When Personal Branding Becomes Personal Risk
The benefits of establishing a personal brand are plentiful, but so are the risks. As security professionals launch and cultivate their personal brands on public-facing channels such as social media, they can draw attention to themselves. While increasing security’s profile is not necessarily a bad thing, understanding the risks and challenges is essential.
In the third installment of the ASIS CSO Center Leadership Series, “It’s Your Personal Brand: What Could Possibly Go Wrong?,” sponsored by Resolver, Counterintelligence Institute founder Peter Warmka will discuss how a security executive’s public profile can affect his or her level of physical and cyber risk, as well as reputational risk for the organization.
Two main areas to watch for are the loss of sensitive data or intellectual property and reputational damage, he says.
“Data leakage or theft, the premature release of sensitive information critical to the organization's overall approach, and the theft of intellectual property may all result in costly losses and even trigger a company's collapse,” Warmka tells Security Management. “Such incidents aren’t necessarily the product of sophisticated assaults; in many situations, people are very vulnerable to social engineering.”
When someone sends you a connection request on LinkedIn, how do you know if it's genuine? https://t.co/qT4782J0AG pic.twitter.com/YhoaTlz9jR
— Security Management (@SecMgmtMag) February 25, 2019
In a social engineering attack, a threat actor can use social media sites like LinkedIn to identify key insiders at an organization and then analyze the insider’s profile and posts to identify potential motivations or vulnerabilities that the actor can use against the insider. For example, a malicious actor could use a CSO’s post about her love of skiing or interest in learning about cybersecurity skills to form some fake common ground.
“The human hacker can approach the target utilizing spear phishing, smishing, vishing, and face-to-face interaction,” Warmka says. “Social media platforms are replacing email as the most effective means of delivering successful spear-phishing campaigns. The attacker can create a fake profile which incorporates commonalities with their target. The target is then more likely to trust and accept an invitation request to connect.
“Once connected, the social media messaging feature can also carry a malicious link to be clicked on or malicious attachment to be opened.”
Malicious actors can also use public-facing social media pages to impersonate individuals or companies, creating bogus sites and profiles to spread false information or manipulate people into handing over passwords or private information. These threats put personnel and their contacts or customers at risk, threatening internal networks and accounts.
“When receiving a connection request, the security professional should carefully analyze the profile for logic, flow, and proper grammar,” Warmka recommends. “Conduct a reverse image search of the profile picture to determine whether it may be attributable to another identity. Conduct Google searches on information provided in this profile. Never connect with someone whose identity you cannot validate.”
Training for senior executives and employees can also be valuable. Warmka recommends that companies maintain frequent, required training for existing staff and new hires, including exercises on how to recognize and respond to social engineering attempts. Personal experiences, case studies, role playing, drills, and videos are all good training resources, and security can reinforce teaching points through periodic simulated social engineering tests or red teaming exercises. Business policies should be easy to understand, using real-life examples and references that connect with employees’ daily work. Avoid long, technical materials that don’t resonate with employees’ lives.
“Have social engineering as a regular topic of discussion,” Warmka says. “Ensure employees understand that protecting corporate data is a part of their job, even if they aren’t at work. Providing information on social media, over the phone, and face-to-face should all be done safely.”
He continues, “Encourage questions, sound judgment, and a fair dose of skepticism whenever employees are approached by someone who they don’t know, whether by email, social media message, text message, telephone call, or face-to-face interaction. Instill the concept ‘Verify, then Trust’ throughout the workforce.”
In addition to threats to sensitive data, reputations are also at risk when business executives take to social media or public-facing outlets without thinking twice.
