptable levels. Typically, this is done through a security and risk assessment to provide actionable intelligence and visibility across the network.
- Mitigate prioritized risk. The findings from the above steps are then used to collaboratively create a strategic roadmap of defense-in-depth advanced cybersecurity solutions to be deployed—either as a force multiplier, replacement, or to ensure existing controls efficacy. This will help mitigate prioritized risks while reducing impacts to critical assets.
- Continuously improve. This is achieved through continuous evaluation, measurement, monitoring, and optimization. This unbiased, data-driven process ensures efficacy of critical controls, while continuously improving the availability of systems to achieve more positive outcomes. This process is a continuous feedback loop, which is rinsed and repeated.
One method of implementing this approach is using the Zero Trust Maturity Model, recommended by the U.S. Department of Homeland Security’s Cybersecurity and Infrastructure Security Agency in its National Security Telecommunications Advisory Committee (NSTAC) report.
The NSTAC report defines the five-step zero-trust approach as:
- Define the protect surface
- Map the transaction flows
- Build a zero-trust architecture
- Create a zero-trust policy
- Monitor and maintain the network
Through the strategic deployment and effective implementation of zero-trust holistically across U.S. critical infrastructure and systems, the NSTCA wrote that more positive outcomes will be achieved within government systems and service, public safety, and our national security, by placing availability first.
Baking in a Mindset
A proactive security mindset must be baked into the system, including a threshold of trust. When that trust threshold is breached, reverification is then required, ensuring availability of critical assets. This is done by continuously evaluating, measuring, monitoring, and optimizing systems, processes, and critical controls, while looking for the absence of normal, and the presence of abnormal. Automation assists here, acting as a force multiplier, augmenting the human factor, to ingest the exponential amount of actionable intelligence, contextualized data, at scale.
Examples include automated pen tests, security information and event management (SIEM) alerts, endpoint detection and response (EDRs), extended detection and response (XDR), and managed detection and response (MDRs), combined with threat hunting and detection of anomalous behavior using artificial intelligence (AI) and machine learning (ML). Other examples of using AI and ML at scale, while ensuring governance, risk, compliance, and cybersecurity alignment, is using immutable anonymized encrypted block chain data lakes, and hyper automation. The ingestion and encryption of data at scale provides actionable preventive intelligence that can be used to make informed decisions to achieve more positive outcomes.
An example of placing availability first to achieve more positive outcomes on the physical side of the house is executive protection (EP). These practitioners identify, prioritize, and continuously monitor their most critical assets—the people they are protecting—to ensure availability of these critical assets. If the principles and their families go home safely at the end of the EP detail’s shift, that is considered a success.
Cybersecurity requires the same mindset. If we continuously identify, prioritize, and monitor our most critical assets (e.g., source code, location of sales force, IP, a mainframe, 911 systems, healthcare systems, personally identifiable information, industrial control system/operational technology assets), and those critical assets are still available at the end of our shift, then by changing our mindset and placing availability first, we have achieved a more positive outcome.
By utilizing the force multipliers and solutions mentioned previously, organizations can map out their network using cybersecurity frameworks and strategies such as zero-trust, ISO 27000, MITRE ATT&CK Framework, NIST’s Cybersecurity Framework, or the Center for Internet Security (CIS) 18 critical security controls. Any of these would be a good place to start building out a solid foundation ensuring governance, risk, compliance, and cybersecurity alignment—along with efficacy, and resiliency of one’s network.
But keep in mind that to achieve more positive outcomes and save lives, relying solely upon compliance is a race to the bottom. One must not only check boxes but use an evidence-based approach and test out critical controls. Run exercises and drills, have incident response plans in place, and conduct pen tests to ensure efficacy of your critical controls. Do not let your worst day be your first day.
This approach has a positive effect on people’s lives—up to and including saving lives. Because all those critical assets—whether they’re bits and bytes, X’s and O’s, 0’s and 1’s, or ICS/OT assets, are interconnected, and have an effect on people and their lives.
Every organization, agency, city, state, government, and nation is technology enabled, and threat actors are capable of accessing—and potentially making unavailable—critical assets.
But if we flip the script to place availability first, we achieve more positive outcomes. If we plan for failure and build great security-by-design systems, when our ecosystem is attacked, breached, and or intruded upon, our critical assets will still be available, and we will achieve more positive outcomes, up to and including saving people’s lives. It’s a mindset!
Andrew J. Peden, CPP, MBA, B.Sc., is CEO at L5L Solutions, which provides simple evidence-based cybersecurity solutions that reduce risk and increase efficacy, transparency, and cyber resilience. He is a member of the ASIS Crisis Management and Business Continuity Community Steering Committee and previously served on the ASIS Chief Security Officer Standards Committee.
