An Increasingly Connected ICS: Highlights from Dragos’ 2020 Year In Review
 Each year Dragos, Inc., publishes its Year in Review (YIR) report, which is an analysis of Industrial Control System (ICS) and Operational Technology (OT) focused cyber threats, vulnerabilities, assessments, and incident response insights. The report is based on data gathered from annual service engagements conducted by the Dragos team of ICS cybersecurity experts and the on-going work of the Dragos Threat Intelligence team. It shows progress made and improvements required to provide safe and reliable operations.
Each year Dragos, Inc., publishes its Year in Review (YIR) report, which is an analysis of Industrial Control System (ICS) and Operational Technology (OT) focused cyber threats, vulnerabilities, assessments, and incident response insights. The report is based on data gathered from annual service engagements conducted by the Dragos team of ICS cybersecurity experts and the on-going work of the Dragos Threat Intelligence team. It shows progress made and improvements required to provide safe and reliable operations.
In 2020, the industrial community performed amazing feats to keep civilization running under the extremely challenging circumstances of the global COVID-19 pandemic. Infrastructure providers kept key services and goods available including electric power, manufactured goods, water, oil and gas, mining, chemical, rail, and transport while many faced hardships globally. As a result of these efforts, organizations shifted in how they conducted business to include an increasingly connected industrial environment. This trend has existed for many years, even while many organizations still believed they had highly segmented or even air-gapped ICS networks.
Activity Groups Increase by 36 Percent
Cyber risk to industrial sectors has grown and accelerated dramatically, led by ransomware impacting industrial processes, intrusions enabling information gathering and process information theft, and new activity from adversaries targeting ICS.
Throughout 2020, the 11 Activity Groups identified by Dragos prior to 2020 remained active against industrial organizations. An Activity Group (AG) is a set of intrusion events related with varying degrees of confidence by similarities in their features or processes. AGs are used to answer analytic questions and develop broad mitigation strategies that achieve effects beyond the immediate threat. Dragos identified four new AGs in 2020:

These new groups represented a 36 percent increase in known groups overall. Other major ICS threat trends in 2020 included:
- Phishing exploits continue to enable ICS intrusions
- Remote access directly to ICS was often leveraged by threats
- The beginning of ransomware specifically targeting ICS
- Supply chain concerns amplified by limited visibility in ICS
Vulnerabilities Grow 29 Percent
According to the National Institute of Standards and Technology (NIST), a vulnerability is a weakness in an information system, system security procedures, internal controls, or implementation that could be exploited or triggered by a threat source.
Adversaries exploit vulnerabilities to gain unauthorized access to a computer system. After exploiting a vulnerability, a cyberattack can run malicious code, install malware, steal sensitive data, or halt operations and/or assume control of ICS. Many vulnerabilities impact ICS software, placing the customers using the software at a heightened risk of a data breach, or supply chain attack.
Dragos researchers analyzed 703 ICS/OT vulnerabilities in 2020, a 29 percent increase from 2019, demonstrating a rise in publicly known flaws in systems supporting industrial operations. Practitioners struggle to prioritize these vulnerabilities due to errors and a lack of actionable guidance in advisories. This is the case whether a patch has been announced for these vulnerabilities or not. In 2020, Dragos found that 43 percent of vulnerability advisories had incorrect data.
The U.S. Department of Homeland Security established the Industrial Control Systems Cyber Emergency Response Team (ICS-CERT). ICS-CERT publishes advisories regularly that list the Common Vulnerabilities and Exposures (CVEs) that have been published by different software vendors.
CVEs are scored using the Common Vulnerability Scoring System (CVSS). CVSS is a free and open industry standard for assessing the severity of computer system security vulnerabilities. The National Infrastructure Advisory Council (NIAC) launched the CVSS scoring system in February of 2005, with the goal of being “designed to provide open and universally standard severity ratings of software vulnerabilities.”
CVSS scores are calculated for each CVE based on a formula that depends on several metrics that approximate ease of exploit and the impact of exploit. Scores range from 0 to 10, with 10 being the most severe. Though originally CVSS was designed with Information Technology (IT) systems in mind, the scoring system has been utilized in ICS environments as well.