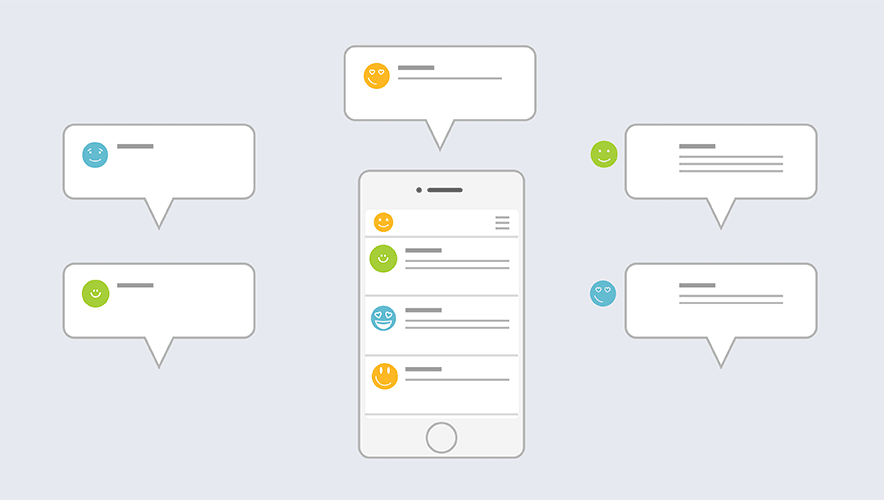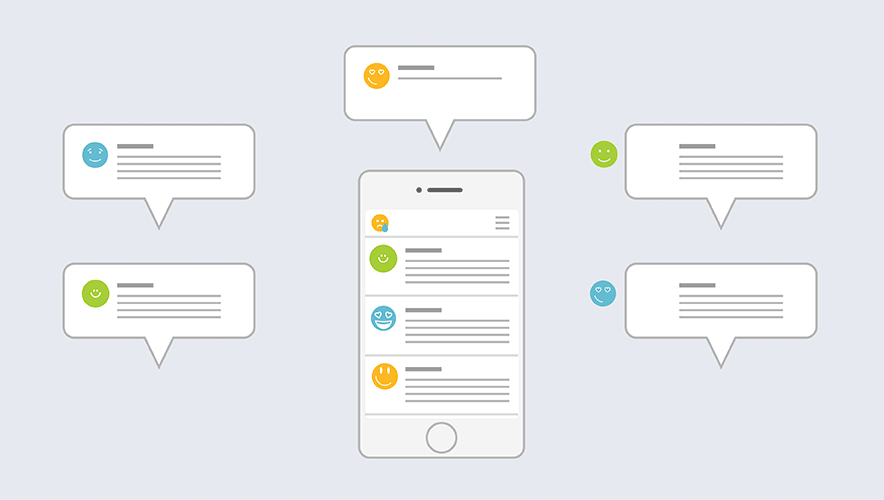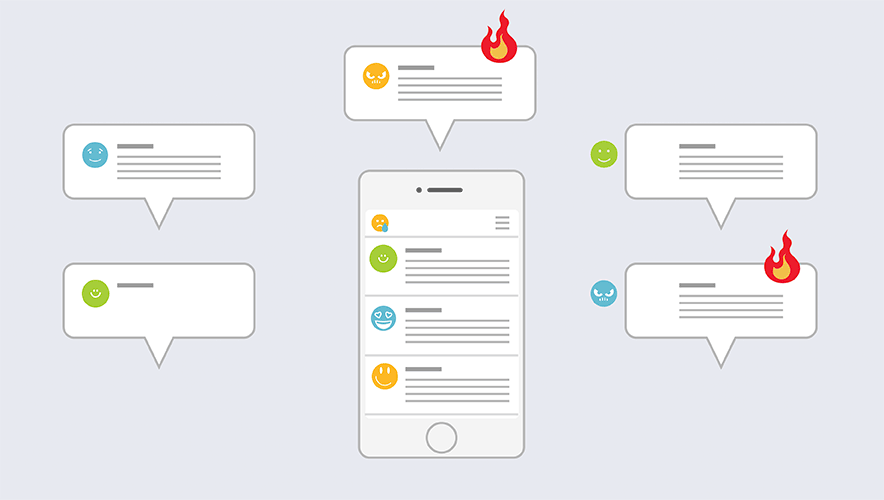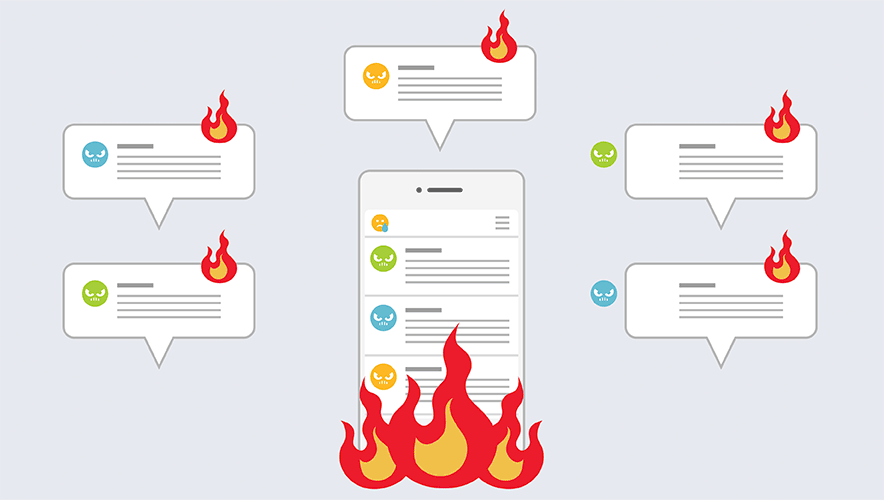
“On social media, public views may circulate swiftly,” Warmka says. “Bad publicity and comments have a significantly higher chance of becoming viral. As a result, businesses and individuals should be extremely cautious about their image on the Internet. Self-inflicted damage to reputation might include offensive posts or remarks, inaccurate product or service claims, and unethical online conduct. Unfavorable PR on social media can have major consequences if we aren’t paying attention to our online presence or don’t respond to negative criticism. Because of the influence of social media, a single bad occurrence may erase years of personal brand growth and all positivity in a split second.”
