Attackers Exploit Trust in PDFs
03/08/2011 -Hackers have grown increasingly attracted to using PDF attachments to carry out targeted cyberattacks, cautions a new cybersecurity report.
"PDFs are potentially one of the most dangerous file formats available and should be treated with caution, much as [executable] files should be,"according to the Symantec.cloud MessageLabs Intelligence report(.pdf). "Because it is significantly easier to generate legitimate and concealed malicious content with PDFs, they are much more dangerous than [executables]."
According to MessageLabs, Microsoft Office documents—like Word and Excel—were traditionally the attachment of choice for targeted attacks: whereby the cyberattacker directly targets an e-mail address rather than just spamming it.
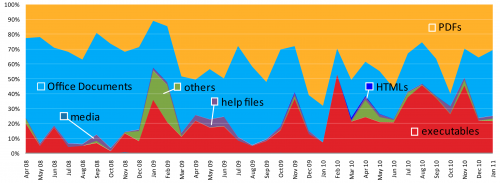
But in between April 2008 and now, the trend has flowed away from Office documents and towards PDFs. The popular file attachment is now the attachment of choice for hackers and the percentage of attacks using PDF files will continue to grow, reports Prashant Gupta, threat research and respond manager at Symantec.cloud.
In 2009, a little over half of all targeted attacks used PDF exploits. This jumped to 65 percent in 2010. MessageLabs estimates that if the current trend continues, three out of every four targeted attacks will leverage a PDF exploit by the middle of this year.
MessageLabs Intelligence, however, clearly notes that hackers' gravitation toward PDF files doesn't mean e-mail users should lower their guard on other file attachments. All it means is that hackers, with the help of moreattack toolkits coming on the market, have made other formats "more popular as attack vectors."
The report advises e-mail users to be wary of all e-mail they receive.
"As will all malware over the years, the most effective means of protection is to be aware of the risks and use caution when dealing with any content delivered to a mailbox," MessageLabs advises. "Social engineering is often the key to the success of these types of attacks, so even if a security solution cannot safeguard the computer, then the last line of defense should be the user."