Dragos reviews ICS-related advisories, including those from ICS-CERT and adds actionable information to them, adding relevant port and protocol information, or determining if the control or view of the process is affected, and if there are alternative mitigations in place regardless of a patch. Dragos also provides corrected CVSS scores based on the vulnerability and how it can be leveraged. This enables practitioners to prioritize these CVEs according to their own environments and to focus on the most severe issues, first.
Below is an example of the CVSS corrections that Dragos provides for some recent CVEs. Click on the link below to see the original advisory from OSIsoft.
OSIsoft PI System (Update A) | CISA
- CVE-2020-10614
- 4 => 4.8
- AV:N/AC:L/PR:H/UI:R/S:U/C:H/I:L/A:H => AV:N/AC:L/PR:H/UI:R/S:C/C:L/I:L/A:N
- CVE-2019-11358
- 5 => 6.1
- AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:H/A:N => AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N
- CVE-2020-10643
- 5 => 5.4
- AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:N/A:N => AV:N/AC:L/PR:L/UI:R/S:C/C:L/I:L/A:N
The above advisory was also confusing because it listed two different vulnerabilities as the same CVE.
Dragos uses a Now, Never, Next scenario to analyze and prioritize vulnerabilities, as shown in the figure below: In 2020 Dragos found that:
- Only 7 percent of vulnerabilities fell into the Now category, requiring immediate reaction
- Thirty percent of vulnerabilities were in the Next category, meaning lower priority threats that might be exploitable but are present deeper in the network and require more work, access, and knowledge for an adversary to exploit or impact OT processes.
- The remainder, 63 percent, were in the Never category, posing a possible threat but rarely require action in vulnerability prioritization.
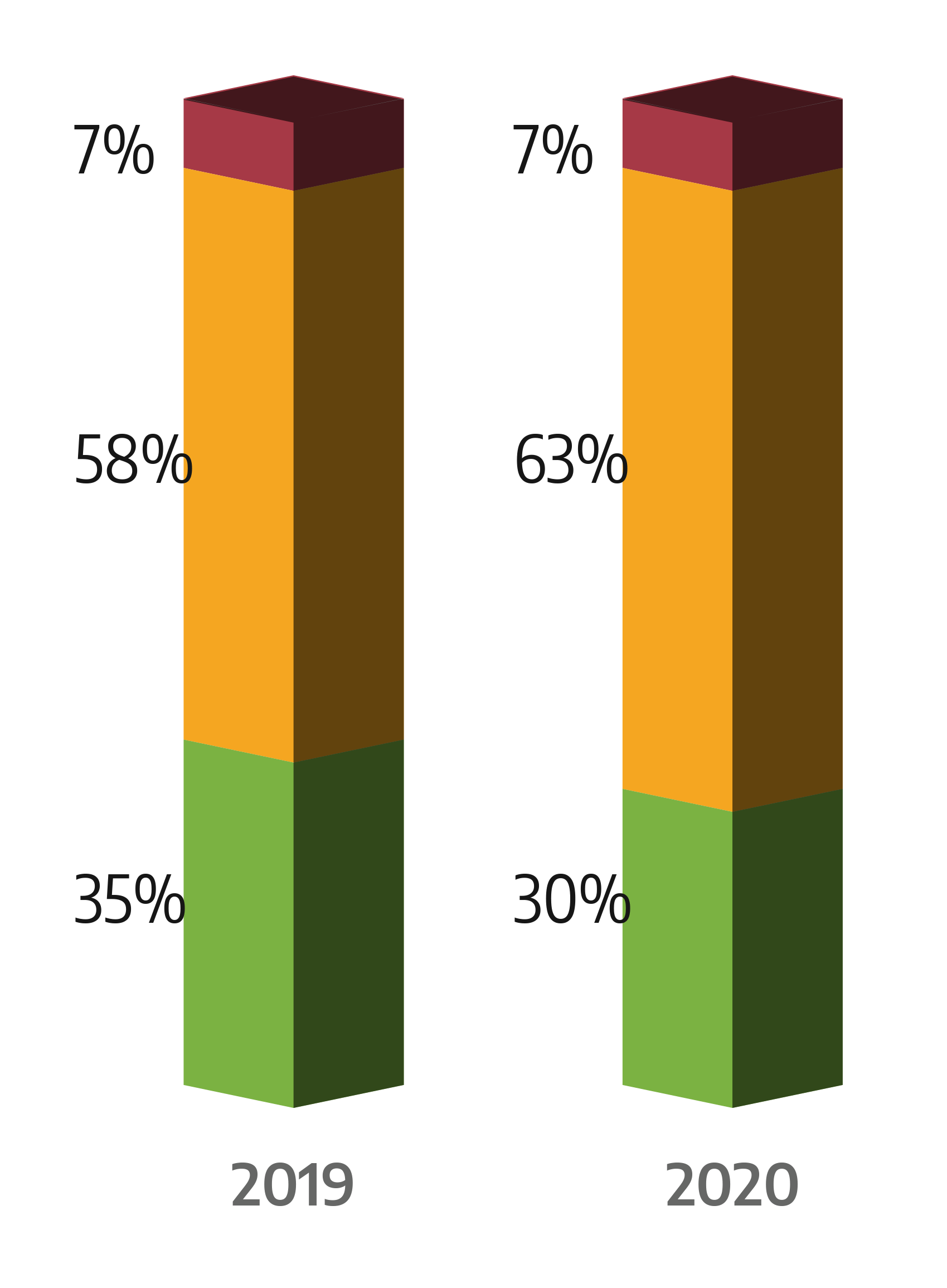
The YIR also identified several third-party vulnerabilities in the software supply chains impacting ICS systems. Most notable were Ripple20 and Amnesia:33 vulnerabilities in third-party Internet Protocol (IP) stacks from ICS vendors. Third-party stacks are used in many embedded products, including some industrial-supporting products and IT systems. Embedded products could include programmable logic controllers, sensors, actuators, or processors, for example.
Lack of Visibility Persists in ICS Environments
