Battle Ready: Maintaining Operations in Conflict Zones
Si vis pacem, para bellam. “If you want peace, prepare for war.” This phrase, passed down from the time of the Roman Empire, serves as a reminder of the dangers a nation can face, admonishing us that it is through preparedness and a willingness to defend oneself that a country can expect to keep its populace at peace.
For the security professional, the phrase has a slightly different meaning. When you can prepare your organization for the worst, you will have the greatest degree of confidence in your team’s ability to face what comes.
War is without question the most catastrophic and difficult man-made disaster known. Its impact is felt at every level of a society, and its duration always exceeds the actual fighting. There will be impacts that a security professional cannot negate, regardless of the level of preparation; however, there are steps that can be taken to improve the chances of success.
First, one must understand exactly what it is the organization does or does not do. In the author’s case, the AIDS Healthcare Foundation (AHF) is a non-governmental organization (NGO) specializing in the treatment and care of HIV-related patients. With operations in more than 45 countries and approximately 1.6 million patients in its care, the organization’s security demands are broad and challenging.
As an organization, AHF—like many NGOs—has at its core a commitment to those that it serves. To achieve this, it operates using a locally based model. AHF normally brings healthcare best practices to a country’s fight against the HIV/AIDS epidemic and works with local governments to employ those practices.
For this to work, the organization must have good relationships with all levels of government and adapt proven methodologies to the local environment. As a rule, AHF does not use expatriates, but rather it seeks to find and employ people within a country who have the talent and will to work with the organization. AHF then leverages its knowledge and employees’ skills using business practices that would not be unfamiliar to any commercial operation.
With this model in mind, AHF was able to plan and respond to the challenge of three different conflicts in a two-year period.
In Ethiopia, two years of conflict between Ethiopian government forces and rebel forces—the Tigray People’s Liberation Front—have left thousands dead and millions displaced. The civil war has shifted wildly since it began in November 2020, with foreign groups fleeing the area, especially when Tigrayan fighters surged south toward the capital of Addis Ababa before being forced back by the Ethiopian military. While the conflict is around ethnic and tribal identity, its impact is further complicated by the Ethiopian government increasing internal security pressure on ethnic Tigrayans living in the capital.
At AHF, we became concerned about the success the Tigrayan forces were having against the Ethiopian Defense Forces in September 2021 and its possible impact on our personnel and more than 30,000 patients—mostly in the Addis Ababa metropolitan area.
Skilled investigators are often good at intelligence analysis.
In the early morning of 1 February 2021, the Myanmar military removed democratically elected leaders in the country in an unexpected coup d’état. Mass protests, civil unrest, and conflict followed. Similar to the situation in Ethiopia, AHF was concerned about its personnel and approximately 17,000 patients. In addition, many young medical professionals (doctors, nurses, etc.) were in the forefront of Myanmar’s civil disobedience movement, which drew special attention from internal security forces supporting the coup.
On 24 February 2022, after months of escalating rhetoric and disintegrating diplomatic ties, Russia invaded Ukraine in a full-scale assault, sparking a wave of evacuations, business closures, supply chain shortages, and economic sanctions. This presented a much greater challenge to the safety and security of AHF’s personnel and its roughly 52,000 patients. Following the more conventional warfare model of a nation-versus-nation clash, the invasion forced a deeper and broader look at how best to respond.
Between reliance on intelligence, long-term development of credibility with stakeholders, and preparedness, AHF was able to either prepare for or respond to these crises and keep providing healthcare to thousands of patients in conflict zones.
Intelligence—Do You Have a Plan?
If a company or organization is operating internationally, it is important that it has a well-developed intelligence program—whether the organization is facing a conflict zone or not. This does not mean you must have access to classified information. When paired with a well-developed internal intelligence operation, open-source information can be extremely helpful.
When developing an intelligence function, it is important that the senior leadership understands the value of the information you produce and is willing to listen to the results of your efforts.
