Stalkerware Fuels Technology-Enabled Abuse
Before the onset of the COVID-19 pandemic, one in three women worldwide had experienced intimate partner violence (IPV), according to Harvard Medical School research. But pandemic-related lockdowns and stay-at-home orders have resulted in sharp upticks in cases. In France, domestic violence reports rose more than 30 percent. In Latin America, reports of intrafamily violence against women climbed sharply; in Colombia, violence against women between 29 and 59 years old spiked 94 percent between March and May 2020, according to The Washington Post.
However, not all countries are recording rises in cases. In the United States, rates in some regions fell by more than 50 percent, according to The New England Journal of Medicine. But advocates warn that these numbers may be misleading—victims trapped at home with their abusers may be unable to safely report incidents or get help.
Additionally, typical watchdogs for abuse—such as teachers, coworkers, clinicians, and friends—have had limited touchpoints with potential victims since the start of the pandemic.
These conditions leave people of all ages and genders at risk for increased abuse, and they offer abusers additional time and resources to track, coerce, and trap victims—including technology.
Long before the lockdowns, smart technology, including Web-controlled locks, lights, thermostats, and cameras, had been misused to monitor, stalk, harass, or intimidate. With abusers and victims trapped at home together for long periods, the opportunity to reconfigure these devices for malicious purposes has expanded, says Eva Galperin, director of cybersecurity for the Electronic Frontier Foundation (EFF).
For example, when Ferial Nijem moved into a smart home, Internet of Things devices provided new levels of convenience and personal control over her environment—everything from the lighting to the climate control was connected. However, her partner hijacked the system, using surveillance cameras to monitor her movements, turning on music in the middle of the night, flickering the lights, and turning off the television. He had configured the smart home system, and Nijem could not override the controls.
“It’s almost as if the house is haunted,” Nijem told the CBC in 2018. “It is only done to cause you trauma, to cause fear, to cause anxiety.”
The amount of technology in homes has only increased since then, especially as the pandemic forced people, organizations, and educational institutions to turn to remote work and virtual schooling. The number of devices operating through home networks puts victims—and their organizations—at further risk.
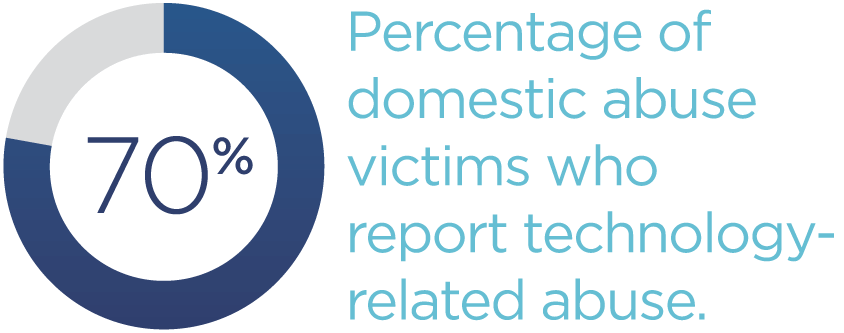
According to domestic violence charity Refuge, more than 70 percent of those it provides support to have reported technology-related abuse within a relationship, the BBC reported. This has extended to more commercially available technology like virtual assistants, smart speakers, smart watches, or doorbell cameras. Many of these devices are connected to credit card details, such as Amazon’s smart speaker Alexa, so control of the device can give abusers control of financial details, too.
Beyond controlling devices, abusers have also turned to malware—so-called stalkerware or spyware has been used to track victims’ devices, the websites they visit, the phone numbers they call, and the text messages they send. The commercially available tools can turn on a smartphone’s camera or microphone to let perpetrators listen in on conversations or see where the victim is or what he or she is doing. Oftentimes the perpetrator can record calls or activity, which could be used later to blackmail the victim.
The majority of stalkerware downloads require physical access to devices, but if victims are locked down with their abusers for months on end, the opportunities to covertly access a device and add a stalking or monitoring tool are broad. The risks also extend to work devices—if a perpetrator infects a victim’s work phone or laptop with stalking malware, he or she could collect sensitive professional information or intellectual property to exert control over the victim or take revenge on the victim or his or her employer down the line.
Remote workplace management tools—such as productivity trackers or employee monitoring software, known colloquially as bossware—serve similar functions as stalkerware, says Galperin, and the use of these tools may normalize the sort of virtual spying that abusers use to track victims. In addition, many remote work monitoring or proctoring apps are poorly made and not particularly secure, she adds, which increases the possibility that they could be misused or hijacked for nefarious purposes—by a partner, a fellow employee, or a malicious outsider.
![]()
“The ability to see what people are doing inside of their homes and the ability to see what they are doing during non-office hours is also extremely invasive,” Galperin says. Employees are also in a position where they are unlikely to refuse monitoring software, especially during a time rife with economic uncertainty and high unemployment. If a toxic coworker or manager begins to abuse the remote monitoring system, the employee may not feel empowered to speak out. Similarly, employees may not feel they are in a safe position to disclose abuse threats—virtual or physical—with their employer.
Domestic abuse and IPV affect workplace safety, particularly where active assailants or workplace violence risk mitigation is concerned. The technological component adds another layer to this challenge, making IPV a cybersecurity issue as well as a physical security and employee safety issue.
Where employers are concerned, “if stalkerware is installed on an employer-supplied device, that is not just a risk to the employee, it is a risk to the employer of insider threat, and it should be treated like that,” Galperin adds.
Security professionals can team up with their IT counterparts to run education and awareness campaigns about malware, stalkerware, and cybersecurity, in addition to sharing information about physical abuse, IPV, workplace violence, and resources available to help victims. Organizations can also provide and promote alternative methods of reporting abuse or requesting assistance, especially if abusers may be taking advantage of or monitoring technology.
“I don’t think that a lot of awareness programs really encompass the idea that this is abuse, but some of it is also a lot about how the programs discuss stalking and harassment. We don’t often see awareness campaigns call out this type of software explicitly,” Galperin says.
“There’s a lot of talk about how this kind of surveillance enables abuse and how it leads to abuse, but I think we really need to reframe and talk about how the surveillance itself is abusive,” she adds. “Secretly tracking the location or messages or passwords or phone calls of your partner—that’s abuse.”
