Profile of a Ransomware Target
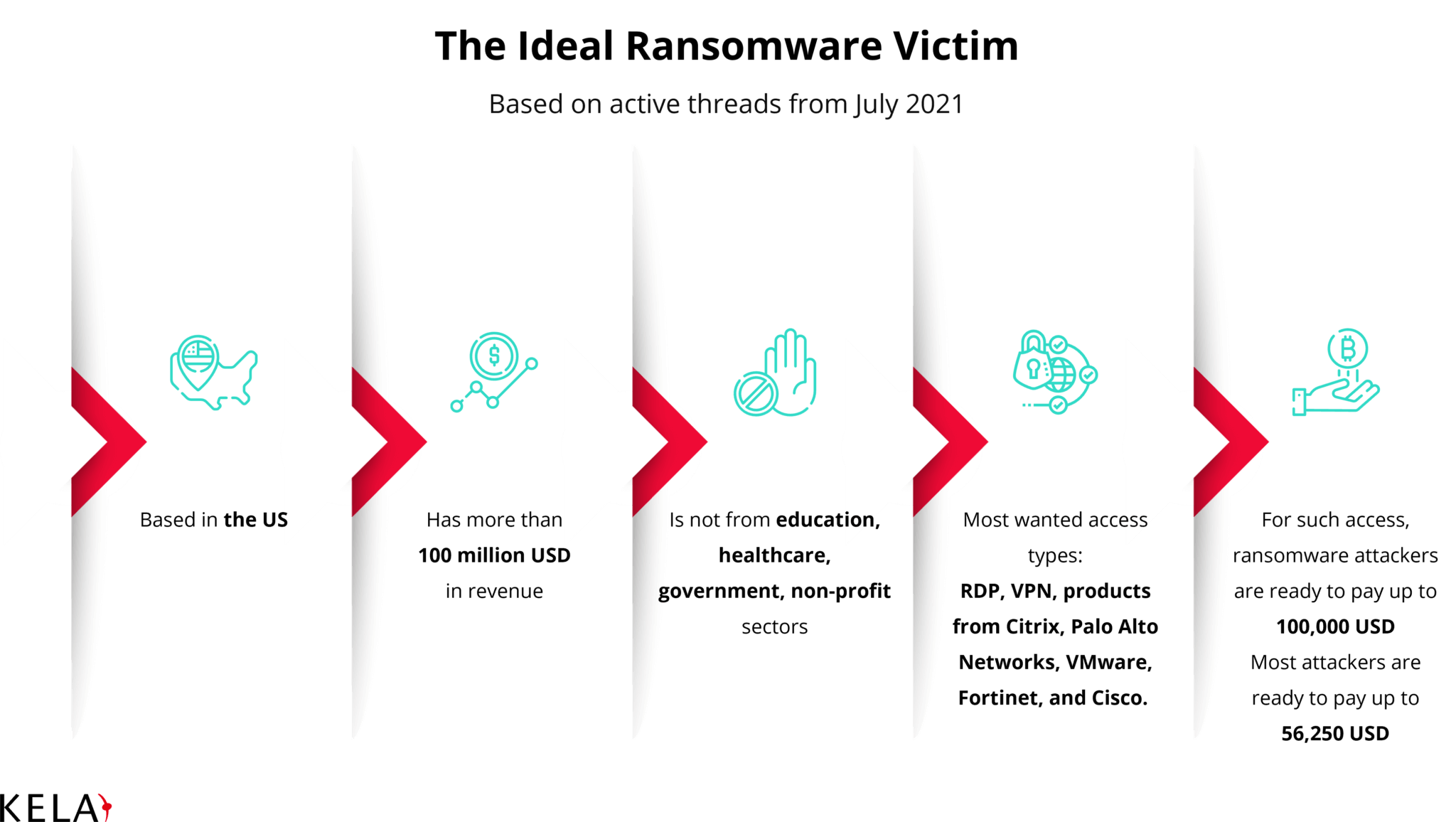
Researchers for the cybersecurity firm KELA jumped onto the Dark Web and built a profile of the ideal ransomware target from a cyber criminal’s perspective. It’s a company based in the United States—though Canada, Australia, and European countries also rate highly—that has at least $100 million in revenue, and is not in education, healthcare, government, or nonprofit sectors.
For different access types, and not necessarily types that would enable broad network intrusion, threat actors are willing to pay handsomely. KELA’s research turned up a range of $100 for initial access to $100,000. Categorized by type of access and the company’s desirability, the low category averaged $1,600 and the highest category averaged $56,250. In addition, many ransomware attackers routinely offer a share of collected ransoms to the initial access broker. Previous KELA research determined access brokers could collect approximately 10 percent of ransoms.
KELA’s research examined “in search of” advertisements from actors looking to use ransomware. It noticed that the advertisements often called for specific parameters, including geography, company size, and type of access, while excluding certain sectors.
The United States was requested in 47 percent of the advertisements studied; Canada and Australia (37 percent) followed, with 32 percent requesting European companies. Many ads specifically said they were not interested in Russian-speaking countries, South America, or third-world countries.
In terms of sectors, 47 percent of the ads blacklisted healthcare or education, 37 percent blacklisted the government sector, and 26 percent did not want access to nonprofit organizations.
“When actors prohibit healthcare or nonprofit industries offers, it is more likely due to the moral code of the actors,” the researchers explained. “When the education sector is off the table, the reason is the same or the fact that education victims simply cannot afford to pay much. Finally, when actors refuse to target government companies, it is a precaution measure and an attempt to avoid unwanted attention from law enforcement.”
The type of access being sought is not necessarily corporate network penetration. To be sure, domain administrator account access is highly prized—with a going rate 10 times more than other user access rights. The types of access sought include “multiple different vectors and entry points—from SQL injection and webshells to RDP- and VPN-based access.” In addition to initial network access, access requests include access to “online shops’ panels, unprotected databases, Microsoft Exchange servers, and more,” all of which the researchers described as “undoubtedly dangerous” but do not give threat actors a deep penetration into corporate networks.
“Therefore, researching the actors’ demands and their Dark Web activity, KELA determined that the actors behind the analyzed threads usually intended to exploit the access for all kinds of malicious activities, including information-stealing (from deploying info-stealing malware to injecting malicious scripts into websites), cryptocurrency mining, spam, and phishing campaigns,” the report said.
Access more Security Management content on cybersecurity.