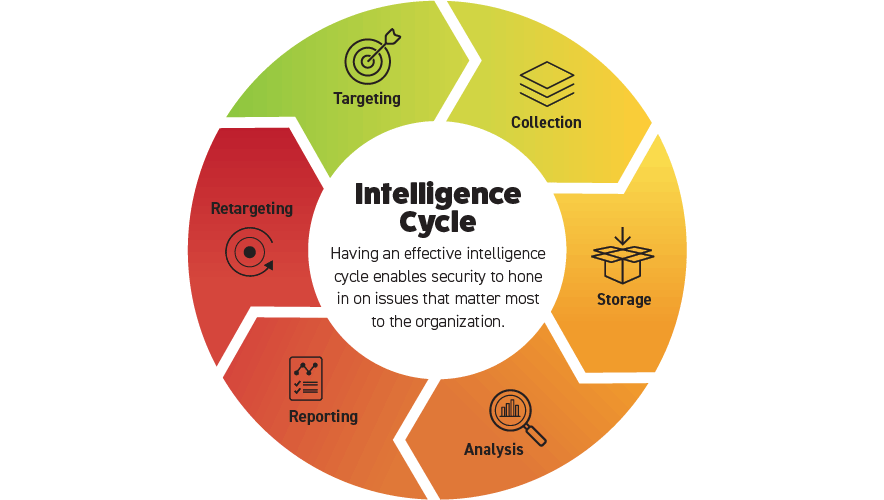
AHF operates in several conflict zones. During the past seven years, its senior leadership came to see that the world was changing regarding security risks—and not for the better. When this was combined with AHF’s rapid growth when fighting the spread of HIV, leaders determined they needed to implement a security department, which led to the understanding of the need for an intelligence system that could be leveraged by the organization at multiple levels. To handle this shift successfully, security professionals must understand the intelligence cycle, as well as the needs and business model of their organization.
The intelligence collection and assessment cycle has been described in many ways, but the simplest is a cycle of six elements that feed into each other: targeting, collection, storage, analysis, reporting, and retargeting. The effectiveness of using this cycle will greatly impact your ability to prepare an organization for war.
Targeting. Knowing what is needed for your stakeholders to make informed decisions is essential. Within the intelligence community, there are targeted areas of interest (TAI) and named areas of interest (NAI).
A TAI is a specific subject or location that is being monitored by an asset. The classic example would be having a satellite watch a specific piece of terrain for changes. Normally, TAIs have been identified as important through discussions with decision makers. When determining what will get the focused attention and resources of a TAI, ask what the leadership wants to know. When dealing with conflict situations, it may be necessary to guide the discussion so you can discover the TAI.
The type of asset used to monitor a TAI will depend on the information required. For security managers, start by looking internally. Consider a preexisting video system; the cameras covering the exterior of the facility can provide valuable information in a conflict zone. A contract security guard company can also be an excellent asset. Often these companies can facilitate a better relationship with the local law enforcement personnel—another key intelligence asset. Finally, most security professionals operating internationally make it a good practice to contact their respective foreign diplomatic services when working within a country. In the case of American companies, the U.S. Department of State Diplomatic Security Service (DSS) can be very helpful. The DSS staff can be consulted about the reliability of a local law enforcement contact, helping to make sure security teams are dealing with the right people to monitor a TAI.
An NAI is a particular topic, subject, or location for which there is a general need for information, but it does not have a targeted asset monitoring it. NAIs are typically linked to major concerns at various levels of an organization. Senior leaders may be more interested in political decisions that impact the profitability—as well as security—of their operations. Those in the extractive industry understand that political changes in a host country can significantly impact operations and the organization’s risk tolerance.
In other cases, it may be something a little subtler. An NAI for a retailer or shipping company might focus on theft ring operations in the supply chain and their potential impact on the movement of goods. Given the current level of supply chain challenges occurring worldwide, understanding where these risks are greatest might be of significant interest to leaders. It is this kind of information that allows them to make informed decisions on a much broader scale and longer timeline. You may not be dedicating specific assets to the collection of information for these NAIs, but you can identify the information as it emerges and provide it in a timely fashion to stakeholders so they can be aware of the challenges.
Collection. Most organizations are really good at collecting information. But are they collecting the right kinds of information? From the NAIs and TAIs, security teams can identify the general topics that are important to leaders and operational staff. However, collection for collection’s sake is essentially filling a drive with meaningless data—one simply cannot review it all.