More than 23 million people engaged in some form of protest in the United States in 2020, according to Civis Analytics. A great many are likely corporate employees. Companies large and small have experienced the effects of employee activism, from walk-outs at Walmart to protest the chain’s gun sales to five percent of Coinbase’s staff quitting after the cryptocurrency firm attempted to stifle dialogue not related to the corporate mission.
Compared to before the COVID-19 pandemic, there has been a 40 percent increase in employee-led activism, and staffs are increasingly pressuring companies to take stances or action on political or social issues.
As Michael Center and Diana Concannon wrote in a July 2021 article for Security Management, “Reputational damage and loss of talent are two prominent threats posed by employee activism. But the strategy to mitigate them should not overshadow the opportunity to fortify an organizational culture of safety, engaging in the challenge of accepting diversity of opinion without generating animosity. Security professionals are positioned to play a key role in proactively assisting executives to manage employee activism in a manner that minimizes conflict and disruption.”
Preparing for the probability that employees will offend one another is a logical modern risk management strategy, especially with the rise of hyper-polarization. https://t.co/zTOYGHmywf
— Security Management (@SecMgmtMag) July 30, 2021
Warmka notes: “Managing employee activism is a new difficulty, but it’s an old type of conundrum: how to connect with wicked situations that can’t be readily handled and represent deeper conflicts which have to be held instead of solved. There may be a lot of ambiguity in the issues, and the final results of actions made may be unpredictable. Some people will inevitably believe they have lost as much as others have gained. Some people will believe that the group has not done enough, while some will be appalled by the actions committed.
“As a leader, it is your responsibility to do all possible to ensure that everyone feels heard and understands how and why decisions are made. There’s also a dilemma to face: although choices must be taken, staff must be aware that you’re maintaining an open mind. Leaders must be able to listen, act, and explain—and then repeat the process.
“Ignoring worker activists might be an indication that management is unable to hear anything that contradicts the predetermined agenda. Hearing differences and being interested are essential for creativity and agility, as well as for attracting and maintaining a new generation of talent who expects to be heard.”
Left unchecked, extreme beliefs can not only threaten cohesion and productivity, they can compromise safety and raise the risk of disruptive behaviors, even violence. https://t.co/a7KBjLCQzd
— Security Management (@SecMgmtMag) July 25, 2021
Beyond threats to networks or company assets, reputational risks can also bleed over into physical security risks. According to a study from the Ontic Center for Protective Intelligence, 24 percent of physical security and IT leaders said that in the first half of 2021 their CEO and/or family members received threats and/or were harmed when working from their private residence or while traveling as a result of intelligence failures.
“More than half of all respondents to the Center for Protective Intelligence survey said their CEO has received physical threats both as a result of either expressing (58 percent) or not expressing (40 percent) a position on racial and/or political issues,” wrote Fred Burton, executive director of the Ontic Center for Protective Intelligence, for Security Management.
As executives come further into the spotlight—both on social media and other public-facing outlets—their risk profile is likely to increase even more.
“We may be targeted if someone doesn’t like what we’re sharing and/or is trying to extort money or information from us,” Warmka says. “This is why it’s vital that your digital accounts are kept as secure as possible. We must ensure to use strict privacy settings on our online accounts and phone apps. We must be mindful of what we are posting and what information we are providing to people who are potentially a threat to us.
“If someone is planning a physical attack against us, providing information on social media regarding our pattern of life or future travel plans can make us more predictable and vulnerable,” he adds.