Dark Web Research Illuminates Threats to Energy Companies
Threat actors are using the Dark Web to auction off initial access to energy companies, according to a report from a Dark Web intelligence firm published Tuesday.
Searchlight Cyber, a firm specializing in scouring the Dark Web and providing intelligence to companies, released a report examining how cyber criminals try to profit from attacking companies in the energy sector.
The report, Dark Web Threats Against the Energy Industry: Building a Threat Model for Energy Companies, examined the Dark Web to study energy sector vulnerabilities that malicious hackers are trying to exploit.
The following example shows someone who has exploited an energy company’s system and is trying to sell that vulnerability on the Dark Web, together with Searchlight Cyber’s explanation of the listing parts:
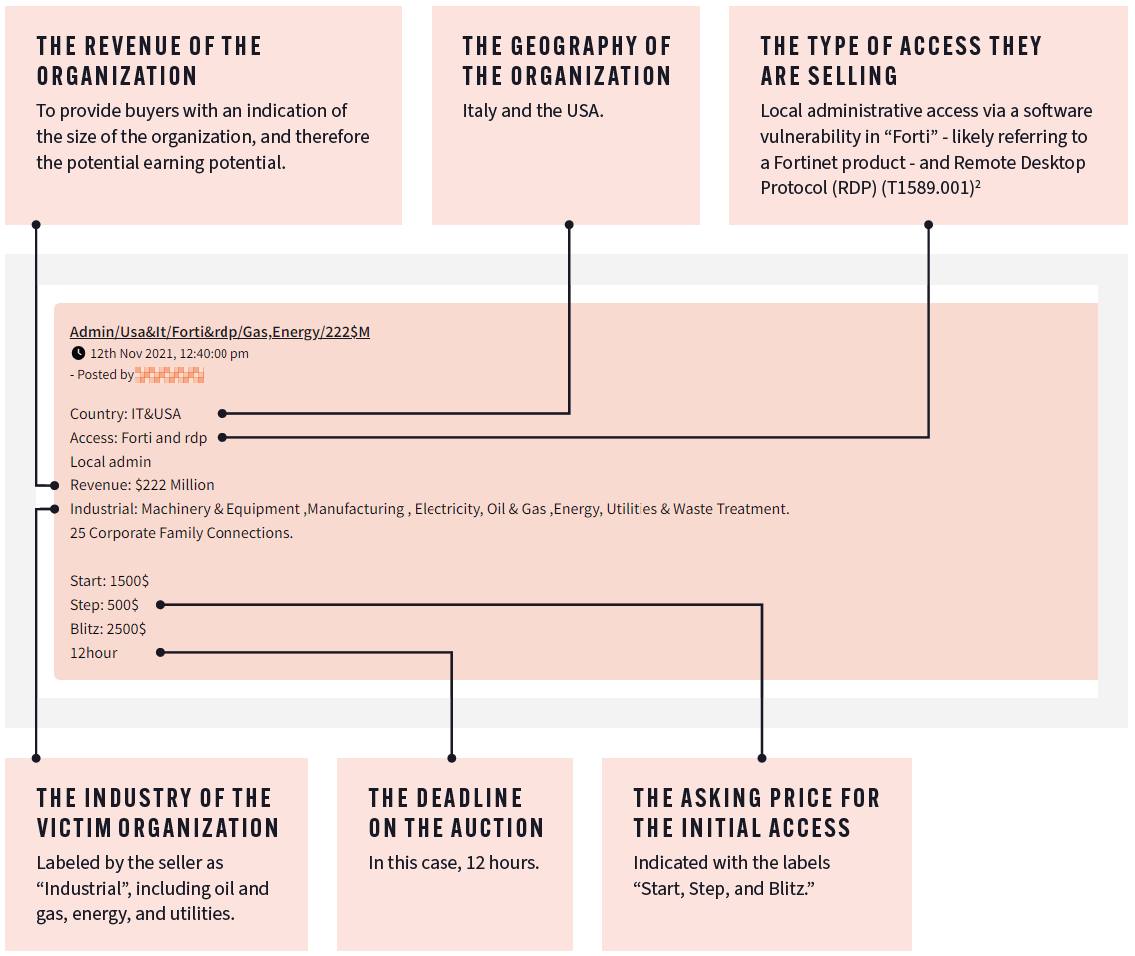
Reprinted with permission of Searchlight Cyber from their report: Dark Web Threats Against the Energy Industry.
The post is from a cyber criminal intermediary, or middleman. They are advertising that they have penetrated an energy company’s remote desktop protocol (RDP) and are auctioning off exclusive access to that vulnerability. Assuming the intermediary’s access works, a potential buyer would use the access to try to exploit other vulnerabilities and penetrate deeper into the company’s systems.
Note: The “Start, Step, Blitz” asking price section is auction shorthand. The auction is open for 12 hours and the bidding starts at $1,500. A new bid must go up one step, in this case $500. The blitz figure indicates that anyone can end the auction and purchase the access for $2,500.
“Initial access brokers’ role in the cybercriminal ecosystem is to facilitate other criminals in undertaking bigger attacks,” the report explained. “They operate at scale and are looking to make a quick, relatively risk-free profit from a large number of victims only by achieving access.”
The listing has several other parts that could be useful to energy companies that have the means to find the listings quickly. It includes the size of the company, its location, and sometimes technology that is involved in the exploitation.
“While cybercriminals share this information with the intention of attracting buyers, visibility into auction activity on Dark Web forums offers security professionals a valuable opportunity to determine if their organization is being targeted,” said Jim Simpson, director of threat intelligence at Searchlight Cyber, in the report. “With information on the revenue, location, and technology of the potential victim, security teams can identify if they fit the profile and take mitigative action. Even if they don’t fit the exact profile of the victim, they know this is a tactic being used against other energy companies that they should factor into their threat modeling.”
In fact, the report said, sometimes the listing actually names the company involved.
In addition to the auction activity, the Dark Web hosts a reversed criminal workflow as well. In this system, hackers post “in search of” announcements asking for remote desktop protocol (RDP) or virtual private network (VPN) access for certain sectors in specific regions.
As for the types of vulnerabilities, many of the examples in the report were selling compromised RDP credentials or VPN credentials. While it’s not known if access was purchased through a Dark Web intermediary, the infamous Colonial Pipeline ransomware attack used a compromised VPN.
Researchers also found ample evidence of cyber criminals working to compromise industrial control systems (ICSs) and operational technology. One example in the report showed a user freely sharing documentation on ICS and other industrial systems so others can more effectively hack systems.
“Access to ICS systems is undoubtedly the highest priority concern of security professionals at energy organizations, and I imagine many will be concerned to see this technology openly discussed on Dark Web forums,” said Ian Garratt, threat intelligence analyst at Searchlight Cyber, in the report. “It does, however, allow defenders to assess the capability of attackers with this information and monitor their evolution as credible threats overtime. This underlines the need to continuously monitor for evidence that their infrastructure—corporate or industrial—has been compromised. As the Colonial Pipeline demonstrated, even compromised corporate systems can be enough to bring operational activity to a halt.”
The report concludes with several recommendations for energy companies—recommendations just as applicable to other companies:
- Identify the assets adversaries are likely to target.
- Pivot off the targeted assets to identify areas of weakness and possible countermeasures.
- Establish who the adversaries that target the sector are; identify trends and techniques employed.
- Pivot off the adversaries to identify trigger events for attacks.
- Create an attack map based on the above information that visualizes the threat landscape in which the company operates.