By using your TAI and NAI categories, you can focus your collection efforts in a way that allows for timely storage, analysis, and reporting.
Storage. The most important element in the storage process is organization. Finding information quickly only happens if you organize it accordingly. It’s important that security teams develop an organization system early in the storage process. Typically, the easiest way to do this is to use TAIs and NAIs as files and store the data accordingly. With modern technology and the ability to use the cloud, one can cross-reference materials quickly—the hashtag capability works well here.
Analysis. This is the most time-consuming element of the cycle. Analysis combines all of your knowledge and experience, and it can be as much an art as it is a science. For the intelligence cycle to work, security teams must spend time analyzing the information based on the need and the report they need to submit.
Security professionals have the advantage of their investigative skills and experience. Skilled investigators are often good at intelligence analysis. Looking at evidence, evaluating its value and validity, and synthesizing conclusions are all useful when engaging in intelligence analysis. The key difference is the certainty factor. For investigators, there must be a high level of confidence in the evidence, which is rarely found in intelligence analysis—especially for politically unstable regions or conflict zones.
Reporting. Reporting is more than just giving an opinion—it’s providing timely information for decision makers in a format that can be readily understood and is supported by fact. Reporting should be designed for its target audience; most executives don’t have the time or desire to read a 50-page intelligence product.
Retargeting. This last phase is often overlooked but extremely important. After the executives get the report, they are going to have more questions and ask you to focus your efforts based on their new needs, starting the cycle again.
The development of a good intelligence process that produces useful information for the audience will improve your chances of being able to implement a sound preparation plan—especially for work in a conflict zone.
Most security departments do not have the resources to dedicate a person to full-time intelligence analysis and reporting, but some larger corporations have seen the value and hired experienced individuals. A company’s level of commitment will be commensurate with the importance that senior leadership places on the risks and their potential impact on operations. But security professionals must understand the elements of the collection process and how they work to paint a picture of risk—doing so will help to develop mitigation strategies that match the needs, expectations, and culture of the organization.
Many security teams have access to sources of intelligence reporting through travel safety programs. Additionally, many companies are eligible for membership in the Overseas Security Advisory Council (OSAC) through the U.S. Department of State. OSAC analysts are readily available to provide member companies with open-source analysis and reporting. Access to this kind of publicly available information, as well as the analysts’ skills, can save security leaders a great deal of time.
Recommendations are of little value if the person providing them does not have credibility.
Additionally, there are several organizations that provide travel safety and intelligence analysis. While many organizations have relationships with these providers, they might not be effectively tapping into their capabilities. Each of them has the ability to accept questions from their member organizations and provide some level of analysis. Often a 24- to 48-hour window will produce very valuable information from on-the-ground sources—beyond what is normally available through open-source information. These same organizations produce reports on a near-daily basis addressing the broad array of risks global organizations are facing.
A good practice is to compare these daily outside reports with your TAI and NAI list. When you see a report that meets the criteria, share it with the impacted stakeholders. By doing this on a regular basis, stakeholders become accustomed to the flow of timely and helpful information. Adding value through the efficient use of the intelligence cycle to multiple levels of the organization is a key element to risk management and makes an effective argument for preparations.
Implementing the Plan
Employing this particular model for intelligence analysis and using available resources to the greatest extent possible helped to establish the credibility AHF’s security team needed in dealing with conflict situations.
In the case of Myanmar, the coup by the military junta and the subsequent civil insurrection caught us off guard. There was little or no warning about the potential of a coup, so the security team found itself in a situation where the intelligence cycle had to be abbreviated to allow for faster decisions. That being said, all of the communication we had had in the past with AHF’s Asia Bureau and in-country program teams helped to establish our credibility regarding crisis response. As we developed a better picture of the situation, the intelligence informed our decisions and those of the people in-country. Thus, even though we did not provide the early warning, the system allowed AHF to respond quickly with reliable and verifiable information.
This is quite different from what occurred during the buildup to the Ukrainian–Russian war. We were able to fully employ the intelligence cycle and—based on our experience—determine early on that the possibility of invasion was very high.
