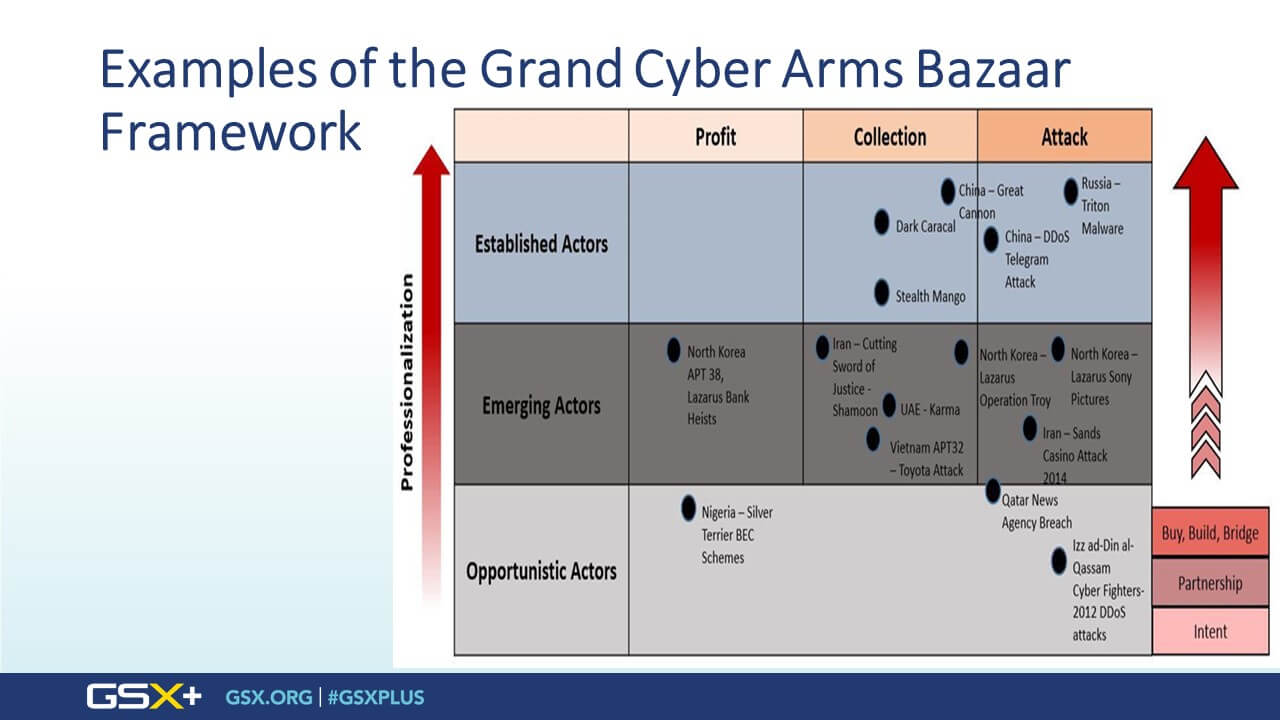
The Cyber Threat Landscape Becomes More Complex
If your aim is to break into computer systems to steal information; hold people, companies, or governments hostage; compromise capabilities; or otherwise create mayhem, then there has never been a better time to act than now.
What previously was only achievable with highly sophisticated expertise that often took years to develop is now available through ready-made cybercrime tools, offered for purchase, for hire, or sometimes just offered freely through online forums and connections. All of this drastically lowers the barrier of entry for individuals, crime syndicates, or nation-states that want to attack a target.
You can learn more about this developing landscape in the GSX+ session “Commodification of Cyber Offensive Capabilities” led by Ice Miller, LLP’s Guillermo Christensen on Tuesday, 22 September, at 12:25 p.m. to 1:15 p.m. EDT.
In the session, Christensen describes how an expanding array of state and nonstate actors have access to various cyber tools or weapons, which may be employed for collection, financial gain, surveillance, or attack. The risk is even greater when the low entry barrier is combined with the growing connectivity of systems, which opens a larger attack surface, expands the scope and reach of what threat actors can do, and can cause collateral damage to systems and entities beyond the intended target.
The GSX+ Daily had the opportunity to interview Christensen on the threats he describes in his session and what they mean for those responsible for securing a company’s information systems.
GSX+ Daily: What does the term commodification mean in relationship to cybersecurity?
GC: This was a term we came up with after a lot of thinking about the core concepts we wanted to talk about. Proliferation was part of it, as was lowering the barrier of entry. But when it comes down to it, with commodification, the concern we have is the combination of the easy accessibility of hacking tools and a growing sophistication level enabling the weaponization these tools. This used to be the realm of the most advanced nation-states, but now there are a growing number of these sophisticated attacks.
What makes some attacks more sophisticated than others?
GC: It’s not just a line of code. The code might enable entry into a targeted system without triggering the alarms and sensors that most organizations have put in place to try guard against cyber intrusions. Once they get in, they want to stay in for as long as possible for many reasons. That type of approach involves more than just technology; it’s tactics and logistics they use to persist in the system for a long period of time and spread to other systems and find vulnerabilities.
Hacking tools have had a market for a long time. These combined applications are now available at price points and easy-to-use configurations that will result in a proliferation of the kinds of attacks that could only be undertaken by the likes of Russia or China or the United States before.
You introduce the concept of a cyber red line in the session, what does that mean?
GC: We borrowed from the military realm and concepts of deterrence. The idea is that there are certain red lines that countries will not cross in military conflict. An example, after World War II use of biological or chemical weapons was a red line, and crossing that line would have consequences for a country. Hospitals are another one. You don’t target hospitals.
In the context of cyber warfare, there are red lines that most of the civilized world would agree that you don’t cross in malicious activity or attack or espionage. In the early stages of COVID, there was a lot of talk about not targeting organizations that are involved in COVID-19 research—and that obviously didn’t last very long. But what about hospitals? Should we expect an attack by a reputable nation-state group on a hospital system that causes suffering and death, should that be a red line? And the real question is what do you do about it? How do you respond? So what we’re concerned with is there isn’t a clearly defined set of red lines —whether formalized by treaty, akin to nonproliferation agreements, or more informal ideas that could eventually be codified by international law or treaty—around what the civilized world might believe are activities, assets, or parts of our society that should be off limits to a cyberattack.
In terms of this increased threat, what do those charged with protecting systems need to be thinking about?
GC: I think there are two things. First, you need to build a much greater understanding of your supply chain and the digital welfare of that supply chain. You need to understand if your business has critical assets exposed to the kinds of threats that this kind of environment creates. As a quick example, if you have critical supply chain assets in India, you need to be mindful whenever there are increased tensions between Pakistan and India. Do you have system integrations with the Indian assets? How closely is that Indian asset tied to Indian institutions and how likely is it that the company itself could be a target? How will that asset’s capabilities be compromised if an attack causes major disruption to Indian infrastructure? These are the types of things that would need to be part of your company’s resiliency planning.
The second thing is to understand the extent to which your company may be perceived as being on the side of one state versus another and the likelihood that you may be more exposed as a result. In such cases, you need to not only be concerned about run-of-the-mill cyber criminals, insider threats, IP theft, and the like, but also that your company would be a target by someone more likely to be going after it for an objective that is perhaps not organic to the company’s business itself, but because it sends a message or it’s useful to propagate an attack that extends into other parts of the economy.