The Critical Role of C-UAS in Perimeter Security Systems
 At the turn of the 21st century, the U.S. military deployed its first modern operational unmanned aircraft system (UAS). It used UAS in two wars—Afghanistan and Iraq—to conduct a variety of missions for operational and tactical support.
At the turn of the 21st century, the U.S. military deployed its first modern operational unmanned aircraft system (UAS). It used UAS in two wars—Afghanistan and Iraq—to conduct a variety of missions for operational and tactical support.
The value proposition for these devices is clear: Complete increasingly complex missions while reducing the number of troops on the ground, keeping them out of harm’s way.
Today, drones are widely implemented by both military and commercial customers. This shift toward UASs also rapidly accelerated the development of technologies needed to manufacture drones, allowing them to proliferate in commercial markets as well. In fact, the global commercial UAV market is expected to reach $501.4 billion by 2028, registering a compound annual growth rate of 57.5 percent from 2021 to 2028, according to a new report by Grand View Research, Inc.
For security managers at airports, nuclear power plants, oil refineries, and other critical infrastructure sites, these commercial drones pose a novel threat. In fact, in recent months, the industry has seen drones refitted to perform several malicious tasks, including an assassination attempt in Iraq, the transport of illegal cargo in Virginia, a terrorist attack in Minsk, and an attempted attack on the Northeast electrical grid, the first documented drone attack intended to deliberately damage U.S. energy structure.
Why C-UAS?
These examples demonstrate how perimeter security breaches today have evolved beyond intruders on the ground. To respond to new aerial risks, numerous Counter UAS (C-UAS) strategies have arisen to bolster perimeter intrusion detection systems (PIDS).
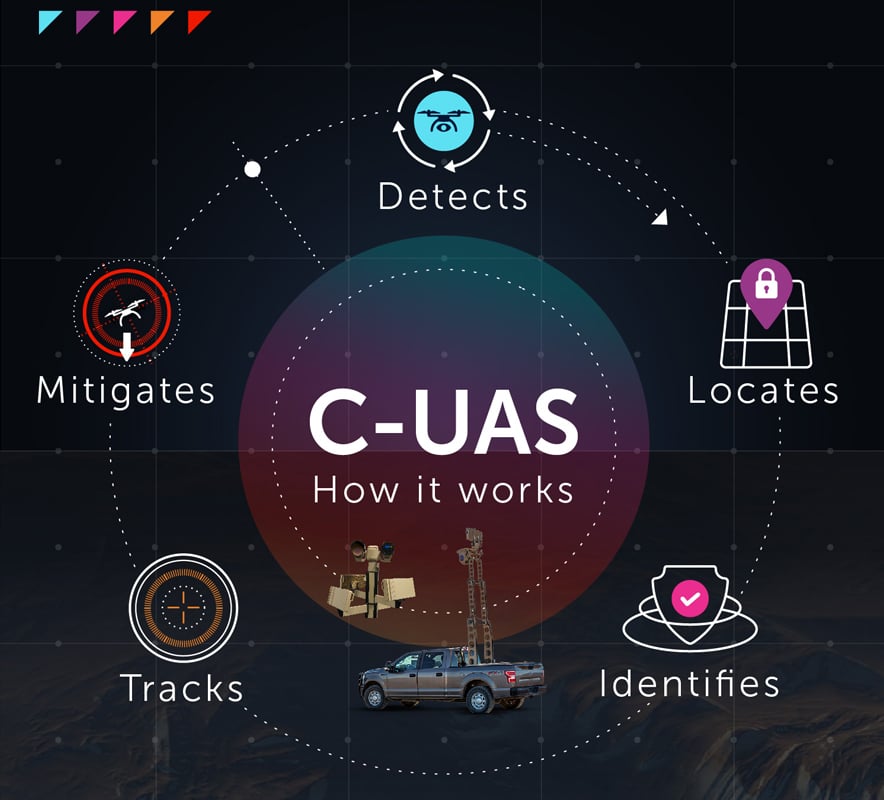
What matters first and foremost is that any PIDS deployed keeps people and property safe—from ground- and air-based threats alike. For a PIDS to do so, it must be able to meet every conceivable threat head on. For this reason, security managers are investing in multi-faceted C-UAS technologies to detect, identify, locate, track, and mitigate incoming adversarial UASs.
A Multi-Layered Strategy
The leading C-UAS approach is to layer multiple sensors with proven performance in the field for faster, more reliable threat recognition and response. As part of this strategy, security personnel are deploying long-range radars to deliver 360-degree detection coverage, scanning areas three to four times per second; these radars detect everything from pre-programmed or customized drones to parachutes, mylar balloons, and small aircraft. Radio frequency (RF) sensors are also commonly used to detect UASs.
The leading C-UAS approach is to layer multiple sensors with proven performance.
Security managers are then pairing radar and RF devices with multi-sensor EO/IR cameras that feature daylight sensors and high-definition thermal sensors, Convolutional Neural Network analytics—which build artificial neural networks and then teach a computer to classify distinct, pixel-level similarities between different kinds of objects—as well as other specialty software that enables classification and auto-tracking of all targets. As UASs can quickly shift position, having robust and redundant tracking capabilities is critical.
Lastly, security teams are also integrating effectors into C-UAS platforms, which are designed to either jam or spoof adversarial drones as part of real-time response efforts. Essentially, jamming RF and GPS communications links render enemy drones inoperable, while spoofing technologies take control of enemy UAS systems by deceiving GPS signals to the UAS’s receiver. By bringing these first-class technologies together, security operators are better equipped to detect, classify, and mitigate UAS targets, 24/7.
Neutralizing UAS
That mitigation might also include neutralizing a drone that’s flown into the airspace being monitored by the security team. When initiating a C-UAS kill chain, or plan of attack to identify and neutralize UASs, there are five key steps:
- Operators must use radar, RF devices, and multi-spectral cameras to detect a drone that has flown into their airspace.
- Security teams must identify whether the drone is a true threat, such as by assessing video analytics and RF and radar signatures.
- Through the C-UAS platform management software, personnel locate the drone on a 3D map.
- Operators use radar—or specialty cameras—to track the position of the drone.
- Security personnel counter the drone using non-kinetic strategies, such as jamming or spoofing, or kinetic methods, such as disseminating nets, launching projectiles, or pointing laser or microwave beams to destroy the drone’s airframe. The strategy could combine methods.
Important Lessons
With UAS threats growing every day, security directors at critical infrastructure organizations can no longer afford to consider a C-UAS solution as an add-on feature to their PIDS. When strategically designed to integrate the highest performing technologies, C-UAS platforms can minimize risk by quickly locating and neutralizing adversarial threats.
Kai Moncino is director of global business development, security, at Teledyne FLIR. In his current role, Moncino is responsible for strategy creation and execution for the security vertical business. His focus areas include developing relationships with key customers and establishing strategic alliances with industry partners. Moncino has worked at Teledyne FLIR for more than eight years, holding several positions during his tenure at the company, including mechanical engineer, product manager and strategic global business development manager.