In December 2021, the AHF security team recommended to the leadership at all levels that preparations be made for the possibility of a Russian invasion. This was met with some degree of skepticism at the time. Normally when the security professional has a contrary position, it is overruled by the operational and senior leadership. In this case, however, our previous practice of providing valuable intelligence to decision makers at all levels gave the security team a higher degree of credibility. By employing an effective intelligence cycle and providing regular updates, we were able to leverage our relationship with all levels of management from the country program leadership through to the most senior executives.
Recommendations are of little value if the person providing them does not have credibility. Therefore, having a solid relationship with the stakeholders can be improved by providing them the information they need.
Stakeholder Credibility—Have You Built Trust?
Of all the essential elements of the crisis preparation phase, having a good relationship with key stakeholders and the ability to reach out and enjoy the confidence of the C-suite must be at the top for anyone trying to prepare an organization for the chaotic impact of a conflict zone. The majority of leaders within corporations, businesses, and organizations have not spent time in conflict zones, nor have they spent much time studying them. For most private sector leaders, dealing with active conflicts is not something that occurs on a regular basis.
To be effective when communicating with key stakeholders in times of war, security’s relationship with stakeholders is critical, and it takes time to develop. To do so, security professionals must have a thorough understanding of the organization, its structure, and the key players. Decisions are made by people who are influenced by multiple considerations. Security professionals are one of many factors and voices. If you want your voice to stand out as a conflict arises, you must establish yourself in advance.
Taking the time to do a detailed stakeholder analysis can go a long way in helping security professionals understand where best to try and influence decision making. A simple matrix identifying the players at all levels and their needs can be combined with some type of system that rates them in terms of their willingness to support your decisions and actions. This map will guide the best path forward when seeking champions for security and crisis preparedness initiatives.
Time and experience give the AHF security team an opportunity to do detailed planning regarding stakeholders. Knowing who the critical players are and their needs is helpful. We take the time to establish regular meetings with geographic leadership, conducting monthly meetings to discuss bureau leaders’ security concerns, challenges, and needs helped to establish productive relationships.
Being the professional who looks out for risks and provides solutions or recommendations on how to address those risks should be right in security’s wheelhouse. Having regular conversations with leaders about their needs puts you in the position of being a solution provider, and that value-add reputation is worth its weight in gold.
When the situation in Myanmar emerged, we worked with the local bureau’s leadership to establish a weekly—and later monthly—meeting process to come up with solutions and recommendations.
Regarding Ukraine, by the time we began to prepare for the invasion the relationship was very solid. Because of the security team’s preexisting relationship with leaders at the national and regional levels, preparations and recommendations were carried out cooperatively. We were able to coordinate with internal and external organizations so they would be best prepared. This could not have happened if we did not have a strong relationship built over time.
Conflict Zones—Do You Know Your Operating Environment?
To understand how to operate in conflict zones, one must first understand exactly what a conflict zone is. There are lots of definitions for this term, and some organizations will approach it differently.
Each organization has its own unique tolerance for risk. Many financial or technology companies would find operating in a conflict zone to be beyond their tolerance level as a rule. Conversely, organizations in the extractive industries (mining, oil exploration) often find themselves committed to working in areas where conflicts are quite prevalent. So, agreement on the term as it pertains to your organization will help you as a security professional understand the best way to address the challenge.
AHF agreed upon the definition: “A conflict area or conflict zone is a designated area within which the rights of neutrals are not respected by the belligerents during an armed conflict.” Since AHF is an NGO, its objective is not to become embroiled in the political actions or conflicts found in the countries in which it operates. Instead, the organization focuses on providing “cutting edge medicine regardless of ability to pay.” AHF leadership at the highest level set the standard that we must continue to focus on patient care, provided we did not endanger the lives of our employees in the process.
Having a clear definition of what a conflict zone is—along with agreement about the level of risk your organization is willing to take—essentially determines the parameters in which security professionals must operate in conflict areas. If an organization is committed to remaining in a conflict zone and determined that operations should continue to the greatest extent possible, then there should be a commensurate commitment of resources to support this effort. The level and intensity of the conflict will also drive some of this decision making.