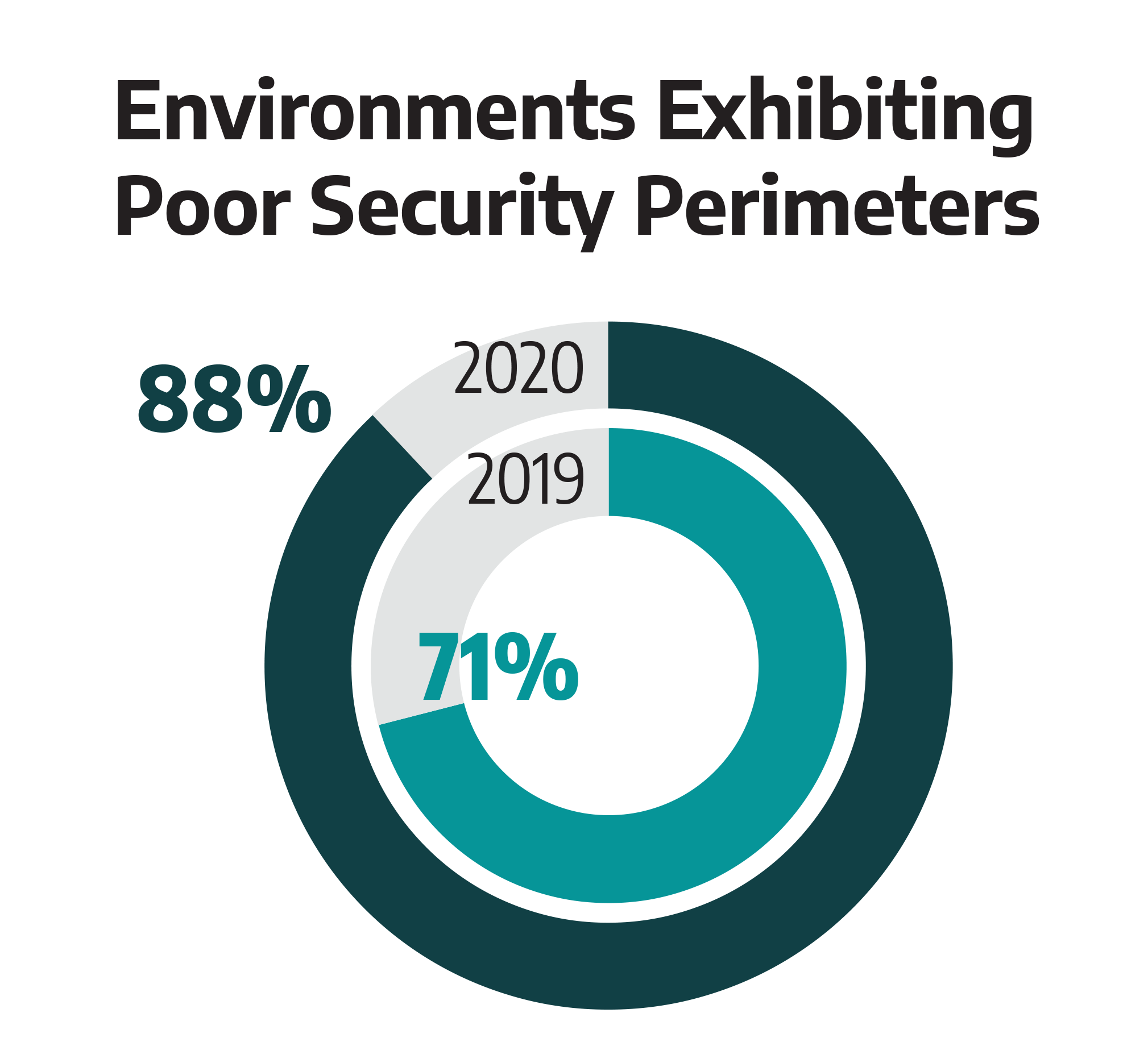
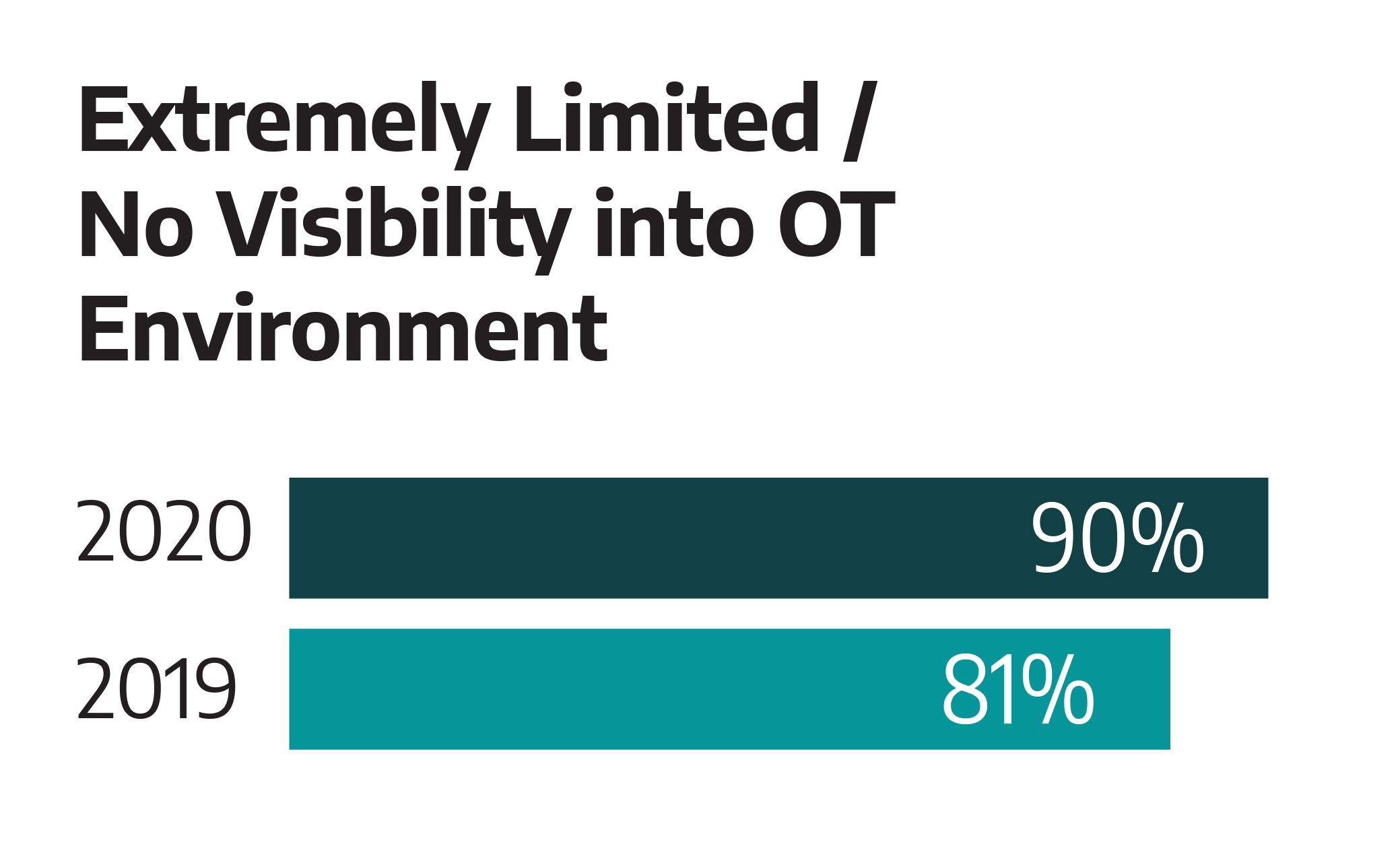
Most Dragos’ services customers had no visibility into their ICS environments. While most customers demonstrated a focus on an enhanced asset inventory, this effort is only the foundation for asset visibility. Many customers only monitored the IT to OT boundary without monitoring activity inside the ICS network. Dragos continues to observe instances of poor segmentation with unexpected or unknown connections from the ICS network.
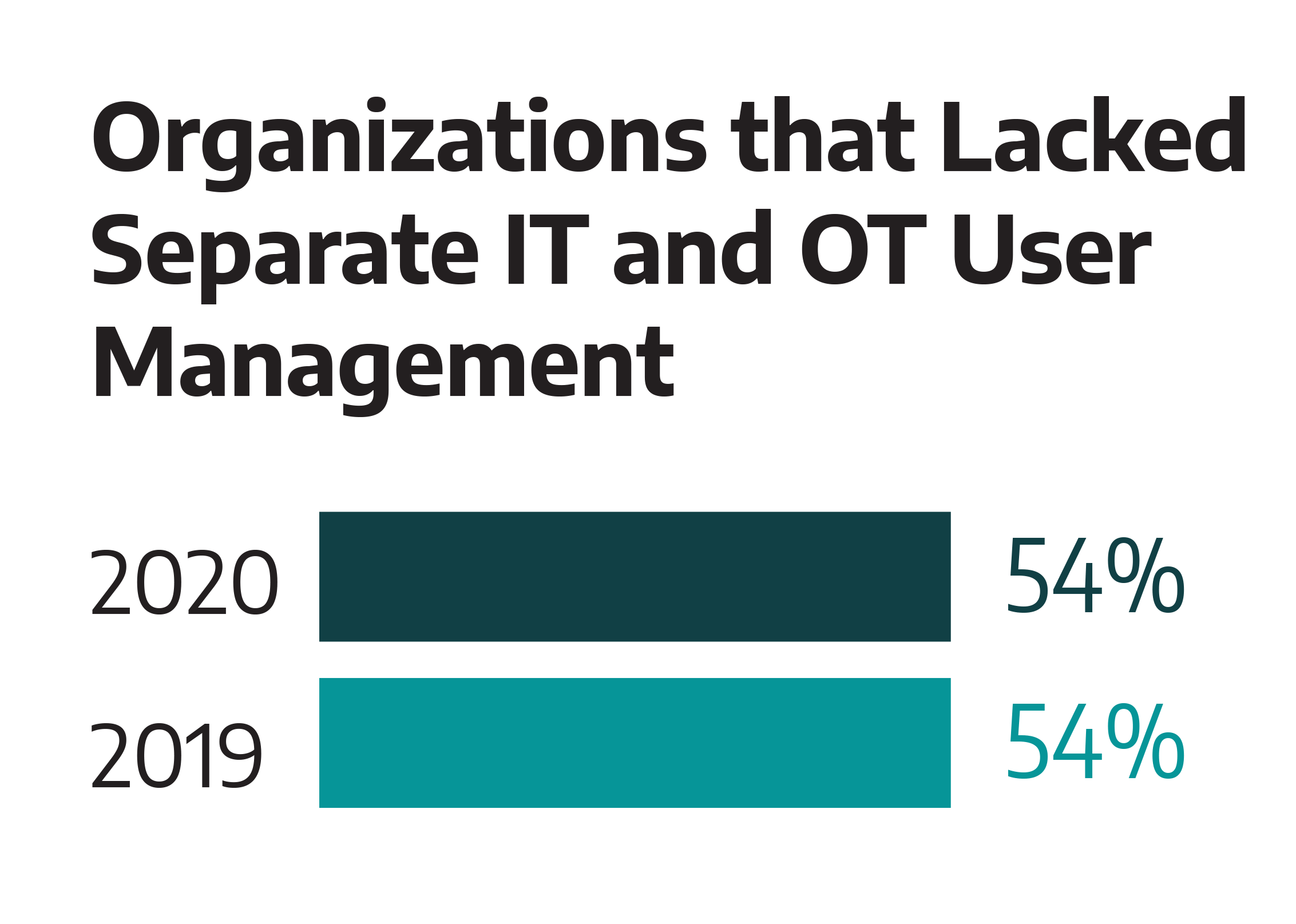
Organizations that Lacked Separate IT and OT User Management organizations continue to frequently share credentials between IT and OT networks. The most common reason for sharing credentials—including using the same passwords and logins for both IT and OT networks and/or direct connection between computers and software on both networks—comes down to time and not understanding or using proper protocols.
Additional findings are summarized in the figure below.
In all the incident-response cases Dragos worked on, the attackers gained access to the victim's ICS network via the Internet, and shared IT and OT credentials were used to move laterally in the network. Dragos threat data shows the abuse of valid accounts and shared credentials are favorite methods employed by Threat Activity Groups.