One can argue, for example, that Mexico is a conflict zone due to its heavy losses from transnational criminal organization activity. The question then becomes: What level of resources and commitment are you willing to devote to address this long-term, low-level, crime-driven conflict? Unlike more conventional warfare, this type of conflict can exist for an extended period, and there is little chance that a negotiated settlement will end it anytime soon. Most organizations operating in Mexico have adapted and increased their security requirements to mitigate this risk.
But the situation in Mexico is very different from the conflicts in Myanmar, Ethiopia, and Ukraine. In these situations, the conflict ranks much higher on the spectrum, involving larger-caliber weapons and more organized actions. The level of destruction and intensity of resources required to fight increases as you move towards general warfare. Operating in these environments requires a more detailed plan, and often organizations do not get early warning. For AHF, a good example of that was Myanmar.
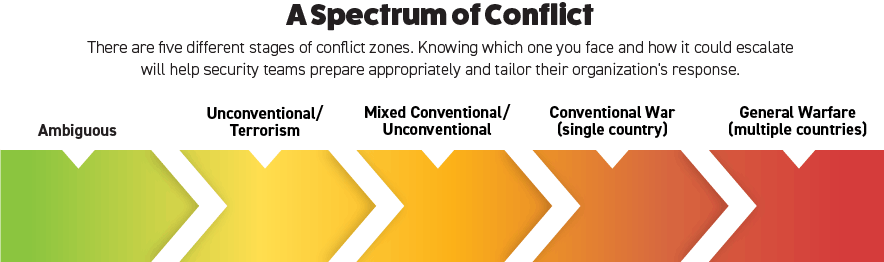
After the initial coup response, the AHF security team began to assess the impact of this shift and how anti-coup forces would respond. Unsurprisingly, this progressed from protest and civil disobedience towards limited attacks against military forces. As this evolved, we took advantage of the time between stages to prepare staff to deal with the escalation. A basic understanding of the spectrum of warfare was very helpful here—this lets security professionals and analysts track conflict between five stages (ambiguous; unconventional/terrorism; mixed conventional/unconventional; conventional war involving a single country; and general warfare involving multiple countries), and it helped the AHF security team explain to leadership where it was on the spectrum and where the conflict was likely to go. The Myanmar conflict moved from the ambiguous zone towards the unconventional/terrorism model. The speed of that progression depended on a number of factors, but taking advantage of the time between stages enabled the organization to prepare and support its people.
AHF decided early on to focus on getting additional funds to staff through an advancement in pay. Based on our intelligence assessment, it was clear that international sanctions were likely to impact the banking system in Myanmar. In addition, the local population would likely move to get its money as quickly as possible, leading to a run on the banks. By working with AHF’s finance department, we were able to get sufficient funding to sustain the in-country staff for an extended period of time, allowing them to get supplies and make up for the lack of notice.
This no-notice situation is the opposite of what happened in Ethiopia and Ukraine. Ethiopia was a mixed conventional/unconventional conflict or limited conventional war occurring within the borders of the country. As the Tigrayan rebels had early battlefield successes, AHF was able to begin the preparation process. Understanding the nature of warfare and how the combatants are equipped is important. The rebels are a foot-based army with a relatively slow rate of progress when compared with modern combined arms forces—traveling about 15 to 20 miles a day at best.
Taking advantage of the time and distance factors allowed the in-country AHF team to complete a detailed response plan and have it reviewed. Communication systems were enhanced, especially our employee emergency communication system, so that we could reach our employees on an as-needed basis. Government forces were able to turn back the rebels, but the planning and preparation were helpful in maintaining employee morale and the confidence of senior leaders.
Preparations for war are not dissimilar for preparations for an earthquake or hurricane.
The earlier warning about the outbreak of war in Ukraine allowed AHF to leverage lessons learned from Myanmar and Ethiopia and have a better response plan. When looking at the spectrum of warfare, it was apparent early on that this would be a limited conventional war. The Russian forces, being largely a mechanized force, were expected to employ a combined arms operations known for intense combat and rapid movement; it was anticipated they could cover as much as 60 miles a day, depending on resistance and weather.
In addition to physical threats, there was a general concern about Russian forces’ ability to engage in cyber tactics. This created the uncertainty that AHF would be able to contact employees through common communication methods. Social media, voice over Internet protocol (VoIP) phones, mobile phones, and apps such as WhatsApp and Signal were expected to be severely impacted by this new form of asymmetrical warfare. Therefore, any plan we created needed to account for a rapidly moving force combined with a significant interruption in communication.
Through an understanding of the continuum of warfare, and with a clear definition of what constitutes a conflict, we were able to develop a plan that fit the AHF’s needs at all levels. As with Ethiopia, we tailored the plan based on anticipated actions. In this case the focus was on developing a much deeper communication plan less likely to be interrupted by cyberattacks and determining where our employees might have to evacuate. As the tensions increased, AHF conducted training sessions with staff, explaining what we anticipated would be the impact of the invasion on them. It was essentially a primer course in modern combined arms warfare with a focus on how to best shelter in place, prepare for evacuation, and make provisions to keep all options open.
By understanding the kind of conflict and having agreement at all levels about the risks, a security professional can make the business case for the preparations needed to keep employees safe and operations rolling. Having a full understanding of the leadership’s tolerance for risk and a continued focus on mission made it possible for AHF to determine how best to respond.
Preparation—Leveraging What You Know
Preparations for war are not dissimilar for preparations for an earthquake or hurricane. A well-developed business continuity and contingency plan will cover all of the critical elements necessary for a security professional’s program to be effective, down to the lowest level of the organization. It’s your ability to leverage the tools of disaster management already in your toolbox that can make you an efficient and effective planner when dealing with war.
In Ukraine, AHF focused on purchasing and distributing supplies and equipment that would allow employees to sustain themselves for seven days. This was expected to be a largely conventional fight with combined arms operations, so airstrikes would likely be intense and thorough. AHF’s employee population had to be prepared to go into civil defense shelters that had been around since the days of the Cold War, and these are rarely heated. The campaign was expected to start in the winter, so among AHF’s recommendations were supplies that would help prevent hypothermia, such as sleeping bags, small camping stoves, and blankets.
Next, we focused on water. In general, each person needs about one gallon of water per day. In Ukraine, the average family size is about two-and-a-half people, essentially meaning they should have two-and-a-half gallons of water per day when they are sheltering. Under a prolonged air campaign, there is a possibility that power and water will be cut off. So, we made sure employees and their families could store the required amount of water for as long as possible and focused on ensuring they replenished it quickly every time there was an opportunity.
Fuel presented another challenge. Many AHF employees in Ukraine owned vehicles. We strongly encouraged them to keep their vehicles full as much as possible and carry as much fuel as they can manage—ideally enough to refill the fuel tank at least once. If the decision was made to evacuate, we anticipated—correctly—that there would be a lack of fuel available. Additionally, the typical distance one can achieve in a day’s drive dropped dramatically. Staff reported that the traffic jams leaving key urban areas were so large that sheltering in place became the best initial option. In one case, a trip that should have taken one day took three. The extra fuel made it possible for them to reach their destination.
One of the most critical tools in any organization’s arsenal is its employee emergency communication system. Most organizations have established some type of emergency communication system that allows them to quickly reach out to their employees, advise them of danger, and get a response back. In many cases, these systems are siloed based on geography or business unit. That being said, if you have the capability to contact all employees in an area where you think war is going to develop, you have an advantage.
Most emergency communication systems are platform-agnostic, taking advantage of phone, data, SMS text, and Internet communication channels. A well-developed system will have all of the critical contact information for every employee kept up to date.
AHF used its system to create a check-in process for all employees. Once a day, typically at about 5:00 p.m. Ukraine time, the system automatically reaches out to local employees asking for their status. If an employee is in danger, he or she can request communication with the country program manager, who would then contact the employee and see if anything could be done to help. In one case, an employee found herself trapped by heavy fighting in an urban area in eastern Ukraine. The communication system was able to get through and allowed us to know her status. Over the course of four days, AHF maintained communication through various means until we were able to get her evacuated. Without the employee communication system, AHF may not have been aware of her situation.