Top Five Recommendations to Enhance ICS Security
Dragos recommends five key OT cybersecurity initiatives to improve on in 2021 to enhance the security of an ICS:
- Increase Network Visibility. Ninety percent of service engagements included a finding about lack of visibility. Visibility includes network monitoring, host logging, and maintaining a Collection Management Framework (CMF).
- Identify and Prioritize Crown Jewels. All external routable network connections to ICS environments were believed to be air-gapped. Crown Jewel Analysis identified a digital attack path to impact a critical physical process.
- Boost Incident Response Capabilities. Forty-two percent of customers did not have a suitable Incident Response Plan and 75 percent had difficulty with declaring a cyber incident.
- Validate Network Segmentation. Eighty-eight percent of services engagements included a finding about improper network segmentation, including issues like weak segmentation between IT and OT networks, permissive firewall rulesets, and externally routable network connections.
- Separate IT and OT Credential Management. Fifty-four percent of service engagements included a finding about shared credentials. This includes accounts shared between IT and OT, default accounts, and vendor accounts.
Click here to download the full Dragos YIR report.
Sergio Caltagirone, vice president of threat intelligence at Dragos, is committed to tracking down hackers and safeguarding civilization. In nine years with the U.S. government and three years at Microsoft, Sergio has hunted the most sophisticated targeted threats in the world, applying intelligence to protect billions of users while safeguarding civilization through the protection of critical infrastructure and industrial control systems. He co-created the Diamond Model of Intrusion Analysis, helping thousands of others bring more pain to adversaries by strengthening hunters and analysts. Caltagirone also serves as the technical director of the Global Emancipation Network, a non-profit, non-governmental organization (NGO), leading a world-class, all-volunteer team dedicated to ending human trafficking and rescuing victims through data science and analytics, saving tens of millions of lives.