The employee emergency communication system—while key—cannot be the only tool in a security leader’s toolbox when it comes to maintaining situational awareness of employees. AHF also developed and employed a good old-fashioned location plan that relied on latitudinal and longitudinal coordinates to identify nearby employees. We then grouped them so employees were able to reach out and contact each other. This information was put on a map, allowing AHF to see graphically where employees were located.
Taking advantage of this information also allowed us to help plot evacuation routes. As the war progressed and situations became untenable for employees, they would request the best evacuation routes. Using the intelligence assets available to us, AHF’s security team was able to identify the best route to the desired destination for any employee who asked.
One final point that cannot be overlooked is providing the financial wherewithal to meet these preparation needs. During an emergency, the supplies in question—extra food, fuel, and water—cost above and beyond what a typical employee can afford. Experiences in other crises such as Myanmar and Ethiopia had proven to AHF leadership the importance of making financial resources available at the right time. Senior leaders began discussing how to get employees additional funds from the moment they realized that the situation in Ukraine could become much worse. As a result, all employees were provided an additional 30 days’ pay as a backup. This gave them enough money to purchase emergency supplies, and it left them with a comfortable margin going forward.
There were significant doubts about whether Ukrainians would be able to access the banking system during the conflict, especially since financial transactions are typically done using the Internet. This conflict’s cyber risk made cash all the more important. Having dealt with this in the past, AHF’s finance team was prepared and had developed a procedure to make sure cash was available when needed.
Personnel Safety—A Critical Question
Knowing employees’ locations during a conflict is critical. Most executives are primarily concerned with the safety of their employees in these situations, and you cannot answer their questions if you don’t know where employees are.
The two most important addresses that security leaders need to know are employees’ work and home addresses. But each country, sometimes each locality, has its own way of determining addresses. The best way to get this information in a fashion that is consistent and standardized is to get the latitude and longitude for each address. This is not as complicated as it seems with modern technology. There are any number of platforms and apps available that will allow you to determine the latitude and longitude for every location.
In any wartime situation, the battlefield is very dynamic and can change quickly. So, employees should have a primary, secondary, and tertiary location. The primary location is typically their residence or somewhere near where they will shelter in the event of war. A secondary location should be a place that they can move to within about one to two days travel by vehicle. Road conditions will affect how far this is, but typically it’s 60 to 120 miles from their primary location. The tertiary location should be an equal distance beyond that.
Often there’s a break in contact when communication channels are shattered by combat actions. As with a hurricane or earthquake, having a plan that advises your employees to identify their secondary and tertiary locations before an emergency hits will pay dividends should they have to move quickly. When communication is reestablished, the in-country team leadership will have an idea where to start looking for employees or trying to contact them. This will allow leaders a better understanding of the impact on operations and what can be done to assist employees.
Results—What Really Matters
All of this effort occurred during the span of approximately six weeks prior to the invasion of Ukraine. As it became increasingly clear that some type of action was going to occur, the early preparation allowed AHF personnel to continue with their primary mission, even as others were scrambling to respond.
The old saying that “prior planning prevents poor performance” was definitely in effect. Taking the time to build trust in advance allowed us to engage in well-developed preparation plans that helped to mitigate risks. Preparedness enabled employees to take care of themselves and their families, which freed them up to continue fulfilling AHF’s mission of caring for patients.
For the organization’s leadership, this was the source of some comfort. And as the situation progressed, it became clear that others were not as well prepared, so we found ourselves in a position to aid more patients because we had also worked to secure medication in advance. The result has been that all of our patients have continued to receive care. And this may be the strongest argument one can make for the investment in preparation. n
Ralph “RC” Miles is the global director of safety and security for the AIDS Healthcare Foundation (AHF). He has more than 25 years of private sector experience in the design, development, and implementation of comprehensive security, investigations, and intelligence strategies in a variety of business climates and organizational cultures. Prior to his civilian career, Miles spent nine years serving as an officer in the U.S. Army in various assignments around the world.










